Linux Administration: The Complete Linux Training Course
The Linux Lighthouse
25:39:25
Description
The TOP Linux Administration & Linux Command Line Course That Teaches You All About Linux & Prepares You For IT Jobs
What You'll Learn?
- By the end of this course you will be a professional in Linux administration and be able to apply for Linux jobs
- You will have solid Linux skills and have great understanding of Linux concepts and fundamentals
- You will master all of the important Linux commands
- Acquire the technical expertise to work on the Linux command line
- You will be able to troubleshoot day-to-day Linux related issues
- You will gain advance Linux systems administration skills
- You will gain knowledge of the most used Linux commands
- Become an Independent User of the Linux Operating System
- Feel comfortable using the command line interface
- CentOS/Redhat versions 7, 8 and 9 and Rocky 8 and 9
Who is this for?
What You Need to Know?
More details
DescriptionWELCOME !    Â
Welcome to the Linux Administration: The Complete Linux Training Course, the one course you need to learn all about Linux Administration, Linux Command Line and Linux in general to start your career in IT.
The Linux operating system is the most preferred operating system in the corporate world and the great thing about Linux is that most of what you'll need to learn isn't very difficult at all. Linux is a key skill of IT, it provides good career opportunities with higher salaries, it's a free operating system and by learning Linux, you can use this Linux knowledge and apply it to roles like Linux System Administrator, DevOps Engineer, Cloud Architect, Network Administrator, Security Engineer, Backend Developer, Frontend Developer, Data Scientist, and much more. So if you want to learn Linux and be able to apply it in any of the roles mentioned above, then this course is for you !
Course's Aim ?
This course will teach you the Linux skills that will enable you to start your career in IT in any Linux based or related job and to provide you with all you need to apply for the job as a professional in Linux. After this course you won't be needing any other to start your career and that's because this course is designed to cover all the Linux aspects needed for you to start your career in IT.
Who are we?
We are M Torkey and M Khalil and we have been working with Linux for over a decade, along the years we've worked in so many companies as Sys Admins and DevOps Engineers and we have been given the opportunity to learn from experts and developed a lot of skills in the work field and henceforth we would present for you what you exactly need to skyrocket your chances of landing a job in IT and starting your career.
In this course you'll learn the key commands, concepts and overall Linux skills that will help get you started in your journey.
Why Linux ?
Linux tends to be highly reliable and a more secure system than any other operating system (OS). Linux also is quite popular among many corporates and many consider it to be the lead operating system in the corporate world. Here are 5 reasons why you should start in Linux:
Linux Provides Good Career Opportunities
Much of the infrastructure that powers the internet, including routers and servers, is based on Linux
Linux is Used on Nearly Every Server
Linux is one such skill that allows an individual to experience a widespread growth in their profile after learning it
Linux is free and open source
What will be presented in this course ?
The course is aimed to teach Linux to beginners, intermediates and even advanced Linux users who wish to develop their skills in Linux. Starting all the way from the Linux basics up to how to manage an entire platform.
This is the list of topics that I will cover in this course:
Section 1 - Introduction
Welcome !
What is Linux ?
Why Linux ?
Section 2 - Prepare Your Lab
Install VirtualBox on Windows
Create our first virtual machine
Add New Virtual Hard Disk
Why Rocky Linux ? and it's relation to centOS and RedHat
Install Rocky 9.0 (Redhat & CentOS compatible)
Port Forwarding - NAT - Network issue solution
Section 3 - Understand & Use Essential Tools
Accessing the Command Line
Linux File System Hierarchy
Create Files & Directories
Find Your Way In Linux
Copy, Move, Rename & Delete Files
Copy, Move, Rename & Delete Directories
Get Help with Manual Pages
Get Help with Pinfo
Read Linux Documentation
Use Input & Output redirection
Create & Edit Text Files
Access Remote Systems Using SSH
Archive, Compress, Unpack & Uncompress Files
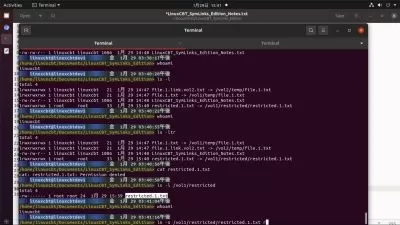
Create Hard & Soft Links
Finding Files
Section 4 - Linux System Administration (Chapter 1)
Create Local Users & Local Groups
Gain Super Powers
Modify Users, Groups & Password Aging
Configure A System To Use An Existing Authentication Service
Notation Permissions
Symbolic Permissions
Special Permissions
Section 5 - Linux System Administration (Chapter 2)
Monitor Running Processes with ps Command
Run Processes in the Background
Terminate Running Processes with Kill & Pkill
Monitoring Running System with top
Listing Unit Files with systemctl
Start, Stop & Check The status of a Linux Service
The Truth About System Log
The rsyslog
The SystemD Journal
Boot, Reboot And Shut Down A System Normally
Boot Systems Into Different Targets Manually
Interrupt The Boot Process To Gain Access To A System
Adjust Process Priority With Renice
Section 6 - Linux System Administration (Chapter 3)
Examining the File System
Mounting & Unmounting File System
Create, Mount, Unmount And Use Vfat, ext4 And xfs File Systems
Mount and Unmount CIFS and NFS Network File Systems
Extend Existing Logical Volume
Create and manage Access Control Lists ACLs
Maintain Accurate Time with ntp
Validate Your Network Configuration
Configure Linux Network
Edit Network Configuration Files
Configuring Hostnames & Names Resolution
Install & Update Software with yum
Manage RPM Packages
Schedule Tasks Using at and cron
Section 7 - Linux System Administration (Chapter 4)
Configure Key-Based Authentication for SSH
Disallow User Root from Logging In Using SSH
Copying Files Securely Between Systems
Synchronize Files & Folders Securely Between Systems
Configure Firewall Settings Using Firewall-config & Firewall-cmd
Introduction To SElinux
List And Identify SElinux File And Process Context
Restore Default File Contexts
Use Boolean Settings To Modify System SElinux
Diagnose And Address Routine SElinux Policy Violation
Section 8 - Linux System Administration (Chapter 5)
Configure Aggregated Network Links Between 2 RHEL Systems or Interfaces
Configure IPv6 Addresses and Perform Basic IPv6 Troubleshooting
Firewalld - The rich rules
Configure Network Address Translation(NAT) - Masquerade
Configure Network Address Translation (NAT) - Port forwarding
Configure a system as an iSCSI target
Configure a system as an iSCSI initiator
Use procsys and sysctl to Modify or Set Kernel runtime parameters
Produce and deliver reports on system utilization(processor,memory,disk,network)
Section 9 - Linux System Administration (Advanced Topics)
Install the packages needed to provide the service
Configure SELinux to support the service
Use SELinux port labelling to allow services to use non-standard ports
Configure the service to start when the system is booted
Install and Configure Apache
Configure Apache access restrictions on directories
Configure Group Managed Content
Deploy a basic CGI application
Configure an Apache Virtual Host
Configure TLS security
The Apache Configuration File
Configure a Caching-Only Name Server
Provide network shares to specific clients
Provide network shares suitable for group collaboration
Use Kerberos to Control Access to NFS network shares (configure Kerberos)
Use Kerberos to Control Access to NFS network shares ( Configure Nfs Server )
Provide Network Shares to Specific Clients-client installation and configuration
Provide Network Shares Suitable for Group Collaboration
Configure a system to forward all emails to a central mail server
Configure Key-Based Authentication
Configure Key-Based Authentication 2
Synchronize time using other NTP peers
Install and Configure MariaDB
Create a simple database schema
Backup database
Perform simple SQL queries against a database
Restore a MariaDB database
Section 10 - Bonus 1: Secure Shell Deep Dive
Introduction To Secure Shell
How do I connect to a remote host
How do I connect to a remote host on a different SSH port
How can I login to a specific directory?
How do I execute a command on a remote host using SSH?
How can I copy (file/files) to a remote host using SCP?
How can I copy (file/files) from a remote host using SCP?
How can I Copy entire directory using SCP?
Can I limit the speed (bandwidth) of files transfer using SCP?
What is SFTP and how to connect to SFTP?
SFTP List file and check the working directory
SFTP Uploading Files
SFTP Downloading Files
SFTP Switching and Creating Directories
SFTP Remove Files and Directories
Multiple SSH Sessions with screen (Install Screen)
Multiple SSH Sessions with screen (Start working)
Multiple SSH Sessions with screen Lock and Exit from the screen
Tunneling x11 Through SSH (Linux)
Tunneling x11 Through SSH (Run Linux Applications on Windows)
Remote Desktop with SSH (Install and Configure VNC Server)
Remote Desktop with SSH (Connect to Remote Desktop)
Change The Default Port
Disable Direct Root Access
Allow Access for Certain User(s)
Deny Access from Known IPs
Allow Access from Known IPs
Public Key Authentication
Disable Password Authentication
Section 11 - Bonus 2: Additional Lectures
Vi editor part 1
Vi editor part 2
Create SWAP file and SWAP partition
Logical Volume Management (LVM)
Software RAID
Process Managment
VMSTAT And IOSTAT
List Open Files (LSOF)
Tcpdump
Search for Files on Linux using find and locate
Cat Command
Grep Command
AWK Command
HEAD Command
Network Clients (ssh , Scp , Ftp ,wget)
With that there will be 24 hour support for any questions or suggestions in the discussion forumÂ
And now after this description you must be concerned on what are you going to get out of this course by the end !Â
By the end of this course you will have the skills that will qualify you to apply for any Linux related job and be able to preform in real life situations. Â
==========================================================================================
For Assurance, check out what my students actually have to say about the course:
"I've taken dozens of courses on Udemy with some really great content, but this if you only take one course, this is the one to take. thank you.!!!" - Edward W. (5 Star Review)
"Five Star All The Way!!! Thanks guys you are the best on Udemy! Well explained course and easy to understand in a reasonable time. After completing the first section I am confident that this course will provide everything I had hoped for and more" - canning G. (5 Star Review)
"Thank you very much for the course! I look forward to seeing more lectures, he did not waste a word. Buy this course if you want to succeed. Very understandable!!!" - Kaichekanchap (5 Star Review)
                      Â
"Awesome dude!! great stuff, highly recommend. Simply Five Star. Thank you for showing us this innovative knowledge. It was extremely well educative" - Uppalakiran (5 Star Review)
"Simple and straightforward!!!!!! Wish I'd had access to a class like this years ago. The instructor are always here to help out, never had a problem to contact him regarding to the question in the course" - Sairepavan (5 Star Review)
"I have got more information about Linux, I would strongly recommend this course to all new professionals starting their career as a Linux administrator" - Abhishek Kumar P. (5 Star Review)
"Great job!!! Best course on udemy. Simple and sweet description. Anyone who want to learn linux can go through it. It gave me exactly what I was looking for" - Nervinara (5 Star Review)
Who this course is for:
- Anyone who would like to learn Linux and seek a job in Linux.
- Anyone interested in starting a career in Linux
- Anyone who wants to learn how to use the Linux command line and master the skill
- Anyone who wants to become a Linux system administrator
WELCOME !    Â
Welcome to the Linux Administration: The Complete Linux Training Course, the one course you need to learn all about Linux Administration, Linux Command Line and Linux in general to start your career in IT.
The Linux operating system is the most preferred operating system in the corporate world and the great thing about Linux is that most of what you'll need to learn isn't very difficult at all. Linux is a key skill of IT, it provides good career opportunities with higher salaries, it's a free operating system and by learning Linux, you can use this Linux knowledge and apply it to roles like Linux System Administrator, DevOps Engineer, Cloud Architect, Network Administrator, Security Engineer, Backend Developer, Frontend Developer, Data Scientist, and much more. So if you want to learn Linux and be able to apply it in any of the roles mentioned above, then this course is for you !
Course's Aim ?
This course will teach you the Linux skills that will enable you to start your career in IT in any Linux based or related job and to provide you with all you need to apply for the job as a professional in Linux. After this course you won't be needing any other to start your career and that's because this course is designed to cover all the Linux aspects needed for you to start your career in IT.
Who are we?
We are M Torkey and M Khalil and we have been working with Linux for over a decade, along the years we've worked in so many companies as Sys Admins and DevOps Engineers and we have been given the opportunity to learn from experts and developed a lot of skills in the work field and henceforth we would present for you what you exactly need to skyrocket your chances of landing a job in IT and starting your career.
In this course you'll learn the key commands, concepts and overall Linux skills that will help get you started in your journey.
Why Linux ?
Linux tends to be highly reliable and a more secure system than any other operating system (OS). Linux also is quite popular among many corporates and many consider it to be the lead operating system in the corporate world. Here are 5 reasons why you should start in Linux:
Linux Provides Good Career Opportunities
Much of the infrastructure that powers the internet, including routers and servers, is based on Linux
Linux is Used on Nearly Every Server
Linux is one such skill that allows an individual to experience a widespread growth in their profile after learning it
Linux is free and open source
What will be presented in this course ?
The course is aimed to teach Linux to beginners, intermediates and even advanced Linux users who wish to develop their skills in Linux. Starting all the way from the Linux basics up to how to manage an entire platform.
This is the list of topics that I will cover in this course:
Section 1 - Introduction
Welcome !
What is Linux ?
Why Linux ?
Section 2 - Prepare Your Lab
Install VirtualBox on Windows
Create our first virtual machine
Add New Virtual Hard Disk
Why Rocky Linux ? and it's relation to centOS and RedHat
Install Rocky 9.0 (Redhat & CentOS compatible)
Port Forwarding - NAT - Network issue solution
Section 3 - Understand & Use Essential Tools
Accessing the Command Line
Linux File System Hierarchy
Create Files & Directories
Find Your Way In Linux
Copy, Move, Rename & Delete Files
Copy, Move, Rename & Delete Directories
Get Help with Manual Pages
Get Help with Pinfo
Read Linux Documentation
Use Input & Output redirection
Create & Edit Text Files
Access Remote Systems Using SSH
Archive, Compress, Unpack & Uncompress Files
Create Hard & Soft Links
Finding Files
Section 4 - Linux System Administration (Chapter 1)
Create Local Users & Local Groups
Gain Super Powers
Modify Users, Groups & Password Aging
Configure A System To Use An Existing Authentication Service
Notation Permissions
Symbolic Permissions
Special Permissions
Section 5 - Linux System Administration (Chapter 2)
Monitor Running Processes with ps Command
Run Processes in the Background
Terminate Running Processes with Kill & Pkill
Monitoring Running System with top
Listing Unit Files with systemctl
Start, Stop & Check The status of a Linux Service
The Truth About System Log
The rsyslog
The SystemD Journal
Boot, Reboot And Shut Down A System Normally
Boot Systems Into Different Targets Manually
Interrupt The Boot Process To Gain Access To A System
Adjust Process Priority With Renice
Section 6 - Linux System Administration (Chapter 3)
Examining the File System
Mounting & Unmounting File System
Create, Mount, Unmount And Use Vfat, ext4 And xfs File Systems
Mount and Unmount CIFS and NFS Network File Systems
Extend Existing Logical Volume
Create and manage Access Control Lists ACLs
Maintain Accurate Time with ntp
Validate Your Network Configuration
Configure Linux Network
Edit Network Configuration Files
Configuring Hostnames & Names Resolution
Install & Update Software with yum
Manage RPM Packages
Schedule Tasks Using at and cron
Section 7 - Linux System Administration (Chapter 4)
Configure Key-Based Authentication for SSH
Disallow User Root from Logging In Using SSH
Copying Files Securely Between Systems
Synchronize Files & Folders Securely Between Systems
Configure Firewall Settings Using Firewall-config & Firewall-cmd
Introduction To SElinux
List And Identify SElinux File And Process Context
Restore Default File Contexts
Use Boolean Settings To Modify System SElinux
Diagnose And Address Routine SElinux Policy Violation
Section 8 - Linux System Administration (Chapter 5)
Configure Aggregated Network Links Between 2 RHEL Systems or Interfaces
Configure IPv6 Addresses and Perform Basic IPv6 Troubleshooting
Firewalld - The rich rules
Configure Network Address Translation(NAT) - Masquerade
Configure Network Address Translation (NAT) - Port forwarding
Configure a system as an iSCSI target
Configure a system as an iSCSI initiator
Use procsys and sysctl to Modify or Set Kernel runtime parameters
Produce and deliver reports on system utilization(processor,memory,disk,network)
Section 9 - Linux System Administration (Advanced Topics)
Install the packages needed to provide the service
Configure SELinux to support the service
Use SELinux port labelling to allow services to use non-standard ports
Configure the service to start when the system is booted
Install and Configure Apache
Configure Apache access restrictions on directories
Configure Group Managed Content
Deploy a basic CGI application
Configure an Apache Virtual Host
Configure TLS security
The Apache Configuration File
Configure a Caching-Only Name Server
Provide network shares to specific clients
Provide network shares suitable for group collaboration
Use Kerberos to Control Access to NFS network shares (configure Kerberos)
Use Kerberos to Control Access to NFS network shares ( Configure Nfs Server )
Provide Network Shares to Specific Clients-client installation and configuration
Provide Network Shares Suitable for Group Collaboration
Configure a system to forward all emails to a central mail server
Configure Key-Based Authentication
Configure Key-Based Authentication 2
Synchronize time using other NTP peers
Install and Configure MariaDB
Create a simple database schema
Backup database
Perform simple SQL queries against a database
Restore a MariaDB database
Section 10 - Bonus 1: Secure Shell Deep Dive
Introduction To Secure Shell
How do I connect to a remote host
How do I connect to a remote host on a different SSH port
How can I login to a specific directory?
How do I execute a command on a remote host using SSH?
How can I copy (file/files) to a remote host using SCP?
How can I copy (file/files) from a remote host using SCP?
How can I Copy entire directory using SCP?
Can I limit the speed (bandwidth) of files transfer using SCP?
What is SFTP and how to connect to SFTP?
SFTP List file and check the working directory
SFTP Uploading Files
SFTP Downloading Files
SFTP Switching and Creating Directories
SFTP Remove Files and Directories
Multiple SSH Sessions with screen (Install Screen)
Multiple SSH Sessions with screen (Start working)
Multiple SSH Sessions with screen Lock and Exit from the screen
Tunneling x11 Through SSH (Linux)
Tunneling x11 Through SSH (Run Linux Applications on Windows)
Remote Desktop with SSH (Install and Configure VNC Server)
Remote Desktop with SSH (Connect to Remote Desktop)
Change The Default Port
Disable Direct Root Access
Allow Access for Certain User(s)
Deny Access from Known IPs
Allow Access from Known IPs
Public Key Authentication
Disable Password Authentication
Section 11 - Bonus 2: Additional Lectures
Vi editor part 1
Vi editor part 2
Create SWAP file and SWAP partition
Logical Volume Management (LVM)
Software RAID
Process Managment
VMSTAT And IOSTAT
List Open Files (LSOF)
Tcpdump
Search for Files on Linux using find and locate
Cat Command
Grep Command
AWK Command
HEAD Command
Network Clients (ssh , Scp , Ftp ,wget)
With that there will be 24 hour support for any questions or suggestions in the discussion forumÂ
And now after this description you must be concerned on what are you going to get out of this course by the end !Â
By the end of this course you will have the skills that will qualify you to apply for any Linux related job and be able to preform in real life situations. Â
==========================================================================================
For Assurance, check out what my students actually have to say about the course:
"I've taken dozens of courses on Udemy with some really great content, but this if you only take one course, this is the one to take. thank you.!!!" - Edward W. (5 Star Review)
"Five Star All The Way!!! Thanks guys you are the best on Udemy! Well explained course and easy to understand in a reasonable time. After completing the first section I am confident that this course will provide everything I had hoped for and more" - canning G. (5 Star Review)
"Thank you very much for the course! I look forward to seeing more lectures, he did not waste a word. Buy this course if you want to succeed. Very understandable!!!" - Kaichekanchap (5 Star Review)
                      Â
"Awesome dude!! great stuff, highly recommend. Simply Five Star. Thank you for showing us this innovative knowledge. It was extremely well educative" - Uppalakiran (5 Star Review)
"Simple and straightforward!!!!!! Wish I'd had access to a class like this years ago. The instructor are always here to help out, never had a problem to contact him regarding to the question in the course" - Sairepavan (5 Star Review)
"I have got more information about Linux, I would strongly recommend this course to all new professionals starting their career as a Linux administrator" - Abhishek Kumar P. (5 Star Review)
"Great job!!! Best course on udemy. Simple and sweet description. Anyone who want to learn linux can go through it. It gave me exactly what I was looking for" - Nervinara (5 Star Review)
Who this course is for:
- Anyone who would like to learn Linux and seek a job in Linux.
- Anyone interested in starting a career in Linux
- Anyone who wants to learn how to use the Linux command line and master the skill
- Anyone who wants to become a Linux system administrator
User Reviews
Rating
The Linux Lighthouse
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 192
- duration 25:39:25
- English subtitles has
- Release Date 2023/09/04