Industrial SCADA and ITOT from Cyber Security and Zero Trust
Alexandru Serghie
1:35:03
Description
Overview about making SCADA and ITOT more secure for Cyber Security threats using Zero Trust techniues
What You'll Learn?
- Learn concepts for building a secure SCADA from Cybersecurity point of view
- Define Zero Trust objective and implementation
- Detail on how to secure the network to overcome risks that nobody wants in SCADA and ITOT
- Examples and practices will help achieve world wide standard of security and compliance
Who is this for?
What You Need to Know?
More details
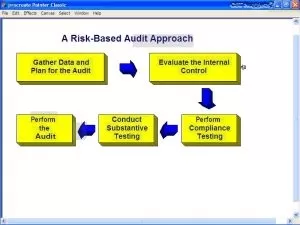
DescriptionIn this course, I will give an overview on how to design and implement highly secure SCADA platforms. This course can be a good start point for beginners and also I hope will be interesting to follow even for experts in the field. The theory from this course will surely need adaptation over time while new threats will appear.
The course follows zero trust techniques that I am also using in my daily activities. They are very important because older frameworks which contains even methods like just unplugging cable and considering it more secure. methods that was proven in practice to be a really bad one.
This course is intended to share the knowledge I gathered in many years of experience. I will happily accept discussions invites and debates and maybe they will me and also this course to improve while we all improve the security of our systems.
This will not be the definite containing all and have the direct and proven path to success. I can't say enough, cyber security needs to evolve over time at same rate or better than vulnerabilities evolves. Our lives start to depend more end more on IT and OT is just a part that usually we don't easily see with our own eyes but believe me, you don't want an OTÂ system to be hacked and used in malicious activities.
Who this course is for:
- Engineers, Network and Infrastructure, System and Operations, Managers, Architects
In this course, I will give an overview on how to design and implement highly secure SCADA platforms. This course can be a good start point for beginners and also I hope will be interesting to follow even for experts in the field. The theory from this course will surely need adaptation over time while new threats will appear.
The course follows zero trust techniques that I am also using in my daily activities. They are very important because older frameworks which contains even methods like just unplugging cable and considering it more secure. methods that was proven in practice to be a really bad one.
This course is intended to share the knowledge I gathered in many years of experience. I will happily accept discussions invites and debates and maybe they will me and also this course to improve while we all improve the security of our systems.
This will not be the definite containing all and have the direct and proven path to success. I can't say enough, cyber security needs to evolve over time at same rate or better than vulnerabilities evolves. Our lives start to depend more end more on IT and OT is just a part that usually we don't easily see with our own eyes but believe me, you don't want an OTÂ system to be hacked and used in malicious activities.
Who this course is for:
- Engineers, Network and Infrastructure, System and Operations, Managers, Architects
User Reviews
Rating
Alexandru Serghie
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 54
- duration 1:35:03
- Release Date 2024/01/05