Learn Kubernetes and AKS Network Security
Houssem Dellai
3:07:50
Description
Learn how to secure network communication in AKS/Kubernetes cluster
What You'll Learn?
- Learn AKS and Kubernetes network best practices
- Learn how to securely expose services in Kubernetes
- Learn how to secure pod to pod communication
- Learn to setup TLS certificates for pods and ingress
Who is this for?
More details
DescriptionYou started your journey learning Kubernetes ?
You have been learning the fundamentals of a Kubernetes cluster ?
And now you want to make sure your cluster is production ready in terms of security ?
If you are looking for how to secure your Kubernetes cluster then this course is for you.
Let us face it, security is not an easy task. And Kubernetes is not an exception.
Securing a Kubernetes cluster requires thinking about all these aspects:
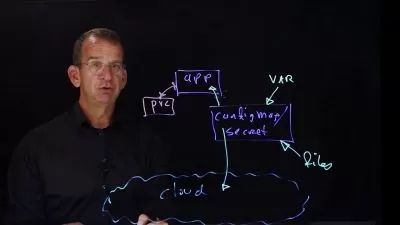
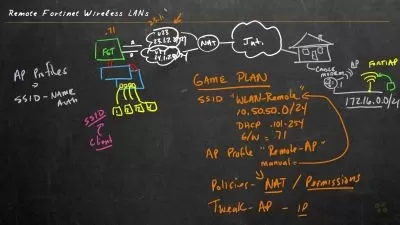
Network security: through private cluster access to API Server with Private Endpoint.
Secure egress traffic: all egress traffic should be filtered using Firewall.
Secure ingress traffic: using TLS and HTTPS on the ingress controller.
Secure inter-pod communication: secure traffic between pods using TLS or mTLS.
Controlling traffic between pods: using Network Policy tools like Calico.
Securing access to Managed Identities: by restricting access to IMDS endpoint (169.254.169.254).
Microsoft provides the following recommendations to secure an AKS cluster and this course will try to go deeper with demonstration.
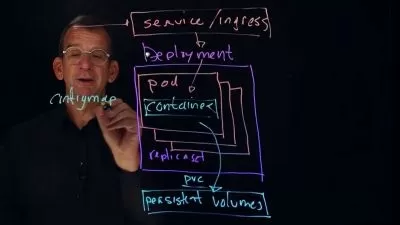
Recommendation 1: To distribute HTTP or HTTPS traffic to your applications, use ingress resources and controllers. Compared to an Azure load balancer, ingress controllers provide extra features and can be managed as native Kubernetes resources.
Recommendation 2: To scan incoming traffic for potential attacks, use a web application firewall (WAF) such as Barracuda WAF for Azure or Azure Application Gateway. These more advanced network resources can also route traffic beyond just HTTP and HTTPS connections or basic TLS termination.
Recommendation 3: Use network policies to allow or deny traffic to pods. By default, all traffic is allowed between pods within a cluster. For improved security, define rules that limit pod communication.
Recommendation 4: Don't expose remote connectivity to your AKS nodes. Create a bastion host, or jump box, in a management virtual network. Use the bastion host to securely route traffic into your AKS cluster to remote management tasks.
Disclaimer: This course uses Azure Kubernetes Service (AKS) for demonstrations. But most of the content is applicable to any Kubernetes cluster on any environment.
Who this course is for:
- This course is for platform teams that needs to manage Kubernetes cluster and securely deploy apps.
You started your journey learning Kubernetes ?
You have been learning the fundamentals of a Kubernetes cluster ?
And now you want to make sure your cluster is production ready in terms of security ?
If you are looking for how to secure your Kubernetes cluster then this course is for you.
Let us face it, security is not an easy task. And Kubernetes is not an exception.
Securing a Kubernetes cluster requires thinking about all these aspects:
Network security: through private cluster access to API Server with Private Endpoint.
Secure egress traffic: all egress traffic should be filtered using Firewall.
Secure ingress traffic: using TLS and HTTPS on the ingress controller.
Secure inter-pod communication: secure traffic between pods using TLS or mTLS.
Controlling traffic between pods: using Network Policy tools like Calico.
Securing access to Managed Identities: by restricting access to IMDS endpoint (169.254.169.254).
Microsoft provides the following recommendations to secure an AKS cluster and this course will try to go deeper with demonstration.
Recommendation 1: To distribute HTTP or HTTPS traffic to your applications, use ingress resources and controllers. Compared to an Azure load balancer, ingress controllers provide extra features and can be managed as native Kubernetes resources.
Recommendation 2: To scan incoming traffic for potential attacks, use a web application firewall (WAF) such as Barracuda WAF for Azure or Azure Application Gateway. These more advanced network resources can also route traffic beyond just HTTP and HTTPS connections or basic TLS termination.
Recommendation 3: Use network policies to allow or deny traffic to pods. By default, all traffic is allowed between pods within a cluster. For improved security, define rules that limit pod communication.
Recommendation 4: Don't expose remote connectivity to your AKS nodes. Create a bastion host, or jump box, in a management virtual network. Use the bastion host to securely route traffic into your AKS cluster to remote management tasks.
Disclaimer: This course uses Azure Kubernetes Service (AKS) for demonstrations. But most of the content is applicable to any Kubernetes cluster on any environment.
Who this course is for:
- This course is for platform teams that needs to manage Kubernetes cluster and securely deploy apps.
User Reviews
Rating
Houssem Dellai
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 38
- duration 3:07:50
- Release Date 2023/04/10