Mastering Cybercrime Defense & Digital Security
Diwakar Thakore
3:34:36
Description
The Essential Guide to Safeguarding Yourself, Your Family, and Your Business Online
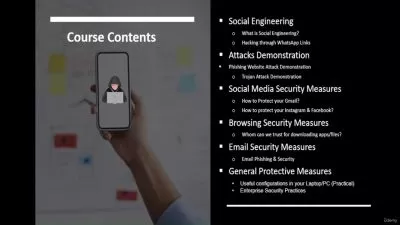
What You'll Learn?
- Define cybercrime and its impact on individuals and organizations.
- Analyze notable cybercrime incidents and their consequences.
- Evaluate different cybercrime threats, classifications, and actors.
- Assess comprehension of cybercrime classifications and threat actors.
- Explain the role of human behavior in cybercrime.
- Examine cybercrime incidents driven by human vulnerabilities.
- Analyze psychological principles behind social engineering attacks
- Implement strategies to defend against social engineering attacks
- Develop response plans for different social engineering scenarios.
- Understand how online behavior impacts security.
- Investigate security breaches resulting from poor online practices.
- Understand the various types of cyber-attacks and their implications.
- Differentiate between various types of cybercriminals and their motivations.
- Recognize different forms of malware and their functionalities
- Understand the importance of basic security measures.
- Implement key security practices such as updating systems and installing security software.
- Recognize and address vulnerabilities related to social engineering.
- Set up multi-factor authentication for various accounts.
- Apply guidelines for secure usage of personal devices
- Implement best practices for secure email and internet usage.
- Implement preventive measures to mitigate cyber threats.
- Develop a cybersecurity action plan for personal or organizational use.
Who is this for?
What You Need to Know?
More details
Description'Essential Guide to Safeguarding Yourself, Your Family, and Your Business Online: Navigate the Digital Jungle Safely'
In an increasingly interconnected world, the importance of cybersecurity literacy cannot be overstated.
Whether you're a student, a professional, a homemaker, a small business owner, or a corporate employee, protecting yourself, your loved ones, and your business from online threats is paramount.
That's why we've designed "Mastering Cybercrime Defense & Digital Security" - a comprehensive program that equips you with the knowledge and skills to navigate the digital landscape with confidence and security.
This program goes beyond mere awareness of cyber threats; it empowers you to take proactive measures to safeguard your digital presence effectively.
From understanding the various forms of cybercrime to implementing robust cybersecurity practices, each module is crafted to provide practical insights and actionable strategies that you can immediately apply in your daily life.
Through engaging lectures, interactive case studies, active storytelling, practical exercises, and scenario analyses, you'll learn how to recognize and mitigate common cyber threats, secure your personal devices and networks, protect your sensitive information, and respond effectively to cyber incidents.
Whether you're learning for personal enrichment or professional advancement, this program offers valuable insights and resources tailored to your needs.
Join us on this journey to digital safety and empowerment.
Together, let's navigate the digital jungle safely and ensure a secure online environment for ourselves, our families, and our businesses.
Who this course is for:
- This program is for anyone who wants to be a Smart Digital Citizen.
- This course is for anyone who wants to protect him/her self, his/her family, occupation and society from cybercrime and similar nefarious activities.
- This course is for anyone who is interested in knowing the ways of the cybercrime and cybercriminals, and be one step ahead.
'Essential Guide to Safeguarding Yourself, Your Family, and Your Business Online: Navigate the Digital Jungle Safely'
In an increasingly interconnected world, the importance of cybersecurity literacy cannot be overstated.
Whether you're a student, a professional, a homemaker, a small business owner, or a corporate employee, protecting yourself, your loved ones, and your business from online threats is paramount.
That's why we've designed "Mastering Cybercrime Defense & Digital Security" - a comprehensive program that equips you with the knowledge and skills to navigate the digital landscape with confidence and security.
This program goes beyond mere awareness of cyber threats; it empowers you to take proactive measures to safeguard your digital presence effectively.
From understanding the various forms of cybercrime to implementing robust cybersecurity practices, each module is crafted to provide practical insights and actionable strategies that you can immediately apply in your daily life.
Through engaging lectures, interactive case studies, active storytelling, practical exercises, and scenario analyses, you'll learn how to recognize and mitigate common cyber threats, secure your personal devices and networks, protect your sensitive information, and respond effectively to cyber incidents.
Whether you're learning for personal enrichment or professional advancement, this program offers valuable insights and resources tailored to your needs.
Join us on this journey to digital safety and empowerment.
Together, let's navigate the digital jungle safely and ensure a secure online environment for ourselves, our families, and our businesses.
Who this course is for:
- This program is for anyone who wants to be a Smart Digital Citizen.
- This course is for anyone who wants to protect him/her self, his/her family, occupation and society from cybercrime and similar nefarious activities.
- This course is for anyone who is interested in knowing the ways of the cybercrime and cybercriminals, and be one step ahead.
User Reviews
Rating
Diwakar Thakore
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 22
- duration 3:34:36
- Release Date 2024/06/19