Hardening Linux Security - Cybersecurity Compliance 2024
Nadeem Muhammad Ali
1:33:55
Description
Core underlying approach all Linux Professionals ought to watch and safeguard their Linux as a Strongbox predominantly.
What You'll Learn?
- How To Lock and Unlock Users Account in Linux Easily
- Locking Down Linux Servers with “sudo” Command | The Principle of Least Privilege
- Exploiting - SSH PuTTY login Brute-Force
- 19 Tips - Securing SSH, Installing, Enabling, & Heavy-Handed
- Secure your Linux Boxes with 3 Steps to Implement SSH Key-Based Authentication - 100% Secure
- Configure Fail2Ban - Setup an IPS To Protect and Blocking "LINUX/ UNIX" from Network Attacks
Who is this for?
What You Need to Know?
More details
DescriptionLinux is a widely used and popular operating system known for its stability, flexibility, and security. However, even with its built-in security features, Linux systems can still be vulnerable to security breaches.
This training covers how to improve the security of your Linux (Ubuntu, CentOS, RHEL) Boxes, whether you are newly built or auditing your existing Linux boxes.
This training covers the fundamentals of principal security to prevent all sorts of Internal and External attackers which we normally overlook.
Get Ready to Hands-On in:
How To Lock and Unlock Users Account in Linux Easily - 10 Minutes Professional Tactic.
To securely lock, disable, and unlock user's accounts in Linux Serves. After watching this video you can manage your Linux Users as this is part of managing users' principles, you can professionally manage user accounts in your Linux VPS Servers, hosting servers, corporate Linux servers, SSH servers, etc.
Locking Down Linux Servers with “sudo†command | the principle of least privilege.
We’ve been using the sudo in every Linux server's distro to run or execute commands with elevated privileges or you can say with root (administrator) rights. In fact, sudo usage took a deeper look when you are “Managing Users and Permissionsâ€.
Therefore, I won’t go into too much detail regarding sudo here, but some things bear repeating as sudo directly impacts security.
Exploiting - SSH PuTTY login Brute-Force - Cyber Security Compliance 2023
In this video, I will specifically talk about how to brute force SSH logins and passwords in the same way that hackers do, along with how to permanently fix those gaps or security countermeasures without thwarting and losing any configuration. I am exposing how easy is to brute force any SSH connection and choke or launch a DoS attack only if you remain unprotected or fail to follow the best practices to secure your SSH protocol or connection.
19 Tips - Securing SSH, Installing, Enabling, & Heavy-handed
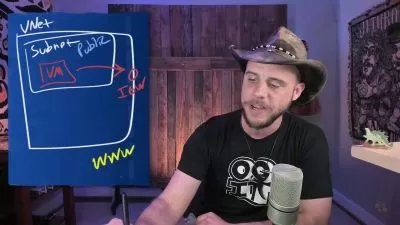
In this stirring lecture, we will address essential security settings in, Secure Shell Protocol aka SSH, which is a cryptographic network communication protocol that permits secure communication and data exchange between two devices over an unsecured network.
Today everything is managing remotely is significantly imperative, whether you are hosting your Linux servers or a seasoned systems administrator who has the responsibility to manage Linux boxes remotely, and the most important is to secure your SSH service from every likely internal and external attack.
Secure your Linux Boxes - 3 Steps to Implement SSH Key-Based Authentication - 100% Secure
In this lecture, we will talk about, Secure Shell Protocol “also known as†SSH, which is a cryptographic network communication protocol that permits secure communication and data exchange between two devices over an unsecured network.
The Secure Shell (SSH) is still the de facto way of connecting to remote Linux servers and various network devices. Rather than losing importance, its uses have increased with the greater reliance on automation technologies such as Ansible, cPanel/WHM, Kubernetes, docker containerization, etc.
Fail2Ban - Setup an IPS To Protect and Blocking "LINUX/ UNIX" from Network Attacks
Fail2Ban, an intrusion prevention framework. Written in Python, it is designed to prevent almost all Linux services from brute-force attacks. Also prevent brute force SSH logins and passwords in the same way that hackers do, along with how to permanently fix those gaps or security countermeasures without thwarting and losing any configuration.
We can set up Fail2Ban to provide brute-force protection for SSH on our server, this will ensure that the server is secure from brute-force attacks and it also allows us to monitor the strength of the brute-force attacks in regards to the number of authentication attempts that are being made.
Who this course is for:
- Anyone Managing Linux Boxes Remotely (SSH)
- Cybersecurity Professionals
- Software Developers or Engineers
- System Administrators and Network Engineers
- Anyone in Information Technology Systems
- Anyone who want to improve their security posture
Linux is a widely used and popular operating system known for its stability, flexibility, and security. However, even with its built-in security features, Linux systems can still be vulnerable to security breaches.
This training covers how to improve the security of your Linux (Ubuntu, CentOS, RHEL) Boxes, whether you are newly built or auditing your existing Linux boxes.
This training covers the fundamentals of principal security to prevent all sorts of Internal and External attackers which we normally overlook.
Get Ready to Hands-On in:
How To Lock and Unlock Users Account in Linux Easily - 10 Minutes Professional Tactic.
To securely lock, disable, and unlock user's accounts in Linux Serves. After watching this video you can manage your Linux Users as this is part of managing users' principles, you can professionally manage user accounts in your Linux VPS Servers, hosting servers, corporate Linux servers, SSH servers, etc.
Locking Down Linux Servers with “sudo†command | the principle of least privilege.
We’ve been using the sudo in every Linux server's distro to run or execute commands with elevated privileges or you can say with root (administrator) rights. In fact, sudo usage took a deeper look when you are “Managing Users and Permissionsâ€.
Therefore, I won’t go into too much detail regarding sudo here, but some things bear repeating as sudo directly impacts security.
Exploiting - SSH PuTTY login Brute-Force - Cyber Security Compliance 2023
In this video, I will specifically talk about how to brute force SSH logins and passwords in the same way that hackers do, along with how to permanently fix those gaps or security countermeasures without thwarting and losing any configuration. I am exposing how easy is to brute force any SSH connection and choke or launch a DoS attack only if you remain unprotected or fail to follow the best practices to secure your SSH protocol or connection.
19 Tips - Securing SSH, Installing, Enabling, & Heavy-handed
In this stirring lecture, we will address essential security settings in, Secure Shell Protocol aka SSH, which is a cryptographic network communication protocol that permits secure communication and data exchange between two devices over an unsecured network.
Today everything is managing remotely is significantly imperative, whether you are hosting your Linux servers or a seasoned systems administrator who has the responsibility to manage Linux boxes remotely, and the most important is to secure your SSH service from every likely internal and external attack.
Secure your Linux Boxes - 3 Steps to Implement SSH Key-Based Authentication - 100% Secure
In this lecture, we will talk about, Secure Shell Protocol “also known as†SSH, which is a cryptographic network communication protocol that permits secure communication and data exchange between two devices over an unsecured network.
The Secure Shell (SSH) is still the de facto way of connecting to remote Linux servers and various network devices. Rather than losing importance, its uses have increased with the greater reliance on automation technologies such as Ansible, cPanel/WHM, Kubernetes, docker containerization, etc.
Fail2Ban - Setup an IPS To Protect and Blocking "LINUX/ UNIX" from Network Attacks
Fail2Ban, an intrusion prevention framework. Written in Python, it is designed to prevent almost all Linux services from brute-force attacks. Also prevent brute force SSH logins and passwords in the same way that hackers do, along with how to permanently fix those gaps or security countermeasures without thwarting and losing any configuration.
We can set up Fail2Ban to provide brute-force protection for SSH on our server, this will ensure that the server is secure from brute-force attacks and it also allows us to monitor the strength of the brute-force attacks in regards to the number of authentication attempts that are being made.
Who this course is for:
- Anyone Managing Linux Boxes Remotely (SSH)
- Cybersecurity Professionals
- Software Developers or Engineers
- System Administrators and Network Engineers
- Anyone in Information Technology Systems
- Anyone who want to improve their security posture
User Reviews
Rating
Nadeem Muhammad Ali
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 8
- duration 1:33:55
- Release Date 2024/07/25