ISO 27005:2022 Manage Information Security Risk Step by Step
Dr. Amar Massoud
4:27:06
Description
With a Use Case and Templates
What You'll Learn?
- Understand and apply ISO 27005:2022 methodologies for information security risk assessments.
- Identify, analyze, and evaluate risks to information security within an organizational context.
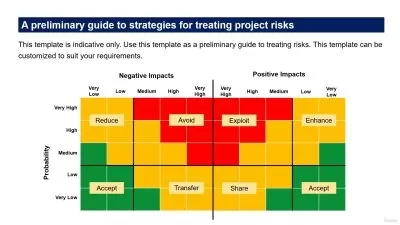
- Develop and implement effective risk treatment plans aligned with ISO 27005:2022 guidelines.
- Continuously monitor and review risk management processes for ongoing improvement and compliance.
Who is this for?
What You Need to Know?
More details
DescriptionCourse Overview: Dive into the world of risk assessment in line with ISO/IEC 27005:2022 standards in our comprehensive course. This training is uniquely designed to provide a blend of theoretical knowledge and practical application, using a fictional model company, "HealthSecure Inc.," as a continuous case study throughout the course.
What You'll Learn:
Fundamentals of ISO 27005:2022: Understand the core concepts, principles, and frameworks of ISO 27005:2022.
Risk Assessment Techniques: Learn to identify, analyze, and evaluate information security risks using proven methodologies.
Practical Application: Apply your learning to real-life scenarios through the HealthSecure Inc. case study, encompassing various aspects of risk assessment and treatment.
Use of Tools and Templates: Gain hands-on experience with risk assessment tools and templates that can be adapted to your professional context.
Course Features:
Interactive Learning: Engaging content including lectures, interactive sessions, and group discussions.
HealthSecure Inc. Case Study: A comprehensive use case running throughout the course, providing practical insights into the application of risk assessment in a business environment.
Hands-On Assignments: Practical assignments and projects that simulate real-world risk assessment challenges.
Resource Toolkit: Access to a range of templates and tools for conducting risk assessments, allowing for immediate application in your workplace.
Expert Instructors: Learn from experienced professionals with extensive knowledge in information security and risk management.
Who Should Enroll: This course is ideal for IT and cybersecurity professionals, compliance officers, risk managers, business leaders, and anyone interested in mastering the art and science of ISO 27005:2022 risk assessment.
Course Goals: By the end of this course, participants will be able to confidently conduct risk assessments and develop comprehensive risk treatment plans in alignment with ISO 27005:2022 standards, leveraging the practical experience gained from the HealthSecure Inc. case study.
Join us to enhance your skills in information security risk assessment and contribute to the robust security posture of your organization.
Who this course is for:
- Information Security Professionals: Ideal for those working in or aspiring to work in information security roles, including security analysts, managers, and consultants who seek to deepen their understanding of risk assessment in line with ISO standards.
- IT Professionals: IT staff responsible for managing and safeguarding digital assets. The course is particularly beneficial for those involved in developing or maintaining an Information Security Management System (ISMS).
- Compliance Officers and Auditors: Professionals involved in ensuring regulatory compliance or conducting internal audits within organizations, especially in sectors with stringent data protection and privacy regulations.
- Business Managers and Executives: Decision-makers who need to understand the risk landscape of their organizations to make informed decisions about information security strategies and investments.
- Project Managers and Developers: Individuals responsible for overseeing IT projects, including software development, who need to incorporate risk management into their project lifecycle.
- Students and Academics: Learners in the fields of cybersecurity, information technology, or business management who aim to gain a comprehensive understanding of risk assessment methodologies and practices.
Course Overview: Dive into the world of risk assessment in line with ISO/IEC 27005:2022 standards in our comprehensive course. This training is uniquely designed to provide a blend of theoretical knowledge and practical application, using a fictional model company, "HealthSecure Inc.," as a continuous case study throughout the course.
What You'll Learn:
Fundamentals of ISO 27005:2022: Understand the core concepts, principles, and frameworks of ISO 27005:2022.
Risk Assessment Techniques: Learn to identify, analyze, and evaluate information security risks using proven methodologies.
Practical Application: Apply your learning to real-life scenarios through the HealthSecure Inc. case study, encompassing various aspects of risk assessment and treatment.
Use of Tools and Templates: Gain hands-on experience with risk assessment tools and templates that can be adapted to your professional context.
Course Features:
Interactive Learning: Engaging content including lectures, interactive sessions, and group discussions.
HealthSecure Inc. Case Study: A comprehensive use case running throughout the course, providing practical insights into the application of risk assessment in a business environment.
Hands-On Assignments: Practical assignments and projects that simulate real-world risk assessment challenges.
Resource Toolkit: Access to a range of templates and tools for conducting risk assessments, allowing for immediate application in your workplace.
Expert Instructors: Learn from experienced professionals with extensive knowledge in information security and risk management.
Who Should Enroll: This course is ideal for IT and cybersecurity professionals, compliance officers, risk managers, business leaders, and anyone interested in mastering the art and science of ISO 27005:2022 risk assessment.
Course Goals: By the end of this course, participants will be able to confidently conduct risk assessments and develop comprehensive risk treatment plans in alignment with ISO 27005:2022 standards, leveraging the practical experience gained from the HealthSecure Inc. case study.
Join us to enhance your skills in information security risk assessment and contribute to the robust security posture of your organization.
Who this course is for:
- Information Security Professionals: Ideal for those working in or aspiring to work in information security roles, including security analysts, managers, and consultants who seek to deepen their understanding of risk assessment in line with ISO standards.
- IT Professionals: IT staff responsible for managing and safeguarding digital assets. The course is particularly beneficial for those involved in developing or maintaining an Information Security Management System (ISMS).
- Compliance Officers and Auditors: Professionals involved in ensuring regulatory compliance or conducting internal audits within organizations, especially in sectors with stringent data protection and privacy regulations.
- Business Managers and Executives: Decision-makers who need to understand the risk landscape of their organizations to make informed decisions about information security strategies and investments.
- Project Managers and Developers: Individuals responsible for overseeing IT projects, including software development, who need to incorporate risk management into their project lifecycle.
- Students and Academics: Learners in the fields of cybersecurity, information technology, or business management who aim to gain a comprehensive understanding of risk assessment methodologies and practices.
User Reviews
Rating
Dr. Amar Massoud
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 48
- duration 4:27:06
- English subtitles has
- Release Date 2024/02/14








![Risk Management Masterclass [2023] | Certification Course](https://traininghub.ir/image/course_pic/14196-x225.webp)