ITAM / Cyber Security Workshop with NIST - CIS - ITAM Map
Keith Rupnik,Regina Rupnik
1:15:39
Description
Learn how IT Asset Management supports cybersecurity in over 750 ways! Includes NIST - CIS - ITAM mapping!
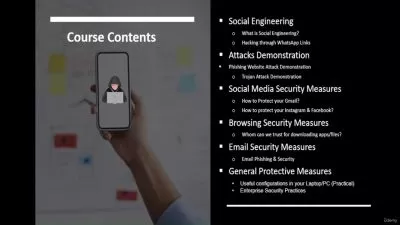
What You'll Learn?
- How the relationship between ITAM and IT security makes IT security’s objectives attainable.
- The mapping of ITAM components to both CIS’s and NIST's cybersecurity frameworks.
- How to use the mapping to assess the ITAM program’s support for IT security.
- How to move the ITAM program forward with IT security.
- The reason for managing the IT asset’s lifecycle.
- The critical components of the ITAM program.
- The value of each lifecycle phase to IT security as well as other departments.
Who is this for?
What You Need to Know?
More details
DescriptionAs an organization, your network's attack surface is the primary vulnerability that attackers exploit to cause harm. To effectively manage your attack surface, keeping an accurate inventory of all assets, including those owned by the corporation, employees, and vendors, is crucial. You can monitor real-time changes by employing IMACD (install, move, add, change, dispose). However, this relies on upstream processes, policies, and standards that begin before acquisition and continue after end-of-life. It is important to limit exceptions and ensure that executive management supports these processes, policies, and standards.
In this workshop, you will learn how ITAM supports cybersecurity in over 750 ways so that you can protect your organization's data, which are its crown jewels. You will also receive the mapping between ITAM's 37 key components to NIST's and CIS's security controls. Utilizing the mapping, you can confidently apply the knowledge gained from the workshop to benchmark and advance your IT, ITAM, and IT security programs. This will expand your educational experience beyond the workshop. You will also learn how ITAM benefits departments other than IT security. Funding ITAM initiatives is one of the best investments for your organization, and executives will love it!
This workshop will teach you about ITAM's impact on IT security and the entire organization. You will receive a tool that, when appropriately used, will accelerate your ITAM, IT, and IT security programs by assessing your current ITAM Program's performance and then developing a roadmap for improvement.
Who this course is for:
- IT Asset Managers, Hardware Asset Managers, Software Asset Managers, Cloud Asset Managers: Learn how critical ITAM is to IT security according to two leading cyber security frameworks from NIST and CIS. You will receive the tools necessary to advance your ITAM Program and increase its visibility!
- IT Security Managers and Professionals: NIST and CIS require an accurate IT asset inventory but do not explain how to achieve one. Learn what is needed to implement an ITAM Program to meet this objective and how you can interface with your ITAM team!
- IT Managers, IT Professionals: The pressure is on to help secure your organization’s data, and you have a critical role in this. Learn how many IT processes contribute data to ITAM and significantly impact your organization’s security program based on NIST’s and CIS’s cybersecurity frameworks!
- IT Cloud Managers: Cloud security is on everyone’s mind, and you can’t assume it’s your cloud service provider’s problem. Learn how ITAM, IT, and IT security work together to secure your organization’s data and what your cloud service providers should be doing!
As an organization, your network's attack surface is the primary vulnerability that attackers exploit to cause harm. To effectively manage your attack surface, keeping an accurate inventory of all assets, including those owned by the corporation, employees, and vendors, is crucial. You can monitor real-time changes by employing IMACD (install, move, add, change, dispose). However, this relies on upstream processes, policies, and standards that begin before acquisition and continue after end-of-life. It is important to limit exceptions and ensure that executive management supports these processes, policies, and standards.
In this workshop, you will learn how ITAM supports cybersecurity in over 750 ways so that you can protect your organization's data, which are its crown jewels. You will also receive the mapping between ITAM's 37 key components to NIST's and CIS's security controls. Utilizing the mapping, you can confidently apply the knowledge gained from the workshop to benchmark and advance your IT, ITAM, and IT security programs. This will expand your educational experience beyond the workshop. You will also learn how ITAM benefits departments other than IT security. Funding ITAM initiatives is one of the best investments for your organization, and executives will love it!
This workshop will teach you about ITAM's impact on IT security and the entire organization. You will receive a tool that, when appropriately used, will accelerate your ITAM, IT, and IT security programs by assessing your current ITAM Program's performance and then developing a roadmap for improvement.
Who this course is for:
- IT Asset Managers, Hardware Asset Managers, Software Asset Managers, Cloud Asset Managers: Learn how critical ITAM is to IT security according to two leading cyber security frameworks from NIST and CIS. You will receive the tools necessary to advance your ITAM Program and increase its visibility!
- IT Security Managers and Professionals: NIST and CIS require an accurate IT asset inventory but do not explain how to achieve one. Learn what is needed to implement an ITAM Program to meet this objective and how you can interface with your ITAM team!
- IT Managers, IT Professionals: The pressure is on to help secure your organization’s data, and you have a critical role in this. Learn how many IT processes contribute data to ITAM and significantly impact your organization’s security program based on NIST’s and CIS’s cybersecurity frameworks!
- IT Cloud Managers: Cloud security is on everyone’s mind, and you can’t assume it’s your cloud service provider’s problem. Learn how ITAM, IT, and IT security work together to secure your organization’s data and what your cloud service providers should be doing!
User Reviews
Rating
Keith Rupnik
Instructor's CoursesRegina Rupnik
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 14
- duration 1:15:39
- Release Date 2023/09/04