Kali Linux and Windows Hacking and Security: IT SEC
Cyber Security Online Training
13:15:13
Description
Learn all tools and techniques of Kali with all hacking tools for Windows Operating System
What You'll Learn?
- Learn Kali from scratch
- Learn different tools and techniques in kali
- Learn about Windows Security
- Learn to know how to attack on Win OS
Who is this for?
More details
DescriptionKALI=
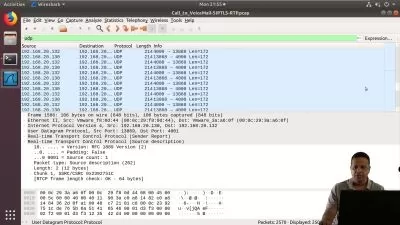
Kali Linux is a Linux distribution that is specialized for cybersecurity. It is an open-source product that involves a lot of customization for penetration testing, which helps companies to understand their vulnerabilities.
While many experts recommend against Kali Linux for beginners, those who are interested in cybersecurity often benefit from using this specific Linux distribution. Kali Linux offers “single root user†design as a way to handle privileges, and users can disable network services by default. That is helpful for the penetration testing and data forensics that can be used to determine a company's weak points in a risk mitigation project.
Kali Linux has over 600 preinstalled penetration-testing applications to discover. Each program with its unique flexibility and use case.
Kali Linux is used by Security Administrators – Security Administrators are responsible for safeguarding their institution’s information and data. They use Kali Linux to review their environment(s) and ensure there are no easily discoverable vulnerabilities.
Kali is also used by Forensics Expert and Network administrators are in charge of keeping the network running smoothly and securely. They audit their network with kali Linux. Kali Linux is mainly used for advanced Penetration Testing and Security Many systems.
So let's get started....
For Windows=
You will learn most of the important tools and techniques used to test the security of your Computer System and Mobile Devices. You will learn how to hack your device and how to protect them from various external Threats. System Hacking is the activity of identifying weaknesses in a computer system or a network to exploit the security to gain access to personal data or business data. An example of system hacking can be: using a password cracking tool to gain access to a computer system. You may also perform System Hacking without using any kind of tool. Learning computer hacking and security is an important aspect in today world. Let's have a look on the topics you will learn in this course.
Topics Covered in this Course are:
1. Footprinting
2. Scanning
3. Gaining Access
4. Maintaining Access
5. Clearing Tracks
6. Generating Reports
7. Quick Hacking Tips
8. Hands-on Training
9. Hacking Mobile Device
10. Securing your Computer and Mobile.
Anyone who is interested to learn about Cyber Security may join this course.Â
This course doesn't make you an expert in the field of cyber security. But, this course will teach you practical things which are must to learn for an individual if you want to know about latest attacks and their defence.
Also learn Ethical Hacking with Kali for 2022.
Let's get started....
Who this course is for:
- Anyone who want to learn Kali and Win OS Hacks
KALI=
Kali Linux is a Linux distribution that is specialized for cybersecurity. It is an open-source product that involves a lot of customization for penetration testing, which helps companies to understand their vulnerabilities.
While many experts recommend against Kali Linux for beginners, those who are interested in cybersecurity often benefit from using this specific Linux distribution. Kali Linux offers “single root user†design as a way to handle privileges, and users can disable network services by default. That is helpful for the penetration testing and data forensics that can be used to determine a company's weak points in a risk mitigation project.
Kali Linux has over 600 preinstalled penetration-testing applications to discover. Each program with its unique flexibility and use case.
Kali Linux is used by Security Administrators – Security Administrators are responsible for safeguarding their institution’s information and data. They use Kali Linux to review their environment(s) and ensure there are no easily discoverable vulnerabilities.
Kali is also used by Forensics Expert and Network administrators are in charge of keeping the network running smoothly and securely. They audit their network with kali Linux. Kali Linux is mainly used for advanced Penetration Testing and Security Many systems.
So let's get started....
For Windows=
You will learn most of the important tools and techniques used to test the security of your Computer System and Mobile Devices. You will learn how to hack your device and how to protect them from various external Threats. System Hacking is the activity of identifying weaknesses in a computer system or a network to exploit the security to gain access to personal data or business data. An example of system hacking can be: using a password cracking tool to gain access to a computer system. You may also perform System Hacking without using any kind of tool. Learning computer hacking and security is an important aspect in today world. Let's have a look on the topics you will learn in this course.
Topics Covered in this Course are:
1. Footprinting
2. Scanning
3. Gaining Access
4. Maintaining Access
5. Clearing Tracks
6. Generating Reports
7. Quick Hacking Tips
8. Hands-on Training
9. Hacking Mobile Device
10. Securing your Computer and Mobile.
Anyone who is interested to learn about Cyber Security may join this course.Â
This course doesn't make you an expert in the field of cyber security. But, this course will teach you practical things which are must to learn for an individual if you want to know about latest attacks and their defence.
Also learn Ethical Hacking with Kali for 2022.
Let's get started....
Who this course is for:
- Anyone who want to learn Kali and Win OS Hacks
User Reviews
Rating
Cyber Security Online Training
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 151
- duration 13:15:13
- Release Date 2022/12/24