Learn Network Hacking in 2025: Attacking Network Components
Aleksa Tamburkovski
6:58:09
Description
Master network hacking: Learn exploit dev, build custom tools, and use pre-made tools to level up your security skills!
What You'll Learn?
- Common Network Vulnerabilities
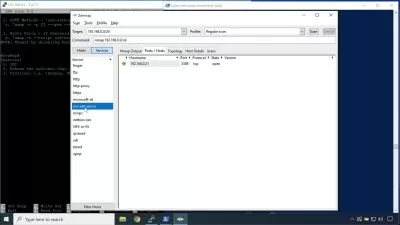
- Coding Python Hacking Tools To Test Network Security
- Using Kali Linux Tools to perform Network Penetration Testing
- Writing exploit from scratch for a Vulnerable Network Application
- Using gdb debugger to reverse Engineer an application
- Writing IDS/IPS rules for Network Traffic
- Learning about DNS Vulnerabilities
- Learning about common Router Vulnerabilities
- Learning about DHCP Attacks
- Showing Large Zero Day Vulnerability In Recent IPv6 Protocol
- Using Virtual Machines To Demonstrate Attacks
- Learning About Networking In General
- Learning How To Protect Against Common Network Attacks
- Many more things ...
Who is this for?
What You Need to Know?
More details
DescriptionIn this Network Hacking course, you'll dive deep into both the theory and hands-on techniques used by ethical hackers to secure and exploit network infrastructures. We’ll start with the fundamentals, covering essential networking concepts and protocols, before moving into advanced topics like attacking key network components—DNS, DHCP, routers, and more. You’ll learn how to execute powerful attacks such as Denial of Service (DoS), MAC spoofing, and exploiting applications over the network.
A unique feature of this course is its focus on coding your own hacking tools using Python, giving you the skills to automate attacks and craft custom solutions. We’ll also explore network security and protection strategies, including how to defend against ARP spoofing, write custom IDS/IPS rules, and secure routers to prevent unauthorized access. Whether you’re a beginner or looking to expand your expertise, this course offers a hands-on, in-depth approach to mastering network hacking and securing networks against common threats.
Here is Overview of the topics that we will cover:
1) Introduction To The Course
2) Denial of Service Attack
3) Bypassing Routers Whitelist/Blacklist
4) Man In The Middle Attack (MITM)
5) DNS Attacks
6) Vulnerabilities In Protocols/Network Components
7) DHCP Attacks
8) Router Hacking
9) Weak Cryptography
10) Project: Manually Exploiting Application Over The Network
11)Â Protecting The Network
12) Bonus Section: Learn Networking Basics
Who this course is for:
- Anyone Interested In more Advance Hacking
- Anyone Who Wants to Code Their Own Tools
- Anyone Who Wants to Learn To Code Their Own Exploit
- Anyone Generally Interested In Networking Vulnerabilities and Security
In this Network Hacking course, you'll dive deep into both the theory and hands-on techniques used by ethical hackers to secure and exploit network infrastructures. We’ll start with the fundamentals, covering essential networking concepts and protocols, before moving into advanced topics like attacking key network components—DNS, DHCP, routers, and more. You’ll learn how to execute powerful attacks such as Denial of Service (DoS), MAC spoofing, and exploiting applications over the network.
A unique feature of this course is its focus on coding your own hacking tools using Python, giving you the skills to automate attacks and craft custom solutions. We’ll also explore network security and protection strategies, including how to defend against ARP spoofing, write custom IDS/IPS rules, and secure routers to prevent unauthorized access. Whether you’re a beginner or looking to expand your expertise, this course offers a hands-on, in-depth approach to mastering network hacking and securing networks against common threats.
Here is Overview of the topics that we will cover:
1) Introduction To The Course
2) Denial of Service Attack
3) Bypassing Routers Whitelist/Blacklist
4) Man In The Middle Attack (MITM)
5) DNS Attacks
6) Vulnerabilities In Protocols/Network Components
7) DHCP Attacks
8) Router Hacking
9) Weak Cryptography
10) Project: Manually Exploiting Application Over The Network
11)Â Protecting The Network
12) Bonus Section: Learn Networking Basics
Who this course is for:
- Anyone Interested In more Advance Hacking
- Anyone Who Wants to Code Their Own Tools
- Anyone Who Wants to Learn To Code Their Own Exploit
- Anyone Generally Interested In Networking Vulnerabilities and Security
User Reviews
Rating
Aleksa Tamburkovski
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 43
- duration 6:58:09
- Release Date 2025/02/25