LPI Security Essentials (020-100) Complete Course & Exam
Jason Dion • 1 Million+ Enrollments Worldwide,Dion Training Solutions • ATO for ITIL & PRINCE2,Dion Training Solutions • ATO for ITIL & PRINCE2,Kip Boyle
17:29:31
Description
Pass the LPI Security Essentials (020-100) exam on your 1st attempt, includes a full-length practice exam!
What You'll Learn?
- Passing the LPI Security Essentials certification exam with confidence
- Avoid common security threats of using computers, networks, connected devices, and IT services on premises and in the cloud
- Implement common ways to prevent and mitigate attacks against their personal devices and data
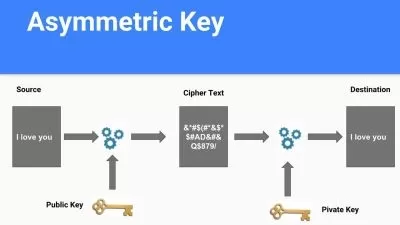
- Utilize encryption to secure data transferred through a network and stored on storage devices and in the cloud
- Apply common security best practices, protect private information, and secure their identity
- Securely use IT services and to take responsibility for securing their personal computing devices, applications, accounts, and online profiles
Who is this for?
What You Need to Know?
More details
Description** Taught by a Best Selling IT Certification Instructor **
Taught by an expert in information technology and cybersecurity with over 20 years of experience, this course is a fun way to master the fundamentals of cloud computing.
My name is Jason Dion, and I have personally helped over 1,000,000 students earn their IT certifications, and now I can help you, too!
Along with my co-instructor, Kip Boyle, we are going to teach you the fundamentals of cybersecurity and how to stay safe while online!
In today's digital age, IT security is vital for both individuals and organizations. Protecting data, devices, and networks is crucial in responsible information technology use. The Linux Professional Institute Security Essentials certificate provides an opportunity to learn and demonstrate expertise in the field. The exam covers essential IT security fields, making it suitable for students, staff, and organizations seeking to improve their security. It's also ideal for individuals looking to gain basic competence in secure information technology use.
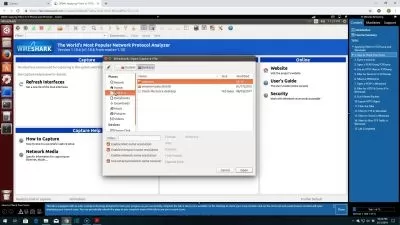
In this course, you will get access to all of our lessons, lectures, and video demonstrations to teach you everything you need to know to pass the LPIÂ Security Essentials exam.
LPIÂ Security Essentials (020-100) is the best way to gain a fundamental understanding of cybersecurity and is designed for both IT and non-technical professionals who need to make informed security choices while using the Internet so they don't fall victim to cyber attacks and data breaches.
This course is designed to help prepare you for the LPI Security Essentials (020-100) certification exam and covers all five domains of the LPI Security Essentials (020-100)certification exam:
Security Concepts (12.5%)
Encryption (22.5%)
Device and Storage Security (22.5%)
Network and Service Security (25%)
Identity and Privacy (17.5%)
What You Will Receive In The Course:
Video lectures with the essential information needed to pass the LPIÂ Security Essentials (020-100) exam
A complete downloadable study guide in PDF format based on the lessons
Practice quizzes to ensure mastery of each section of the course
A full-length practice exam with multiple choice and mock simulations
This course stays current and up-to-date with the latest release of the LPI Security Essentials exam (020-100), and also provides a 30-day money-back guarantee if you are not satisfied with the quality of this course for any reason!
What Other Students Are Saying About Our Other Certification Courses:
I passed the Security+ exam. This course was absolutely essential to passing that exam. Only the Dion Security+ covered the topics comprehensively and thoroughly enough. No other resource I used came close. (Kolya, 5 stars)
I have just completed watching two different instructor courses on the same subject. I must say, Dion's has more information in a better constructed manner. This course is not easy, it is heavy with information and having you sit through shorter videos was the best part. Having watched more than just Dion's, I can say he goes over the content much better. Very glad I chose to watch a second course! (Rutger, 5 stars)
I love taking this wonderful course. It's full of important tips and amazing steps in order to pass CompTIA Security+. Thank you, Jason Dion, for making this incredible course! (Paul, 5 stars)
Upon completion of this course, you will earn 12 CEUs towards the renewal of your CompTIA A+, Network+, Security+, Linux+, Cloud+, PenTest+, CySA+, or CASP+ certifications.
Who this course is for:
- Students wanting to pass the LPI Security Essentials certification exam
- Students seeking a more secure online experience
- Students seeking to maximize their privacy when browsing the web
- Students wanting to get a basic understanding of cybersecurity
** Taught by a Best Selling IT Certification Instructor **
Taught by an expert in information technology and cybersecurity with over 20 years of experience, this course is a fun way to master the fundamentals of cloud computing.
My name is Jason Dion, and I have personally helped over 1,000,000 students earn their IT certifications, and now I can help you, too!
Along with my co-instructor, Kip Boyle, we are going to teach you the fundamentals of cybersecurity and how to stay safe while online!
In today's digital age, IT security is vital for both individuals and organizations. Protecting data, devices, and networks is crucial in responsible information technology use. The Linux Professional Institute Security Essentials certificate provides an opportunity to learn and demonstrate expertise in the field. The exam covers essential IT security fields, making it suitable for students, staff, and organizations seeking to improve their security. It's also ideal for individuals looking to gain basic competence in secure information technology use.
In this course, you will get access to all of our lessons, lectures, and video demonstrations to teach you everything you need to know to pass the LPIÂ Security Essentials exam.
LPIÂ Security Essentials (020-100) is the best way to gain a fundamental understanding of cybersecurity and is designed for both IT and non-technical professionals who need to make informed security choices while using the Internet so they don't fall victim to cyber attacks and data breaches.
This course is designed to help prepare you for the LPI Security Essentials (020-100) certification exam and covers all five domains of the LPI Security Essentials (020-100)certification exam:
Security Concepts (12.5%)
Encryption (22.5%)
Device and Storage Security (22.5%)
Network and Service Security (25%)
Identity and Privacy (17.5%)
What You Will Receive In The Course:
Video lectures with the essential information needed to pass the LPIÂ Security Essentials (020-100) exam
A complete downloadable study guide in PDF format based on the lessons
Practice quizzes to ensure mastery of each section of the course
A full-length practice exam with multiple choice and mock simulations
This course stays current and up-to-date with the latest release of the LPI Security Essentials exam (020-100), and also provides a 30-day money-back guarantee if you are not satisfied with the quality of this course for any reason!
What Other Students Are Saying About Our Other Certification Courses:
I passed the Security+ exam. This course was absolutely essential to passing that exam. Only the Dion Security+ covered the topics comprehensively and thoroughly enough. No other resource I used came close. (Kolya, 5 stars)
I have just completed watching two different instructor courses on the same subject. I must say, Dion's has more information in a better constructed manner. This course is not easy, it is heavy with information and having you sit through shorter videos was the best part. Having watched more than just Dion's, I can say he goes over the content much better. Very glad I chose to watch a second course! (Rutger, 5 stars)
I love taking this wonderful course. It's full of important tips and amazing steps in order to pass CompTIA Security+. Thank you, Jason Dion, for making this incredible course! (Paul, 5 stars)
Upon completion of this course, you will earn 12 CEUs towards the renewal of your CompTIA A+, Network+, Security+, Linux+, Cloud+, PenTest+, CySA+, or CASP+ certifications.
Who this course is for:
- Students wanting to pass the LPI Security Essentials certification exam
- Students seeking a more secure online experience
- Students seeking to maximize their privacy when browsing the web
- Students wanting to get a basic understanding of cybersecurity
User Reviews
Rating
Jason Dion • 1 Million+ Enrollments Worldwide
Instructor's CoursesDion Training Solutions • ATO for ITIL & PRINCE2
Instructor's CoursesDion Training Solutions • ATO for ITIL & PRINCE2
Instructor's CoursesKip Boyle
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 157
- duration 17:29:31
- English subtitles has
- Release Date 2023/06/16