Ethical Hacking: Web Enumeration
Peter A
41:07
Description
Scan your target before hacking
What You'll Learn?
- Manual Scanning
- Scanning website for hidden directories
- Scanning website for hidden files
- Scanning for hidden subdomains
- Scanning WordPress blogs
- Scanning Servers
Who is this for?
What You Need to Know?
More details
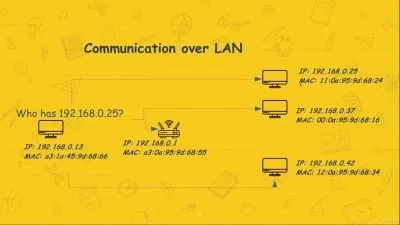
Descriptionweb enumeration is a techniques hackers use when targeting web servers and web sites. When attempting to hack an application with a vulnerabilty, you first have to find out what files, subdomains or directories the applications are vulnerable to. On top of that, you may find hidden files that could give you access to the file server. Perhaps you can access SSHÂ keys, pdfs or find hidden directories. It might be there is a vulnerable app running on one of the sub domains. There are many ways the server could be accessible and web enumeration is the first step.
In this course you will learn how to scan for directories, files, subdomains but also how to scan blogs made with wordpress for vulnerabilities. While you can do manual scanning, that quickly becomes cumbersome. In this course we explain how you can do automated scans on your target server.
This is a beginners course for those interested in Ethical Hacking or Cyber Security. You don't need any prior knowledge when doing this course, but you should have Kali Linux at hands. Kali Linux is a computer system that contains many hacking tools, sometimes it's simply called Kali. It can be downloaded for free as a Live USBÂ or Virtualbox image, there's also a cloud option. While you can install the tools manually, there are so many hacking tools that it's easier to use a dedicated Linux system like Kali.
Who this course is for:
- Beginner Ethical Hackers
- Software Developers
- Sysadmins
- Devops
web enumeration is a techniques hackers use when targeting web servers and web sites. When attempting to hack an application with a vulnerabilty, you first have to find out what files, subdomains or directories the applications are vulnerable to. On top of that, you may find hidden files that could give you access to the file server. Perhaps you can access SSHÂ keys, pdfs or find hidden directories. It might be there is a vulnerable app running on one of the sub domains. There are many ways the server could be accessible and web enumeration is the first step.
In this course you will learn how to scan for directories, files, subdomains but also how to scan blogs made with wordpress for vulnerabilities. While you can do manual scanning, that quickly becomes cumbersome. In this course we explain how you can do automated scans on your target server.
This is a beginners course for those interested in Ethical Hacking or Cyber Security. You don't need any prior knowledge when doing this course, but you should have Kali Linux at hands. Kali Linux is a computer system that contains many hacking tools, sometimes it's simply called Kali. It can be downloaded for free as a Live USBÂ or Virtualbox image, there's also a cloud option. While you can install the tools manually, there are so many hacking tools that it's easier to use a dedicated Linux system like Kali.
Who this course is for:
- Beginner Ethical Hackers
- Software Developers
- Sysadmins
- Devops
User Reviews
Rating
Peter A
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 8
- duration 41:07
- Release Date 2024/03/12