IT Security Foundations: Operating System Security
Focused View
Lisa Bock
1:42:43
297 View
01 - Ensuring system security.mp4
00:59
02 - Resources.mp4
00:23
01 - Securing the Windows OS.mp4
04:03
02 - Visualizing the Windows architecture.mp4
04:37
03 - Dissecting the NTFS.mp4
04:51
04 - NTFS demo.mp4
02:39
05 - Controlling folder access.mp4
02:54
06 - Using runas.mp4
02:55
07 - Exploring User Account Control (UAC).mp4
04:19
01 - Protecting your macOS.mp4
02:59
02 - Interacting with a Linux OS.mp4
02:10
03 - Using the Linux file system.mp4
03:10
04 - Avoiding malware on a Linux host.mp4
02:36
01 - Identify and authenticate.mp4
02:49
02 - Passwords and complexity.mp4
04:52
03 - Smart cards and tokens.mp4
02:59
04 - Biometric identification.mp4
05:02
05 - Multi-factor authentication.mp4
02:59
01 - Using a firewall.mp4
03:46
02 - Locking down the browser.mp4
03:15
03 - Hardening the OS.mp4
02:29
04 - Protocol good practices.mp4
03:49
01 - Email clients and servers.mp4
04:42
02 - Email and SPAM.mp4
04:33
03 - PTR records.mp4
02:15
01 - Cryptographic techniques.mp4
03:13
02 - Symmetric encryption.mp4
04:02
03 - Asymmetric encryption.mp4
03:31
04 - Diving into hash algorithms.mp4
04:54
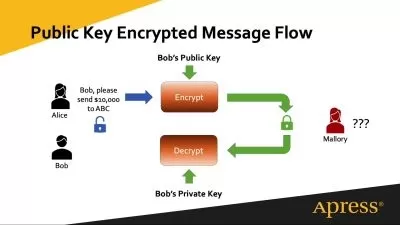
05 - Public Key Infrastructure.mp4
03:35
01 - Next steps.mp4
01:23
Description
The operating system is where many attacks are targeted, which makes OS-level security just as important to your organization as network security. In this course, instructor Lisa Bock details what’s actually involved in securing an operating system, whether you’re using Windows, macOS, or Linux. Lisa reviews user authentication, the structure of Active Directory, and how to assign permissions and create audit policies. In addition, she covers various cryptographic techniques, as well as how to protect servers and email.
More details
User Reviews
Rating
average 0
Focused display
Category
Lisa Bock
Instructor's CoursesExperienced author with a demonstrated history of working in the e-learning industry. She is a security ambassador with a broad range of IT skills and knowledge, including networking, CyberOps, Wireshark, biometrics, Ethical Hacking and the IoT. Lisa is an author for LinkedIn Learning, Packt Publishing and CompTIA and is an award-winning speaker who has presented at several national conferences. She holds a MS in computer information systems/information assurance from UMGC. Lisa was an associate professor in the IT department at Pennsylvania College of Technology (Williamsport, PA) from 2003 until her retirement in 2020. She is involved with various volunteer activities, and she and her husband Mike enjoy bike riding, watching movies, and traveling.

Linkedin Learning
View courses Linkedin LearningLinkedIn Learning is an American online learning provider. It provides video courses taught by industry experts in software, creative, and business skills. It is a subsidiary of LinkedIn. All the courses on LinkedIn fall into four categories: Business, Creative, Technology and Certifications.
It was founded in 1995 by Lynda Weinman as Lynda.com before being acquired by LinkedIn in 2015. Microsoft acquired LinkedIn in December 2016.
- language english
- Training sessions 31
- duration 1:42:43
- Release Date 2023/01/10