Ethical Hacking: SQL Injection
Malcolm Shore
1:39:34
Description
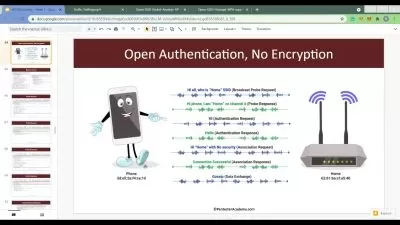
SQL injections are a common way to gain unauthorized access to web applications and extract data from them. In this course, instructor Malcolm Shore shows you the SQL command language and how it is used by attackers to craft SQL Injections. Malcolm begins with commonly encountered relational databases and the basics of the SQL command language. Then he focuses on advanced SQL commands that may be used by attackers to achieve SQL injections. Malcolm explains how to use a simple Python script and how an SQL injection changes the backend SQL query. Then he demonstrates how SQL injections could be used to exploit some testing targets. Malcolm steps through the process of automating SQL injection exploits, then finishes with advice on how to continue to hone your skills as a penetration tester.
More details
User Reviews
Rating
Malcolm Shore
Instructor's Courses
Linkedin Learning
View courses Linkedin Learning- language english
- Training sessions 22
- duration 1:39:34
- Release Date 2023/01/18