F5 BIG-IP LTM Specialist: Architect, Set up, Deploy (Exam 301a) Online Training
Bob Salmans
11:31:23
More details
This intermediate F5 BIG-IP LTM Specialist: Architect, Set up, Deploy (Exam 301a) training prepares learners to efficiently configure, secure and optimize F5 devices with a focus on robust application delivery and traffic management.
F5 Networks is a technology company that's world-renowned for its application and application delivery networking services. F5 hardware and software solutions aren't cheap, but they are powerful, versatile and secure. Security professionals who learn how to navigate and configure F5 technology are extremely valuable to companies that depend on F5 already.
This course covers the skills and knowledge necessary to configure, manage and secure F5's local traffic manager (LTM). For experienced network security professionals, expanding your skills into F5 management is a strong investment in your future – as well as your salary.
After completing this F5 training you'll know how to efficiently configure, secure and optimize F5 devices with a focus on robust application delivery and traffic management.
For IT managers, this F5 training can be used to onboard new network security admins, curated into individual or team training plans, or as a F5 reference resource.
F5 BIG-IP LTM Specialist: What You Need to Know
This F5 BIG-IP LTM Specialist training has videos that cover topics including:
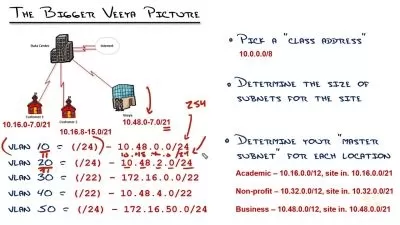
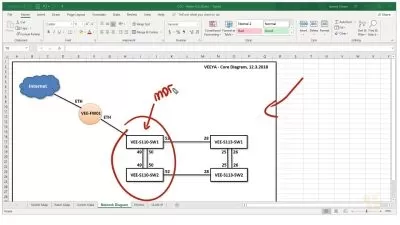
- Configure and optimize F5 devices for traffic distribution and optimal performance
- Manage access control, authentication and authorization policies on F5 devices
- Implement load balancing strategies and traffic prioritizations
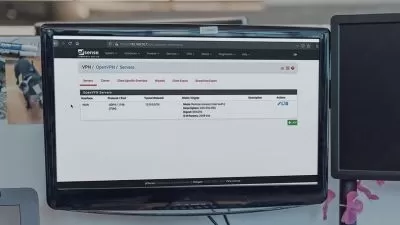
- Configure and optimize SSL/TLS credentialing
- Understand and enforce compliance standards and policies
Who Should Take F5 BIG-IP LTM Specialist Training?
This F5 BIG-IP LTM Specialist: Architect, Set up, Deploy (Exam 301a) training is considered associate-level F5 training, which means it was designed for network security admins. This F5 BIG-IP Local Traffic Manager skills course is designed for network security admins with three to five years of experience with enterprise network security.
New or aspiring network security admins. The F5 credential this course prepares you for, BIG-IP LTM Specialist, has a prerequisite (F5 Certified Big-IP Administrator). So although the content of this course is valuable to new network security admins, the credential itself could be difficult to attain right away. You should still take the course if the skills and knowledge would be valuable for your job, though – you don't need to take the cert exam to take the course.
Experienced network security admins. Once you're at a certain point in your career, expanding your familiarity into different hardware and software configurations is a good way to improve your marketability and job opportunities. F5 is a great candidate for where you spend your time and energy if you're not already familiar with their operations. And for network security administrators with a few years of experience, this course is a great way to prepare for the LTM Specialist if you've already earned the F5-CA.
User Reviews
Rating
Bob Salmans
Instructor's CoursesI love seeing and helping people advance through life. It's my small part in contributing to the advancement of the security community.
Bob got his start in IT after enlisting in the United States Navy and being assigned to a network engineer role. He brings seven years of IT training experience to CBT Nuggets along with over 20 years of IT experience. Bob was a security team lead for a managed services provider before joining CBTN. In his spare time, he enjoys spending time with his family, cooking, and metal and woodworking.
Certifications: Microsoft MCSE, Cisco CCNP, Cisco CCDP, Cisco CCNA Security, CISSP, CCSP, GPEN, CISA, CISM, CompTIA Security+, CompTIA CySA+, CompTIA Pentest+
Areas of expertise: Information security, networking, active directory, Linux

CBT Nuggets
View courses CBT Nuggets- language english
- Training sessions 101
- duration 11:31:23
- English subtitles has
- Release Date 2024/06/25