Fortinet FortiSOAR From Zero To Hero
Hatem Metwally
12:50:12
Description
Learn state-of-the-art Security Product that must have in any SOC arsenal
What You'll Learn?
- Security Orchestration, Automation and Response (SOAR)
- FortiSOAR
- Use Cases
- Hands-ON
- SOAR
- Playbooks
- Incident Response
- Cyber Threat Intelligence
Who is this for?
What You Need to Know?
More details
DescriptionFortiSOAR is a holistic Security Orchestration, Automation and Response (SOAR) workbench, designed for SOC teams to efficiently respond to the ever-increasing influx of alerts, repetitive manual processes, and shortage of resources. It pulls together all of organization's tools, helps unify operations and reduces alert fatigue, context switching, and the mean time to respond to incidents.
FortiSOAR is extremely a flexible product with many important and usefull features, which along with outstanding customer support brings SOC environment to next level.
FortiSOAR provides the ability to customize GUI and affect SOC working environment effectively. "Less clicks is better!" Robastic Integration with 3rd party tools - many API based connectors with example playbooks which can be easily adopted for company needs. Customer Support - great attitude, professionality, very customer oriented.
Through baby steps you will learn Fortinet FortiSOAR important topics that include but not limited to the following:
Part I - FortiSOAR Basics
==================
Lecture 1: Introduction
Lecture 2: Installation
Lecture 3: GUI Demystified - part1
Lecture 4: GUI Demystified - part2
Lecture 5: Foundations and Architecture
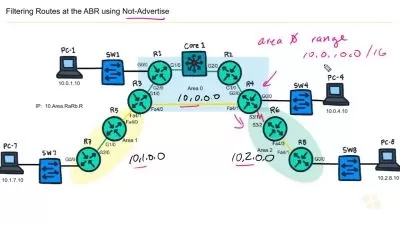
Lecture 6: Ingesting FortiSIEM Incidents into FortiSOAR
Lecture 7: Ingesting Microsoft Exchange Office365 messages into FortiSOAR
Lecture 8: Installing and Configuring VirusTotal Connector
Lecture 9: Dashboards, Templates and Widgets
Lecture 10: Module Templates
Lecture 11: Searches and Filters
Lecture 12: Application Editor
Part II - Playbooks
=============
Lecture 13: Playbooks introduction & Trigger Steps
Lecture 14: Playbooks Core steps
Lecture 15: Playbooks Evaluate steps
Lecture 16: Playbooks Execute steps and others
Lecture 17: Designing Our First playbook - Reassign Analyst
Lecture 18: Perform IP Enrichment for Newly Added IOC
Lecture 19: Create Critical Alert for Bad IOC, Approve, and [Manually] Block on Firewall
Lecture 20: Create Critical Alert for Bad IOC, Approve, and [Auto] Blocking on Firewall
Lecture 21: Generalize IOC Lookup/Auto-Block Playbook for Bad IP and URL
Lecture 22: Perform IP Enrichment from 2 CTIs & Manipulate IBM XForce Results using Code Snippet Step
Lecture 23: Increasing the Resiliency of IP Enrichment
Lecture 24: Automate IOC Extraction From CTI Advisories
Lecture 25: Playbooks Nesting and Parameters Passing
Lecture 26: Playbooks Nesting and Parameters Passing - Part2 (Hands-On)
Appendix
=======
Lecture 27: CLI and Troubleshooting
Lecture 28: Avoid Playbooks Running Forever Condition
Enroll and gain a new competitive skill that is booming and highly demaded nowadays in the Information Security domain.
Who this course is for:
- Network Security Specialists & Administrators
- SOC Operators & Analysts
- Information Security Sepcialists
FortiSOAR is a holistic Security Orchestration, Automation and Response (SOAR) workbench, designed for SOC teams to efficiently respond to the ever-increasing influx of alerts, repetitive manual processes, and shortage of resources. It pulls together all of organization's tools, helps unify operations and reduces alert fatigue, context switching, and the mean time to respond to incidents.
FortiSOAR is extremely a flexible product with many important and usefull features, which along with outstanding customer support brings SOC environment to next level.
FortiSOAR provides the ability to customize GUI and affect SOC working environment effectively. "Less clicks is better!" Robastic Integration with 3rd party tools - many API based connectors with example playbooks which can be easily adopted for company needs. Customer Support - great attitude, professionality, very customer oriented.
Through baby steps you will learn Fortinet FortiSOAR important topics that include but not limited to the following:
Part I - FortiSOAR Basics
==================
Lecture 1: Introduction
Lecture 2: Installation
Lecture 3: GUI Demystified - part1
Lecture 4: GUI Demystified - part2
Lecture 5: Foundations and Architecture
Lecture 6: Ingesting FortiSIEM Incidents into FortiSOAR
Lecture 7: Ingesting Microsoft Exchange Office365 messages into FortiSOAR
Lecture 8: Installing and Configuring VirusTotal Connector
Lecture 9: Dashboards, Templates and Widgets
Lecture 10: Module Templates
Lecture 11: Searches and Filters
Lecture 12: Application Editor
Part II - Playbooks
=============
Lecture 13: Playbooks introduction & Trigger Steps
Lecture 14: Playbooks Core steps
Lecture 15: Playbooks Evaluate steps
Lecture 16: Playbooks Execute steps and others
Lecture 17: Designing Our First playbook - Reassign Analyst
Lecture 18: Perform IP Enrichment for Newly Added IOC
Lecture 19: Create Critical Alert for Bad IOC, Approve, and [Manually] Block on Firewall
Lecture 20: Create Critical Alert for Bad IOC, Approve, and [Auto] Blocking on Firewall
Lecture 21: Generalize IOC Lookup/Auto-Block Playbook for Bad IP and URL
Lecture 22: Perform IP Enrichment from 2 CTIs & Manipulate IBM XForce Results using Code Snippet Step
Lecture 23: Increasing the Resiliency of IP Enrichment
Lecture 24: Automate IOC Extraction From CTI Advisories
Lecture 25: Playbooks Nesting and Parameters Passing
Lecture 26: Playbooks Nesting and Parameters Passing - Part2 (Hands-On)
Appendix
=======
Lecture 27: CLI and Troubleshooting
Lecture 28: Avoid Playbooks Running Forever Condition
Enroll and gain a new competitive skill that is booming and highly demaded nowadays in the Information Security domain.
Who this course is for:
- Network Security Specialists & Administrators
- SOC Operators & Analysts
- Information Security Sepcialists
User Reviews
Rating
Hatem Metwally
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 28
- duration 12:50:12
- English subtitles has
- Release Date 2024/01/04