Microsoft Defender for Cloud - From Zero to Hero
Christopher Nett
4:52:09
Description
Learn Microsoft Defender for Cloud | Hands-on experience in your own free Azure environment | Elevate your cyber career
What You'll Learn?
- Overview on Defender for Cloud: Explore the features and capabilities of Microsoft Defender for Cloud for comprehensive cloud security
- SOC Basics: Gain insights into Security Operations Center (SOC) principles for effective threat management and incident response
- Azure Basics: Understand fundamental Azure concepts to establish a strong foundation for cloud security
- Azure Policy: Learn how to enforce governance policies using Azure Policy to ensure compliance and security
- Azure ARC: Discover the benefits of Azure Arc for extending Azure services and management to any infrastructure
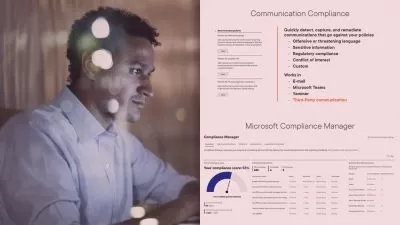
- CSPM (Cloud Security Posture Management): Implement CSPM to proactively manage and improve cloud security posture
- Foundational CSPM: Establish a solid foundation in Cloud Security Posture Management for robust security practices
- Defender CSPM: Leverage Defender CSPM for advanced cloud security posture management and threat detection
- Cloud Workload Protection: Secure cloud workloads effectively to safeguard critical applications and data
- Defender for Servers P1 and P2: Enhance server security with Microsoft Defender for Servers at both foundational and advanced levels
- Defender for App Service: Protect your applications with Defender for App Service for a resilient and secure app environment
- Defender for Databases: Safeguard databases against threats using Microsoft Defender for Databases
- Defender for Storage: Ensure the security of your storage solutions with Microsoft Defender for Storage
- Defender for Containers: Secure containerized environments with Microsoft Defender for Containers for enhanced container security
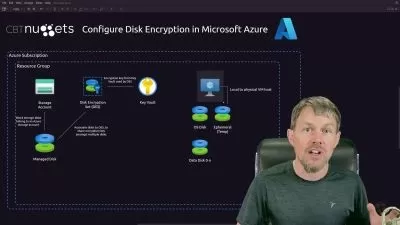
- Defender for Key Vault: Safely manage and protect cryptographic keys and secrets with Defender for Key Vault
- Defender for Resource Manager: Strengthen the security of Azure Resource Manager deployments with Defender
- Defender for APIs: Protect APIs from threats and vulnerabilities using Microsoft Defender for APIs
- Automation: Streamline security processes through automation to improve efficiency and responsiveness
- Integration with Sentinel: Seamlessly integrate with Microsoft Sentinel for enhanced security information and event management
- Integration with Defender for IoT: Enhance IoT security by integrating Microsoft Defender for IoT into your ecosystem
- Integration with Azure WAF: Bolster web application security with seamless integration with Azure Web Application Firewall
- Integration with Azure DDoS Protection Standard: Safeguard against DDoS attacks with integrated protection using Azure DDoS Protection Standard
- Azure Lighthouse: Explore the advantages of Azure Lighthouse for simplified management across multiple Azure environments
- Community: Join a vibrant community to share insights, best practices, and collaborate for ongoing learning and support
Who is this for?
What You Need to Know?
More details
DescriptionMicrosoft Defender for Cloud - From Zero to Hero, is a carefully curated Udemy course designed for IT professionals aspiring to excel in Microsoft Defender for Cloud, enhancing their capabilities in cloud security posture management and cloud workload protection. This comprehensive course guides you methodically from the initial configuration to advanced implementation, incorporating practical, real-world scenarios.
Acquiring expertise in Microsoft Defender for Cloud, formerly known as Azure Security Center, equips you with the skills to navigate a premier Cloud Native Application Protection Platform (CNAPP), essential in today's cybersecurity and cloud security landscape.
Key Benefits for you:
Overview on Defender for Cloud: Explore the features and capabilities of Microsoft Defender for Cloud for comprehensive cloud security.
SOC Basics: Gain insights into Security Operations Center (SOC) principles for effective threat management and incident response.
Azure Basics: Understand fundamental Azure concepts to establish a strong foundation for cloud security.
Azure Policy: Learn how to enforce governance policies using Azure Policy to ensure compliance and security.
Azure ARC: Discover the benefits of Azure Arc for extending Azure services and management to any infrastructure.
Azure Log Analytics: Harness the power of log analytics to gather actionable insights and enhance security monitoring.
CSPM (Cloud Security Posture Management): Implement CSPM to proactively manage and improve cloud security posture.
Foundational CSPM: Establish a solid foundation in Cloud Security Posture Management for robust security practices.
Defender CSPM: Leverage Defender CSPM for advanced cloud security posture management and threat detection.
Cloud Workload Protection: Secure cloud workloads effectively to safeguard critical applications and data.
Defender for Servers P1 and P2: Enhance server security with Microsoft Defender for Servers at both foundational and advanced levels.
Defender for App Service: Protect your applications with Defender for App Service for a resilient and secure app environment.
Defender for Databases: Safeguard databases against threats using Microsoft Defender for Databases.
Defender for Storage: Ensure the security of your storage solutions with Microsoft Defender for Storage.
Defender for Containers: Secure containerized environments with Microsoft Defender for Containers for enhanced container security.
Defender for Key Vault: Safely manage and protect cryptographic keys and secrets with Defender for Key Vault.
Defender for Resource Manager: Strengthen the security of Azure Resource Manager deployments with Defender.
Defender for APIs: Protect APIs from threats and vulnerabilities using Microsoft Defender for APIs.
Automation: Streamline security processes through automation to improve efficiency and responsiveness.
Integration with Sentinel: Seamlessly integrate with Microsoft Sentinel for enhanced security information and event management.
Integration with Defender for IoT: Enhance IoT security by integrating Microsoft Defender for IoT into your ecosystem.
Integration with Azure WAF: Bolster web application security with seamless integration with Azure Web Application Firewall.
Integration with Azure DDoS Protection Standard: Safeguard against DDoS attacks with integrated protection using Azure DDoS Protection Standard.
Azure Lighthouse: Explore the advantages of Azure Lighthouse for simplified management across multiple Azure environments.
Community: Join a vibrant community to share insights, best practices, and collaborate for ongoing learning and support.
Who this course is for:
- SOC Analyst
- Security Engineer
- Security Consultant
- Security Architect
- Security Manager
- Cloud Engineer
- Cloud Architect
- IT Manager
Microsoft Defender for Cloud - From Zero to Hero, is a carefully curated Udemy course designed for IT professionals aspiring to excel in Microsoft Defender for Cloud, enhancing their capabilities in cloud security posture management and cloud workload protection. This comprehensive course guides you methodically from the initial configuration to advanced implementation, incorporating practical, real-world scenarios.
Acquiring expertise in Microsoft Defender for Cloud, formerly known as Azure Security Center, equips you with the skills to navigate a premier Cloud Native Application Protection Platform (CNAPP), essential in today's cybersecurity and cloud security landscape.
Key Benefits for you:
Overview on Defender for Cloud: Explore the features and capabilities of Microsoft Defender for Cloud for comprehensive cloud security.
SOC Basics: Gain insights into Security Operations Center (SOC) principles for effective threat management and incident response.
Azure Basics: Understand fundamental Azure concepts to establish a strong foundation for cloud security.
Azure Policy: Learn how to enforce governance policies using Azure Policy to ensure compliance and security.
Azure ARC: Discover the benefits of Azure Arc for extending Azure services and management to any infrastructure.
Azure Log Analytics: Harness the power of log analytics to gather actionable insights and enhance security monitoring.
CSPM (Cloud Security Posture Management): Implement CSPM to proactively manage and improve cloud security posture.
Foundational CSPM: Establish a solid foundation in Cloud Security Posture Management for robust security practices.
Defender CSPM: Leverage Defender CSPM for advanced cloud security posture management and threat detection.
Cloud Workload Protection: Secure cloud workloads effectively to safeguard critical applications and data.
Defender for Servers P1 and P2: Enhance server security with Microsoft Defender for Servers at both foundational and advanced levels.
Defender for App Service: Protect your applications with Defender for App Service for a resilient and secure app environment.
Defender for Databases: Safeguard databases against threats using Microsoft Defender for Databases.
Defender for Storage: Ensure the security of your storage solutions with Microsoft Defender for Storage.
Defender for Containers: Secure containerized environments with Microsoft Defender for Containers for enhanced container security.
Defender for Key Vault: Safely manage and protect cryptographic keys and secrets with Defender for Key Vault.
Defender for Resource Manager: Strengthen the security of Azure Resource Manager deployments with Defender.
Defender for APIs: Protect APIs from threats and vulnerabilities using Microsoft Defender for APIs.
Automation: Streamline security processes through automation to improve efficiency and responsiveness.
Integration with Sentinel: Seamlessly integrate with Microsoft Sentinel for enhanced security information and event management.
Integration with Defender for IoT: Enhance IoT security by integrating Microsoft Defender for IoT into your ecosystem.
Integration with Azure WAF: Bolster web application security with seamless integration with Azure Web Application Firewall.
Integration with Azure DDoS Protection Standard: Safeguard against DDoS attacks with integrated protection using Azure DDoS Protection Standard.
Azure Lighthouse: Explore the advantages of Azure Lighthouse for simplified management across multiple Azure environments.
Community: Join a vibrant community to share insights, best practices, and collaborate for ongoing learning and support.
Who this course is for:
- SOC Analyst
- Security Engineer
- Security Consultant
- Security Architect
- Security Manager
- Cloud Engineer
- Cloud Architect
- IT Manager
User Reviews
Rating
Christopher Nett
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 120
- duration 4:52:09
- Release Date 2024/03/12