GenAI & Cybersecurity: Learn OpenAI Text Embedding
Peter Alkema,Irlon Terblanche
1:30:02
Description
Unlock the Power of AI in Cybersecurity: From Basics to Advanced Threat Detection Techniques
What You'll Learn?
- Understand the limitations and capabilities of AI in cybersecurity
- Implement text embeddings and vectors for cybersecurity applications
- Develop skills to use AI tools for detecting and mitigating cyber threats
- Gain proficiency in advanced AI techniques to enhance cybersecurity measures
Who is this for?
What You Need to Know?
More details
DescriptionHow can we harness the power of AI to protect our digital world?
Imagine you’re the Chief Information Security Officer (CISO) at a large corporation. Each day, you’re inundated with alerts about potential security breaches, phishing attempts, and malware. The sheer volume is overwhelming, and traditional methods are proving insufficient. The question looms large: “How can I efficiently protect my organization against these evolving cyber threats?†Enter AI and cybersecurity.
In this course, you’ll follow the story of Julia, a CISO who faced this exact challenge. Her organization was a prime target for cybercriminals due to its vast amount of sensitive data. Despite having a robust security team, they struggled to keep up with the sophisticated attacks. Julia knew there had to be a better way, and that’s when she discovered the transformative power of AI.
The journey begins with an exploration of AI’s role in cybersecurity. You’ll learn about the fundamental principles of AI and how these can be applied to detect and mitigate threats in real-time. The course covers the limitations of AI, ensuring you have a balanced view of its capabilities and potential pitfalls.
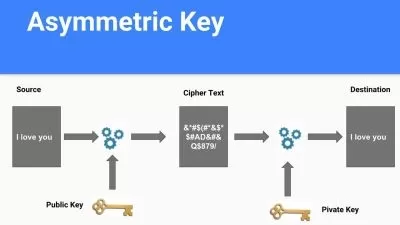
Next, we dive into the technical aspects, starting with text embeddings and vectors. These powerful tools enable AI systems to understand and process language, a crucial aspect in identifying phishing emails, spam, and other text-based threats. You’ll gain hands-on experience in implementing these techniques, turning theoretical knowledge into practical skills.
Julia’s story continues as she integrates AI into her security infrastructure. You’ll learn alongside her as she navigates the challenges of setting up and configuring AI tools. This section covers everything from environment setup to data preparation, giving you a comprehensive understanding of the technical requirements and best practices.
The real magic happens when we move to advanced AI techniques. You’ll explore how to create featurized representations and 3D models, which allow for more sophisticated analysis and detection of threats. These methods provide a deeper insight into the data, enabling more accurate predictions and faster responses.
One of the highlights of the course is the development of interactive dashboards. Just as Julia did, you’ll learn to create visualizations that bring your data to life, making it easier to identify patterns and anomalies. This skill is invaluable in communicating complex information to stakeholders and making informed decisions quickly.
Throughout the course, you’ll work on real-world projects that mirror the challenges faced by cybersecurity professionals. These projects are designed to reinforce your learning and build confidence in applying AI to your own security challenges.
By the end of the course, like Julia, you’ll be equipped with a powerful toolkit to defend against cyber threats. You’ll have a thorough understanding of how AI can enhance your cybersecurity measures and the practical skills to implement these techniques effectively.
So, are you ready to take on the cybercriminals with the power of AI? Join us in this transformative journey and become a leader in the field of AI and cybersecurity.
Who this course is for:
- Cybersecurity professionals seeking to leverage AI in their work
- Data scientists and AI enthusiasts interested in cybersecurity applications
- IT professionals aiming to enhance their understanding of AI in security contexts
- Students and researchers exploring the intersection of AI and cybersecurity
How can we harness the power of AI to protect our digital world?
Imagine you’re the Chief Information Security Officer (CISO) at a large corporation. Each day, you’re inundated with alerts about potential security breaches, phishing attempts, and malware. The sheer volume is overwhelming, and traditional methods are proving insufficient. The question looms large: “How can I efficiently protect my organization against these evolving cyber threats?†Enter AI and cybersecurity.
In this course, you’ll follow the story of Julia, a CISO who faced this exact challenge. Her organization was a prime target for cybercriminals due to its vast amount of sensitive data. Despite having a robust security team, they struggled to keep up with the sophisticated attacks. Julia knew there had to be a better way, and that’s when she discovered the transformative power of AI.
The journey begins with an exploration of AI’s role in cybersecurity. You’ll learn about the fundamental principles of AI and how these can be applied to detect and mitigate threats in real-time. The course covers the limitations of AI, ensuring you have a balanced view of its capabilities and potential pitfalls.
Next, we dive into the technical aspects, starting with text embeddings and vectors. These powerful tools enable AI systems to understand and process language, a crucial aspect in identifying phishing emails, spam, and other text-based threats. You’ll gain hands-on experience in implementing these techniques, turning theoretical knowledge into practical skills.
Julia’s story continues as she integrates AI into her security infrastructure. You’ll learn alongside her as she navigates the challenges of setting up and configuring AI tools. This section covers everything from environment setup to data preparation, giving you a comprehensive understanding of the technical requirements and best practices.
The real magic happens when we move to advanced AI techniques. You’ll explore how to create featurized representations and 3D models, which allow for more sophisticated analysis and detection of threats. These methods provide a deeper insight into the data, enabling more accurate predictions and faster responses.
One of the highlights of the course is the development of interactive dashboards. Just as Julia did, you’ll learn to create visualizations that bring your data to life, making it easier to identify patterns and anomalies. This skill is invaluable in communicating complex information to stakeholders and making informed decisions quickly.
Throughout the course, you’ll work on real-world projects that mirror the challenges faced by cybersecurity professionals. These projects are designed to reinforce your learning and build confidence in applying AI to your own security challenges.
By the end of the course, like Julia, you’ll be equipped with a powerful toolkit to defend against cyber threats. You’ll have a thorough understanding of how AI can enhance your cybersecurity measures and the practical skills to implement these techniques effectively.
So, are you ready to take on the cybercriminals with the power of AI? Join us in this transformative journey and become a leader in the field of AI and cybersecurity.
Who this course is for:
- Cybersecurity professionals seeking to leverage AI in their work
- Data scientists and AI enthusiasts interested in cybersecurity applications
- IT professionals aiming to enhance their understanding of AI in security contexts
- Students and researchers exploring the intersection of AI and cybersecurity
User Reviews
Rating
Peter Alkema
Instructor's CoursesIrlon Terblanche
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 31
- duration 1:30:02
- Release Date 2024/08/12