Metasploit Essential Training
Liam Cleary
4:00:30
Description
As a security or IT professional, you need to know how to check security within your environment, and one of the most commonly used tools available is Metasploit. It lets you conduct basic security checks, full assessments, and penetration testing so you can avoid becoming the target of an attack. Join instructor Liam Cleary to learn how and why you should add Metasploit to your cybersecurity testing toolkit and explore the skills you need to know to get up and running fast.
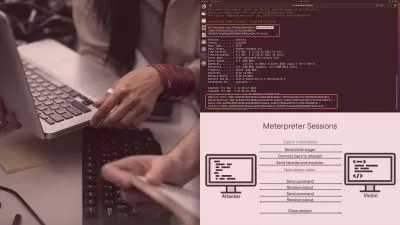
Become more proficient with information gathering, vulnerability scanning, and client-side and post-exploitation using Linux, Windows, and Meterpreter as well as other networking tools such as msfvenom and Mimikatz. By the end of this course, you’ll be equipped with new skills in security and network management to better protect yourself and your organization from potential vulnerabilities.
More details
User Reviews
Rating
Liam Cleary
Instructor's Courses
Linkedin Learning
View courses Linkedin Learning- language english
- Training sessions 39
- duration 4:00:30
- Release Date 2023/03/01