How RATs and Crypters work Ethical Hacking
Kishan Patel
52:40
Description
How remote access tools work properly with crypters
What You'll Learn?
- Fundamentals of Hacking
- Fundamentals of Cybersecurity
- Fundamentals of Malware Analysis
- Fundamentals of Ratting
Who is this for?
What You Need to Know?
More details
DescriptionIn this course, we will be teaching the fundamentals of remote access tools. Many Ethical hackers wish to learn something more beyond CEH. We will teach you how Remote Access tools work and which are the most successful ones and we will dive deep in the intro to crypters. We will teach you how to create FUD files and test them in a safe education environment with proper labs. We will teach you the important of VPS.
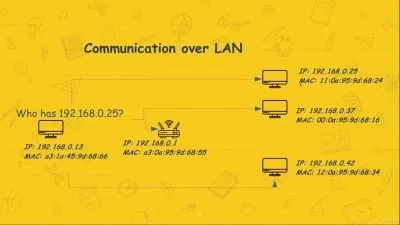
In ethical hacking, It is important to learn how to hack a machine. It can be done graphically and manually. In this course we will be teaching graphically, which means we will be using tools and softwares to generate the files we need to create instead of creating them manually which can take time. Also by using graphically, we have more powerful tools so we can get the most out of our skills.
We will guide you on how RATS work. We will create malware from the tools and learn how to make them FUD - Fully UnDetectable. Almost all malware created gets recognized by good Anti Virus. We will learn how to bypass it with a very good crypter.
Hope you enjoy the course.
Who this course is for:
- Beginner Hacking Course
In this course, we will be teaching the fundamentals of remote access tools. Many Ethical hackers wish to learn something more beyond CEH. We will teach you how Remote Access tools work and which are the most successful ones and we will dive deep in the intro to crypters. We will teach you how to create FUD files and test them in a safe education environment with proper labs. We will teach you the important of VPS.
In ethical hacking, It is important to learn how to hack a machine. It can be done graphically and manually. In this course we will be teaching graphically, which means we will be using tools and softwares to generate the files we need to create instead of creating them manually which can take time. Also by using graphically, we have more powerful tools so we can get the most out of our skills.
We will guide you on how RATS work. We will create malware from the tools and learn how to make them FUD - Fully UnDetectable. Almost all malware created gets recognized by good Anti Virus. We will learn how to bypass it with a very good crypter.
Hope you enjoy the course.
Who this course is for:
- Beginner Hacking Course
User Reviews
Rating
Kishan Patel
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 4
- duration 52:40
- English subtitles has
- Release Date 2022/11/17