Gen (Generative) AI for Cybercrime Defense and Cybersecurity
Diwakar Thakore
5:31:23
Description
Harnessing GenAI to Safeguard Against Cyber Threats: A Comprehensive Guide to Cybercrime Defense and Cybersecurity
What You'll Learn?
- Understand the role of GenAI in modern cybersecurity.
- Apply AI-powered techniques to detect, analyze, and respond to cyber threats.
- Implement GenAI-driven tools to maintain and improve an organization’s security posture.
- Guide teams with automated, AI-driven recommended actions to strengthen defenses
- Utilize AI to enhance real-time threat detection, behavioral analysis, and anomaly detection.
- Integrate AI-generated insights into existing security frameworks for improved decision-making.
- Explore AI-powered tools for threat hunting, automated incident response, and adaptive security analytics.
- Understand the integration of GenAI into next-generation firewalls and endpoint security systems.
- Understand the ethical implications and risks associated with the use of GenAI in cybersecurity.
- Promote responsible and transparent use of AI in cybersecurity frameworks
- Gain insight into emerging trends in AI and cybersecurity, preparing for the next generation of cyber threats.
- . In the second half, gain foundational cybersecurity literacy, covering key concepts like cybercrime types, social engineering, and advanced cybersecurity
- Learn how to recognize, prevent, and respond to common cyber threats both in personal and organizational contexts.
- Differentiate between various types of cybercriminals and their motivations.
- Recognize different forms of malware and their functionalities
- Understand the importance of basic security measures.
- . Implement key security practices such as updating systems and installing security software.
- Recognize and address vulnerabilities related to social engineering.
- Set up multi-factor authentication for various accounts.
- Apply guidelines for secure usage of personal devices
- Implement best practices for secure email and internet usage.
- Implement preventive measures to mitigate cyber threats.
- Develop a cybersecurity action plan for personal or organizational use.
- Complete quizzes, assignments, and scenario analyses to solidify understanding.
- Apply course learnings to real-world scenarios in cybersecurity operations.
Who is this for?
What You Need to Know?
More details
DescriptionIn a world where cyber threats are rapidly evolving, traditional defenses are no longer enough.
The first half of the course is designed specifically for professionals looking to harness the power of Generative AI to tackle modern cyber threats. From improving security posture management to automating complex security operations, this course provides a hands-on deep dive into how AI can be a game-changer in your organization's cyber defense strategy.
What You’ll Learn:
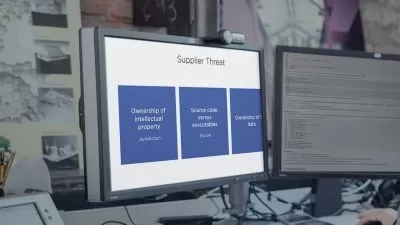
GenAI for Cyber Defense: Discover how Generative AI enhances threat detection, response, and security orchestration across various cybersecurity layers.
Advanced Automation: Master the automation of key tasks like vulnerability management, SSL certificate handling, and detection rule generation, streamlining your cybersecurity operations.
Orchestration & Posture Management: Gain insights into using AI to guide staff with recommended actions, automate processes, and manage security controls across complex environments.
Threat Intelligence & Response: Learn how to accelerate threat detection, analyze real-time intelligence, and automate incident response and remediation for faster resolutions.
In the latter half of the course, we return to the essentials with the Cybersecurity Literacy Program, a foundational module designed for anyone interested in building a strong security baseline. This section covers the fundamentals of cybercrime defense, empowering you to recognize and protect against everyday cyber threats.
Through video lectures, real-world case studies, practical exercises, and interactive learning, you will develop the skills necessary to stay ahead in today’s high-stakes cybersecurity landscape.
This course is ideal for cybersecurity professionals, IT managers, and anyone responsible for defending organizational assets from cyber threats.
This course is also for students, professionals, homemakers, small business owners, or corporate employees, who are looking to safeguard their digital presence and online life .
Together, we will harness the power of GenAI and comprehensive cybersecurity literacy to create a robust, future-proof defense.
Who this course is for:
- Individuals working in IT security roles who want to enhance their skills with the latest GenAI techniques for detecting and mitigating cyber threats.
- Professionals responsible for managing enterprise networks and maintaining security posture who are interested in automating processes and improving threat detection using AI.
- People with a passion for AI who want to explore its practical applications in cybersecurity and how it can help defend against complex cyber threats.
- Cyber Defense Teams, Security Consultants, Business Leaders and Decision Makers , IT Students and New Graduates
In a world where cyber threats are rapidly evolving, traditional defenses are no longer enough.
The first half of the course is designed specifically for professionals looking to harness the power of Generative AI to tackle modern cyber threats. From improving security posture management to automating complex security operations, this course provides a hands-on deep dive into how AI can be a game-changer in your organization's cyber defense strategy.
What You’ll Learn:
GenAI for Cyber Defense: Discover how Generative AI enhances threat detection, response, and security orchestration across various cybersecurity layers.
Advanced Automation: Master the automation of key tasks like vulnerability management, SSL certificate handling, and detection rule generation, streamlining your cybersecurity operations.
Orchestration & Posture Management: Gain insights into using AI to guide staff with recommended actions, automate processes, and manage security controls across complex environments.
Threat Intelligence & Response: Learn how to accelerate threat detection, analyze real-time intelligence, and automate incident response and remediation for faster resolutions.
In the latter half of the course, we return to the essentials with the Cybersecurity Literacy Program, a foundational module designed for anyone interested in building a strong security baseline. This section covers the fundamentals of cybercrime defense, empowering you to recognize and protect against everyday cyber threats.
Through video lectures, real-world case studies, practical exercises, and interactive learning, you will develop the skills necessary to stay ahead in today’s high-stakes cybersecurity landscape.
This course is ideal for cybersecurity professionals, IT managers, and anyone responsible for defending organizational assets from cyber threats.
This course is also for students, professionals, homemakers, small business owners, or corporate employees, who are looking to safeguard their digital presence and online life .
Together, we will harness the power of GenAI and comprehensive cybersecurity literacy to create a robust, future-proof defense.
Who this course is for:
- Individuals working in IT security roles who want to enhance their skills with the latest GenAI techniques for detecting and mitigating cyber threats.
- Professionals responsible for managing enterprise networks and maintaining security posture who are interested in automating processes and improving threat detection using AI.
- People with a passion for AI who want to explore its practical applications in cybersecurity and how it can help defend against complex cyber threats.
- Cyber Defense Teams, Security Consultants, Business Leaders and Decision Makers , IT Students and New Graduates
User Reviews
Rating
Diwakar Thakore
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 47
- duration 5:31:23
- Release Date 2024/12/21