Learn EC-Council Certified Encryption Specialist (ECES)
Raheem ace
1:57:14
Description
Cryptographic Excellence: Dive into Encryption Technologies, Strategies and Techniques for Modern Security. (Unofficial)
What You'll Learn?
- Recognize the significance of encryption in safeguarding digital information.
- Understand the role of encryption in ensuring data confidentiality, integrity, and authenticity.
- Grasp foundational concepts of cryptography that underpin secure communication.
- Types of Encryption Algorithms
- Gain insights into essential concepts such as key management, encryption key lifecycle, and secure key exchange.
- Symmetric and Asymmetric Key Encryption
- Hash Functions and Digital Signatures
- Public Key Infrastructure (PKI) and SSL/TLS Protocols
- Dive into industry-standard encryption algorithms and their applications.
- Encryption in Network Security
- Encryption in Operating Systems
- Data Protection and Compliance
- Secure Communication Protocols
- Identify common cryptographic attacks and learn defense mechanisms.
- Encryption Best Practices
- and much more
Who is this for?
What You Need to Know?
More details
DescriptionIMPORTANT before enrolling:
This course is designed to complement your preparation for certification exams, but it is not a substitute for official vendor materials. It is not endorsed by the certification vendor, and you will not receive the official certification study material or a voucher as part of this course.
Welcome to "Mastering Encryption (ECES): Safeguarding Digital Worlds with Advanced Cybersecurity Strategies."
This comprehensive course is designed to empower you with the knowledge and skills needed to navigate the intricate realm of encryption, a critical component in the ever-evolving landscape of cybersecurity.
ECES certification is designed for individuals who want to specialize in encryption technologies and techniques. The program covers a range of topics related to encryption, including both basic and advanced concepts. Participants in the ECES program typically learn about different encryption algorithms, cryptographic protocols, secure communication, and best practices for implementing encryption in various environments.
In this course, we will embark on a journey through the fundamental concepts, principles, and technologies that form the backbone of encryption. Beginning with an exploration of the Importance of Encryption in Cybersecurity, we delve into the Basics of Cryptography, covering the underlying principles that govern secure communication.
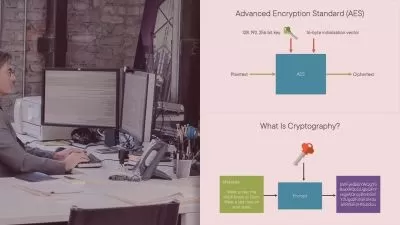
Our journey continues with an in-depth examination of various encryption techniques. We will unravel the mysteries behind Symmetric and Asymmetric Key Encryption, uncover the power of Hash Functions and Digital Signatures, and explore the intricacies of Public Key Infrastructure (PKI) and SSL/TLS Protocols for ensuring secure communication channels.
Dive into the world of encryption algorithms with dedicated lectures on industry standards such as Advanced Encryption Standard (AES), RSA Algorithm, Elliptic Curve Cryptography (ECC), Triple DES, Blowfish, and even touch on the cutting-edge concepts in Quantum Cryptography.
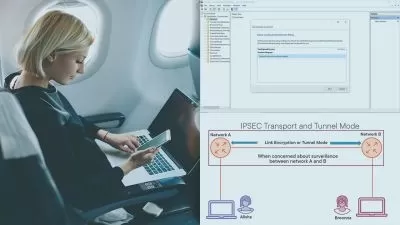
Navigate the complex landscape of Network Security with insights into VPNs, IPsec, SSL VPNs, and the encryption protocols protecting wireless networks and emails (WPA, WPA2, WPA3, PGP, S/MIME). Explore the role of encryption in Operating Systems, including Disk Encryption (BitLocker, FileVault), File and Folder Encryption, and encryption practices on mobile devices (Android, iOS).
Understand the critical aspects of Data Protection and Compliance with lectures on Data Loss Prevention (DLP) and the implications of regulations like GDPR on encryption requirements.
The course also covers Secure Communication Protocols, including Secure File Transfer (SFTP, SCP), Secure Shell (SSH), and Secure Web Browsing (HTTPS). Delve into the realm of Cryptographic Attacks and Countermeasures, equipping yourself with the knowledge needed to defend against common threats.
Finally, we explore Encryption Best Practices, including implementing strong password policies, key management strategies, security awareness training, and monitoring and auditing encryption activities.
"Mastering Encryption" is not just a course; it's a comprehensive guide that will empower you to implement robust encryption strategies, safeguarding digital information in an increasingly interconnected world.
The certification aims to validate the skills and knowledge of professionals in the field of encryption and data protection. It may be particularly relevant for cybersecurity professionals, IT administrators, and anyone involved in securing digital information.
Whether you are a cybersecurity professional, IT enthusiast, or someone looking to enhance their knowledge in digital defense, this course provides the tools and insights needed to become a guardian of privacy and security in the digital age.
Thank you
Who this course is for:
- Cybersecurity Professionals: Individuals working in the field of cybersecurity who want to deepen their understanding of encryption technologies and enhance their skills in securing digital information.
- IT Administrators and Network Engineers: Professionals responsible for managing and securing IT infrastructure, networks, and communication channels.
- Developers and Programmers: Those involved in software development who want to integrate secure coding practices and understand how encryption plays a crucial role in protecting data.
- Information Security Analysts: Analysts responsible for assessing and mitigating security risks within an organization.
- Security Consultants: Individuals providing advisory services on cybersecurity strategies and solutions.
- Compliance and Privacy Professionals: Professionals concerned with regulatory compliance and privacy requirements, as encryption is often a key component of data protection strategies.
- Students and Enthusiasts: Students pursuing a career in cybersecurity or individuals with a keen interest in understanding encryption principles and best practices.
- Business Owners and Managers: Entrepreneurs and managers who want to grasp the importance of encryption in securing their business's digital assets.
- Anyone Interested in Digital Defense: Individuals who recognize the increasing importance of digital security and want to empower themselves with knowledge about encryption technologies.
- Course is structured to accommodate learners at various levels, providing a solid foundation for beginners while delving into advanced concepts for those with more experience in cybersecurity. Whether you are looking to enhance your professional skills or simply gain a better understanding of digital defense, this course offers valuable insights into the world of encryption and cybersecurity.
IMPORTANT before enrolling:
This course is designed to complement your preparation for certification exams, but it is not a substitute for official vendor materials. It is not endorsed by the certification vendor, and you will not receive the official certification study material or a voucher as part of this course.
Welcome to "Mastering Encryption (ECES): Safeguarding Digital Worlds with Advanced Cybersecurity Strategies."
This comprehensive course is designed to empower you with the knowledge and skills needed to navigate the intricate realm of encryption, a critical component in the ever-evolving landscape of cybersecurity.
ECES certification is designed for individuals who want to specialize in encryption technologies and techniques. The program covers a range of topics related to encryption, including both basic and advanced concepts. Participants in the ECES program typically learn about different encryption algorithms, cryptographic protocols, secure communication, and best practices for implementing encryption in various environments.
In this course, we will embark on a journey through the fundamental concepts, principles, and technologies that form the backbone of encryption. Beginning with an exploration of the Importance of Encryption in Cybersecurity, we delve into the Basics of Cryptography, covering the underlying principles that govern secure communication.
Our journey continues with an in-depth examination of various encryption techniques. We will unravel the mysteries behind Symmetric and Asymmetric Key Encryption, uncover the power of Hash Functions and Digital Signatures, and explore the intricacies of Public Key Infrastructure (PKI) and SSL/TLS Protocols for ensuring secure communication channels.
Dive into the world of encryption algorithms with dedicated lectures on industry standards such as Advanced Encryption Standard (AES), RSA Algorithm, Elliptic Curve Cryptography (ECC), Triple DES, Blowfish, and even touch on the cutting-edge concepts in Quantum Cryptography.
Navigate the complex landscape of Network Security with insights into VPNs, IPsec, SSL VPNs, and the encryption protocols protecting wireless networks and emails (WPA, WPA2, WPA3, PGP, S/MIME). Explore the role of encryption in Operating Systems, including Disk Encryption (BitLocker, FileVault), File and Folder Encryption, and encryption practices on mobile devices (Android, iOS).
Understand the critical aspects of Data Protection and Compliance with lectures on Data Loss Prevention (DLP) and the implications of regulations like GDPR on encryption requirements.
The course also covers Secure Communication Protocols, including Secure File Transfer (SFTP, SCP), Secure Shell (SSH), and Secure Web Browsing (HTTPS). Delve into the realm of Cryptographic Attacks and Countermeasures, equipping yourself with the knowledge needed to defend against common threats.
Finally, we explore Encryption Best Practices, including implementing strong password policies, key management strategies, security awareness training, and monitoring and auditing encryption activities.
"Mastering Encryption" is not just a course; it's a comprehensive guide that will empower you to implement robust encryption strategies, safeguarding digital information in an increasingly interconnected world.
The certification aims to validate the skills and knowledge of professionals in the field of encryption and data protection. It may be particularly relevant for cybersecurity professionals, IT administrators, and anyone involved in securing digital information.
Whether you are a cybersecurity professional, IT enthusiast, or someone looking to enhance their knowledge in digital defense, this course provides the tools and insights needed to become a guardian of privacy and security in the digital age.
Thank you
Who this course is for:
- Cybersecurity Professionals: Individuals working in the field of cybersecurity who want to deepen their understanding of encryption technologies and enhance their skills in securing digital information.
- IT Administrators and Network Engineers: Professionals responsible for managing and securing IT infrastructure, networks, and communication channels.
- Developers and Programmers: Those involved in software development who want to integrate secure coding practices and understand how encryption plays a crucial role in protecting data.
- Information Security Analysts: Analysts responsible for assessing and mitigating security risks within an organization.
- Security Consultants: Individuals providing advisory services on cybersecurity strategies and solutions.
- Compliance and Privacy Professionals: Professionals concerned with regulatory compliance and privacy requirements, as encryption is often a key component of data protection strategies.
- Students and Enthusiasts: Students pursuing a career in cybersecurity or individuals with a keen interest in understanding encryption principles and best practices.
- Business Owners and Managers: Entrepreneurs and managers who want to grasp the importance of encryption in securing their business's digital assets.
- Anyone Interested in Digital Defense: Individuals who recognize the increasing importance of digital security and want to empower themselves with knowledge about encryption technologies.
- Course is structured to accommodate learners at various levels, providing a solid foundation for beginners while delving into advanced concepts for those with more experience in cybersecurity. Whether you are looking to enhance your professional skills or simply gain a better understanding of digital defense, this course offers valuable insights into the world of encryption and cybersecurity.
User Reviews
Rating
Raheem ace
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 33
- duration 1:57:14
- Release Date 2024/04/14