Ethical Hacking: Mobile Devices and Platforms
Malcolm Shore
1:56:13
Description
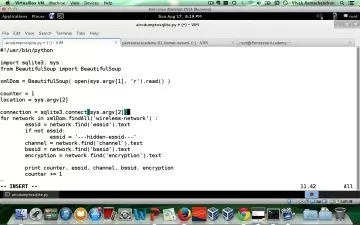
Mobile devices are used for our most sensitive transactions, including email, banking, and social media. But they have a unique set of vulnerabilities, which hackers are all too willing to exploit. Security professionals need to know how to close the gaps and protect devices, data, and users from attacks. Join cybersecurity expert Malcolm Shore as he explores the two dominant mobile operating systems, Android and iOS, and shows ways to protect devices through analysis and testing. Watch this course to review the basics of mobile OS models, the toolsets you need for testing, and the techniques for detecting and preventing the majority of security flaws.
These methods are recognized by EC Council as integral part of those looking to earn their Certified Ethical Hacker certification. The complete CEH BOK can be found at https://www.eccouncil.org/Certification/certified-ethical-hacker/CEH-What-You-Will-Learn.
More details
User Reviews
Rating
Malcolm Shore
Instructor's Courses
Linkedin Learning
View courses Linkedin Learning- language english
- Training sessions 30
- duration 1:56:13
- Release Date 2023/01/09