Learn Ethical Hacking & Build Python Attack & Defense Tools
Mark Nielsen
4:55:52
Description
Ethical Hacking using Python Hacking tools, Wireshark, and Kali Linux. The full Cybersecurity Expert Path
What You'll Learn?
- Intercept network traffic & modify it on the fly.
- Learn ethical hacking, its fields & the different types of hackers.
- Develop Python Hacking tools for Offense
- Install & use Kali Linux - a penetration testing operating system.
- Develop Python Hacking tools for Defense
- Python Security
- How to use Wireshark
- How to hack web systems using DVWA
- Computer Networking
- TCP/IP Protocol suite
- How to use Burp Suite
- CIA Triad
- What a honeypot it
Who is this for?
What You Need to Know?
More details
DescriptionWelcome to "Learn Ethical Hacking - Build Python Attack & Defense Tools," a comprehensive course that will teach you how to become an ethical hacker and build powerful tools using Python.
In this course, you'll learn how to think like a hacker and use that knowledge to protect your own systems from attack. You'll explore the different types of attacks, from phishing to denial of service, and learn how to defend against them. You'll also learn how to use Python to create your own custom attack and defense tools.
This course is designed for anyone who wants to learn ethical hacking and how to use Python to build attack and defense tools. Whether you're a beginner or an experienced programmer, you'll find this course to be informative and engaging.
Some of the topics covered in this course include:
Understanding the basics of ethical hacking
The different types of attacks and how to defend against them
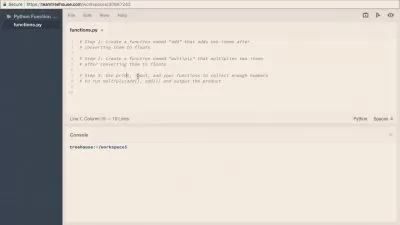
How to use Python to build custom attack and defense tools
Creating a port scanner using Python
Developing a password cracker using Python
Building a network sniffer using Python
Hacking the DVWA using Kali Linux
Computer Networking Crash course (OSI TCP/IP Protocol suite)
By the end of this course, you'll have a strong understanding of ethical hacking and how to use Python to build powerful attack and defense tools. You'll also have the skills and knowledge you need to pursue a career in cybersecurity or advance in your current role.
Enroll now and take the first step towards becoming an ethical hacker and Python developer.
Who this course is for:
- People interested in learning ethical hacking / penetration testing
- People interested in learning how hackers hack computer systems
- People interested in learning how to secure systems from hackers (Ethical Hacking)
Welcome to "Learn Ethical Hacking - Build Python Attack & Defense Tools," a comprehensive course that will teach you how to become an ethical hacker and build powerful tools using Python.
In this course, you'll learn how to think like a hacker and use that knowledge to protect your own systems from attack. You'll explore the different types of attacks, from phishing to denial of service, and learn how to defend against them. You'll also learn how to use Python to create your own custom attack and defense tools.
This course is designed for anyone who wants to learn ethical hacking and how to use Python to build attack and defense tools. Whether you're a beginner or an experienced programmer, you'll find this course to be informative and engaging.
Some of the topics covered in this course include:
Understanding the basics of ethical hacking
The different types of attacks and how to defend against them
How to use Python to build custom attack and defense tools
Creating a port scanner using Python
Developing a password cracker using Python
Building a network sniffer using Python
Hacking the DVWA using Kali Linux
Computer Networking Crash course (OSI TCP/IP Protocol suite)
By the end of this course, you'll have a strong understanding of ethical hacking and how to use Python to build powerful attack and defense tools. You'll also have the skills and knowledge you need to pursue a career in cybersecurity or advance in your current role.
Enroll now and take the first step towards becoming an ethical hacker and Python developer.
Who this course is for:
- People interested in learning ethical hacking / penetration testing
- People interested in learning how hackers hack computer systems
- People interested in learning how to secure systems from hackers (Ethical Hacking)
User Reviews
Rating
Mark Nielsen
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 22
- duration 4:55:52
- Release Date 2023/06/12