Introduction to Cybersecurity : Understanding and Preventing
Raphael Asghar
4:45:20
Description
Foundations of Cybersecurity
What You'll Learn?
- Students will grasp the intricacies of various cyber threats, from common malware to sophisticated social engineering tactics, gaining insights into the methods
- Students will develop a solid foundation in network components, mastering the essentials of secure communication infrastructures
- Students will differentiate between different hacker personas, including white hats, black hats, and gray hats, understanding their motives and techniques
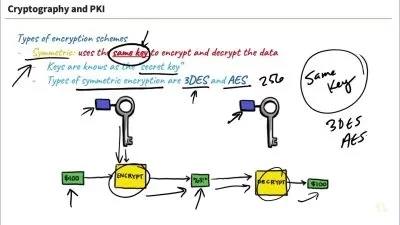
- Through practical examples, students will learn to apply preventative methods such as encryption, firewalls, prevent phishing email ,and other strategic tools
Who is this for?
What You Need to Know?
More details
DescriptionWelcome to the fascinating realm of cybersecurity, where the digital frontier demands vigilant guardians like yourself. I created and designed this course to empower you with the knowledge and skills necessary to navigate the ever-evolving landscape of cyber threats. It is for the absolute beginner, so no prior knowledge of cybersecurity is required. However, an understanding of how the network works will greatly benefit you. I divided this course into four sections to make it easier to navigate.
First, delve into the fundamental understanding of cybersecurity, unraveling its significance and role in safeguarding digital assets.
Second, explore the intricate web of network components, unraveling the complexities that underpin secure communication infrastructures.
Third, journey further as you uncover the diverse personas of hackers, distinguishing between the white hats, black hats, and gray hats, each with their unique motives and methodologies. Unearth the myriad threats that lurk in the digital shadows, from malware to social engineering, and equip yourself with the knowledge to counteract these insidious forces.
Finally, fortify your defenses by delving into preventative methods, embracing encryption, firewalls, and other strategic measures to fortify digital fortresses. Embark on this educational odyssey and emerge as a cyber guardian armed with the expertise to navigate, protect, and secure your digital landscape.
Who this course is for:
- This cybersecurity course is designed with the beginner in mind, offering an entry point into the world of digital security. As a student, you are not required to have an extensive background in cybersecurity or IT; The course assumes no prior knowledge of cybersecurity concepts, making it accessible to those who are taking their first steps into this field. Through a carefully crafted curriculum, you'll gradually build a strong foundation by learning about cyber threats, network components, hacker personas, and practical preventative measures.
Welcome to the fascinating realm of cybersecurity, where the digital frontier demands vigilant guardians like yourself. I created and designed this course to empower you with the knowledge and skills necessary to navigate the ever-evolving landscape of cyber threats. It is for the absolute beginner, so no prior knowledge of cybersecurity is required. However, an understanding of how the network works will greatly benefit you. I divided this course into four sections to make it easier to navigate.
First, delve into the fundamental understanding of cybersecurity, unraveling its significance and role in safeguarding digital assets.
Second, explore the intricate web of network components, unraveling the complexities that underpin secure communication infrastructures.
Third, journey further as you uncover the diverse personas of hackers, distinguishing between the white hats, black hats, and gray hats, each with their unique motives and methodologies. Unearth the myriad threats that lurk in the digital shadows, from malware to social engineering, and equip yourself with the knowledge to counteract these insidious forces.
Finally, fortify your defenses by delving into preventative methods, embracing encryption, firewalls, and other strategic measures to fortify digital fortresses. Embark on this educational odyssey and emerge as a cyber guardian armed with the expertise to navigate, protect, and secure your digital landscape.
Who this course is for:
- This cybersecurity course is designed with the beginner in mind, offering an entry point into the world of digital security. As a student, you are not required to have an extensive background in cybersecurity or IT; The course assumes no prior knowledge of cybersecurity concepts, making it accessible to those who are taking their first steps into this field. Through a carefully crafted curriculum, you'll gradually build a strong foundation by learning about cyber threats, network components, hacker personas, and practical preventative measures.
User Reviews
Rating
Raphael Asghar
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 56
- duration 4:45:20
- Release Date 2024/02/14