GIAC Security Essentials (GSEC)
Focused View
11:42:03
68 View
001 Introduction.mp4
01:25
002 - Module introduction.mp4
00:43
003 - Learning objectives.mp4
00:31
004 - 1.1 Network Protocols and Reference Models.mp4
05:29
005 - 1.2 IPv4 vs. IPv6 and ICMP vs. ICMPv6.mp4
11:17
006 - 1.3 Layer 4 Protocols.mp4
13:01
007 - 1.4 Setting up a Lab Environment.mp4
09:54
008 - 1.5 Using tcpdump and Wireshark.mp4
07:12
009 - Learning objectives.mp4
00:26
010 - 2.1 CIA Triad and Parkerian Hexad.mp4
02:54
011 - 2.2 Categories and Types of Controls.mp4
04:24
012 - 2.3 Understanding the Enterprise Architecture.mp4
01:54
013 - 2.4 Introduction to Threat Enumeration.mp4
02:57
014 - Learning objectives.mp4
00:19
015 - 3.1 Access Control Concepts.mp4
13:03
016 - 3.2 Password Management.mp4
06:50
017 - 3.3 Introduction to Password Cracking.mp4
09:06
018 - Learning objectives.mp4
00:36
019 - 4.1 Network Topologies and Zones.mp4
08:27
020 - 4.2 Overview of Network Devices and Hardening.mp4
14:23
021 - 4.3 Survey of Security Devices and Wireshark.mp4
13:51
022 - 4.4 Configuring Firewalls at Amazon Web Services.mp4
11:57
023 - 4.5 Exploring a Palo Alto Networks Next-Generation Firewall.mp4
10:24
024 - 4.6 Examining a Classic IPS Sensor Device.mp4
05:47
025 - Learning objectives.mp4
00:21
026 - 5.1 Introducing the Center for Internet Security (CIS).mp4
03:36
027 - 5.2 Overview of CIS Controls.mp4
05:56
028 - 5.3 Samples and Case Studies.mp4
05:35
029 - Learning objectives.mp4
00:26
030 - 6.1 The Evolution of IEEE 802.11 Security.mp4
11:09
031 - 6.2 WPA3 Security.mp4
03:37
032 - 6.3 PAN, NFC, and 5G Concepts.mp4
04:12
033 - 6.4 The Internet of Things (IoT).mp4
05:08
034 - Module introduction.mp4
00:31
035 - Learning objectives.mp4
00:20
036 - 7.1 Common Attack Types.mp4
16:01
037 - 7.2 CryptoMalware.mp4
08:45
038 - 7.3 Defensive Strategies.mp4
08:33
039 - Learning objectives.mp4
00:22
040 - 8.1 Defense in Depth Overview and Strategies.mp4
05:00
041 - 8.2 Core Security Strategies.mp4
02:52
042 - 8.3 Defensible Network Architectures.mp4
02:42
043 - Learning objectives.mp4
00:19
044 - 9.1 Overview of Active Defense.mp4
04:58
045 - 9.2 Active Defense Techniques.mp4
03:34
046 - 9.3 Active Defense Tools.mp4
07:53
047 - Learning objectives.mp4
00:26
048 - 10.1 Overview of Endpoint Security.mp4
04:29
049 - 10.2 Host-based Intrusion Detection.mp4
02:12
050 - 10.3 Host-based Intrusion Prevention.mp4
02:41
051 - 10.4 Next-generation Endpoint Security Solutions.mp4
03:04
052 - Module introduction.mp4
00:26
053 - Learning objectives.mp4
00:24
054 - 11.1 Overview of Logging.mp4
07:47
055 - 11.2 Logging System Setup and Configuration.mp4
03:37
056 - 11.3 Logging Analysis Fundamentals.mp4
04:08
057 - 11.4 Core SIEM Activities.mp4
04:36
058 - Learning objectives.mp4
00:25
059 - 12.1 Overview of Vulnerability Management.mp4
06:31
060 - 12.2 Network Scanning.mp4
08:45
061 - 12.3 Using Xenmap and Yersinia.mp4
12:57
062 - 12.4 Penetration Testing.mp4
12:17
063 - Learning objectives.mp4
00:29
064 - 13.1 Overview of Virtualization and VM Security.mp4
05:27
065 - 13.2 Cloud Models and Value Proposition.mp4
14:23
066 - 13.3 Common Attacks Against Cloud Services.mp4
06:57
067 - 13.4 Introduction to Microsoft Azure IAM.mp4
10:52
068 - Module introduction.mp4
00:43
069 - Learning objectives.mp4
00:24
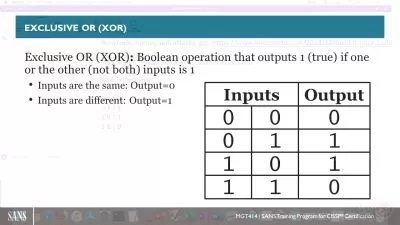
070 - 14.1 Overview of Cryptology and Cryptosystems.mp4
05:36
071 - 14.2 Cryptographic Hashing.mp4
06:34
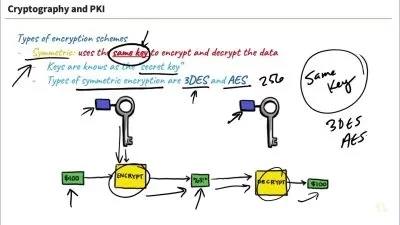
072 - 14.3 Symmetric Key Cryptography.mp4
03:24
073 - 14.4 Asymmetric Key Cryptography.mp4
02:48
074 - Learning objectives.mp4
00:22
075 - 15.1 Digital Signatures.mp4
04:08
076 - 15.2 IPsec.mp4
12:08
077 - 15.3 SSL TLS.mp4
03:16
078 - 15.4 Public Key Infrastructure.mp4
11:03
079 - Learning objectives.mp4
00:27
080 - 16.1 The Importance of Written Security Policies.mp4
03:18
081 - 16.2 Standards, Guidelines, and Procedures.mp4
03:02
082 - 16.3 Acceptable Use Policies.mp4
01:29
083 - 16.4 Survey of Sample Policies.mp4
08:29
084 - Learning objectives.mp4
00:22
085 - 17.1 Overview of Risk Management.mp4
06:13
086 - 17.2 Risk Management Best Practices.mp4
07:25
087 - 17.3 Threat Assessment, Analysis, and Reporting.mp4
12:25
088 - Learning objectives.mp4
00:22
089 - 18.1 Fundamentals of Incident Handling.mp4
03:17
090 - 18.2 Six Step Incident Response Process.mp4
06:26
091 - 18.3 Conducting a Forensic Investigation.mp4
10:59
092 - Learning objectives.mp4
00:24
093 - 19.1 Business Continuity Planning (BCP).mp4
05:23
094 - 19.2 Business Impact Analysis (BIA).mp4
02:41
095 - 19.3 Backups and Restoration.mp4
03:20
096 - 19.4 Disaster Recovery Planning (DRP).mp4
07:30
097 - Module introduction.mp4
00:29
098 - Learning objectives.mp4
00:21
099 - 20.1 Operating Systems and Services.mp4
04:01
100 - 20.2 Windows Workgroups vs. Domains.mp4
09:49
101 - 20.3 Windows-as-a-Service.mp4
04:22
102 - Learning objectives.mp4
00:23
103 - 21.1 NTFS and Shared Folder Permissions.mp4
05:29
104 - 21.2 Registry Keys and REGEDIT.EXE.mp4
04:02
105 - 21.3 Windows Privileges.mp4
04:18
106 - 21.4 Overview of BitLocker Drive Encryption.mp4
05:40
107 - Learning objectives.mp4
00:25
108 - 22.1 Security Templates and SCA Snap-in.mp4
05:31
109 - 22.2 Understanding Group Policy Objects.mp4
05:31
110 - 22.3 Administrative Users, AppLocker, and User Account Control.mp4
04:11
111 - Learning objectives.mp4
00:23
112 - 23.1 Azure and High Availability.mp4
10:10
113 - 23.2 Configuring Azure VM Attributes.mp4
08:39
114 - 23.3 Microsoft Azure Active Directory (MAAD).mp4
13:12
115 - Learning objectives.mp4
00:20
116 - 24.1 Windows PowerShell.mp4
09:55
117 - 24.2 Administrative Tools and Utilities.mp4
08:51
118 - 24.3 Windows Auditing and Forensics.mp4
07:54
119 - Module introduction.mp4
00:30
120 - Learning objectives.mp4
00:26
121 - 25.1 Comparing Linux Operating Systems.mp4
06:34
122 - 25.2 Mobile Device Security.mp4
04:27
123 - 25.3 Linux Shells and Kernels.mp4
13:12
124 - 25.4 Linux Permissions.mp4
08:53
125 - 25.5 Linux User Accounts.mp4
07:58
126 - Learning objectives.mp4
00:24
127 - 26.1 Starting Services at Boot Time.mp4
07:10
128 - 26.2 Configuration Management Tools.mp4
04:39
129 - 26.3 Linux Kernel Security.mp4
06:17
130 - 26.4 Linux System Enhancers.mp4
05:03
131 - Learning objectives.mp4
00:22
132 - 27.1 Configuring and Monitoring Logs.mp4
06:12
133 - 27.2 Leveraging the Auditd tool.mp4
03:17
134 - 27.3 Linux Security Utilities.mp4
06:08
135 Summary.mp4
01:04
More details
User Reviews
Rating
average 0
Focused display

LiveLessons
View courses LiveLessonsPearson's video training library is an indispensable learning tool for today's competitive job market. Having essential technology training and certifications can open doors for career advancement and life enrichment. We take learning personally. We've published hundreds of up-to-date videos on wide variety of key topics for Professionals and IT Certification candidates. Now you can learn from renowned industry experts from anywhere in the world, without leaving home.
- language english
- Training sessions 135
- duration 11:42:03
- Release Date 2023/11/03