Ethical Hacking: Hacking Wireless Networks
Dale Meredith
3:36:11
Description
Wireless provides one of the biggest attack vectors for hackers. This course will teach you how to secure wireless networks needed for the CEH 312-50 exam.
What You'll Learn?
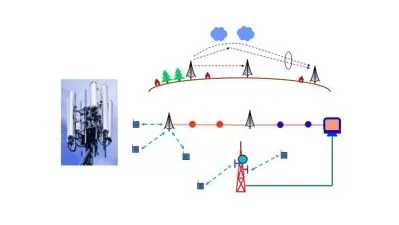
Wireless technologies have changed our world, but it’s also given hackers another attack vector . In this course, Ethical Hacking: Wireless Hacking, you’ll learn to look at your wireless infrastructures the way attackers do and what you can do to protect your organization using the skills of an Ethical Hacker. First, you’ll explore the concepts of wireless technologies, from transmission types to antenna types. Next, you’ll discover the threats and methodologies used by hackers to attack your networks. Finally, you’ll learn how to [protect your wireless infrastructures with countermeasures. When you’re finished with this course, you’ll have the skills and knowledge of ethical hacking needed for the CEH 312-50 exam.
More details
User Reviews
Rating
Dale Meredith
Instructor's Courses
Pluralsight
View courses Pluralsight- language english
- Training sessions 50
- duration 3:36:11
- level average
- English subtitles has
- Release Date 2023/01/08