Governance, Risk, and Compliance for CompTIA Security+
Christopher Rees
2:37:46
Description
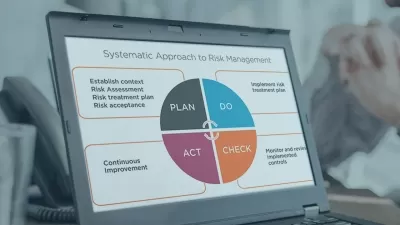
Proper governance, compliance, and risk assessment are an important part of any organization’s overall success. This course will teach you how to implement proper controls, assess risk, and limit your company’s exposure.
What You'll Learn?
Regulations, privacy, compliance, and ensuring your customer’s data is secure are becoming increasingly important while at the same time becoming increasingly complex. As new regulations are introduced, a company’s responsibilities continue to increase. In this course, Governance, Risk, and Compliance for CompTIA Security+, you’ll learn to properly assess your company’s risk across all facets of the organization. First, you’ll explore the various types of controls that can be put in place to limit exposure. Next, you’ll discover several methodologies, frameworks, and best practices needed to develop policy and ensure compliance. Finally, you’ll learn how to create a business impact analysis and properly classify data, along with the technologies required to safeguard that data. When you’re finished with this course, you’ll have the skills and knowledge of risk management and compliance needed to ensure your organization is properly governing employee and customer data, complying with local, state, and federal regulations, and properly assessing risk.
More details
User Reviews
Rating
Christopher Rees
Instructor's Courses
Pluralsight
View courses Pluralsight- language english
- Training sessions 108
- duration 2:37:46
- level preliminary
- English subtitles has
- Release Date 2023/02/07