How to Hack The Box To Your OSCP (The Extra Boxes)
Vonnie Hudson
4:14:43
Description
Go Beyond Root: Pop The Box and Build Real Detections
What You'll Learn?
- How to execute 20 MITRE ATT&CK Tools, Techniques and Procedures!
- How to use over 30 modern attack tools!
- How to setup the PERFECT modern hacking rig
- How to finally FEEL like a confident cybersecurity professional
Who is this for?
More details
DescriptionAre you ready to feel the fun of KNOWINGÂ how to hack?
In this course you will learn how to build a modern hacking lab.
You'll learn how to master the latest tools and attacker tradecraft for compromise victim environments.
You'll finally feel the pleasure and freedom of knowing what you're talking about.
I had a BLASTÂ creating this course for you guys and I'm so excited to share all the awesome with you.
In this course you will learn:
ping (for recon)
nmap
rustscan
whatweb + Wappalyzer
Burp Browser (why you should say NO to FoxyProxy!)
feroxbuster
kerbrute
ldp
ldapsearch
crackmapexec
smbclient
How to install Impact from scratch (because you know... it always breaks)
getTGT
GetUserSPNs
What the heck a SPN is anyway! You'll learn that - finally
hashcat
Silver Tickets
ticketer
How to manually convert passwords into NTLMÂ hashes
SQLÂ Commands
How to build a reverse shell in Powershell
rlwrap
netcat
iconv
xxd
base64
PEAS-ng (winPEAS)
Powershell Remoting
evil-winrm
Reverse Engineering .NETÂ Binaries
Wireshark
Insecure Deserialization
ysoserial
JuicyPotatoNG
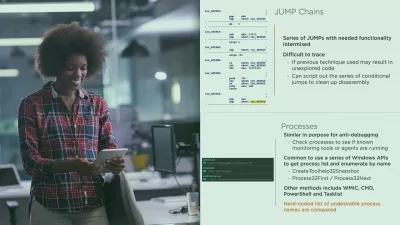
Persistence Mechanisms
Beyond Root: Threat Hunting the Attack
Beyond Root: Mitigations
Seriously! This is the best course I've ever made on hacking. It's the combination of all my experience jam packed into one tiddy little course.
You'll also get:
Hacking links and resources
Complete commands to copy and paste directly into your terminal!
So what are you waiting for?
Why are you still reading?
Enroll now and change your life.
Let's go!
Who this course is for:
- New SOC Analysts
- New Penetration Testers
- New Red Teamers
- New Blue Team Defenders
- Help Desk Analysts (wanting to get into cyber)
- Network Admins, Sys Admins and Network Engineers (wanting to get into cyber)
- Cybersecurity Managers (who want to know how the bad guy compromise environments)
Are you ready to feel the fun of KNOWINGÂ how to hack?
In this course you will learn how to build a modern hacking lab.
You'll learn how to master the latest tools and attacker tradecraft for compromise victim environments.
You'll finally feel the pleasure and freedom of knowing what you're talking about.
I had a BLASTÂ creating this course for you guys and I'm so excited to share all the awesome with you.
In this course you will learn:
ping (for recon)
nmap
rustscan
whatweb + Wappalyzer
Burp Browser (why you should say NO to FoxyProxy!)
feroxbuster
kerbrute
ldp
ldapsearch
crackmapexec
smbclient
How to install Impact from scratch (because you know... it always breaks)
getTGT
GetUserSPNs
What the heck a SPN is anyway! You'll learn that - finally
hashcat
Silver Tickets
ticketer
How to manually convert passwords into NTLMÂ hashes
SQLÂ Commands
How to build a reverse shell in Powershell
rlwrap
netcat
iconv
xxd
base64
PEAS-ng (winPEAS)
Powershell Remoting
evil-winrm
Reverse Engineering .NETÂ Binaries
Wireshark
Insecure Deserialization
ysoserial
JuicyPotatoNG
Persistence Mechanisms
Beyond Root: Threat Hunting the Attack
Beyond Root: Mitigations
Seriously! This is the best course I've ever made on hacking. It's the combination of all my experience jam packed into one tiddy little course.
You'll also get:
Hacking links and resources
Complete commands to copy and paste directly into your terminal!
So what are you waiting for?
Why are you still reading?
Enroll now and change your life.
Let's go!
Who this course is for:
- New SOC Analysts
- New Penetration Testers
- New Red Teamers
- New Blue Team Defenders
- Help Desk Analysts (wanting to get into cyber)
- Network Admins, Sys Admins and Network Engineers (wanting to get into cyber)
- Cybersecurity Managers (who want to know how the bad guy compromise environments)
User Reviews
Rating
Vonnie Hudson
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 25
- duration 4:14:43
- Release Date 2022/12/06