Ethical Hacking: Evading IDS, Firewalls, and Honeypots
Malcolm Shore
2:19:56
Description
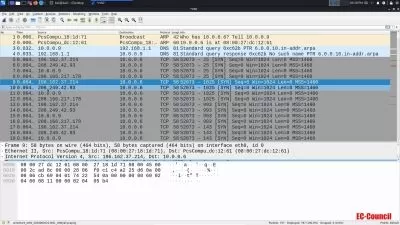
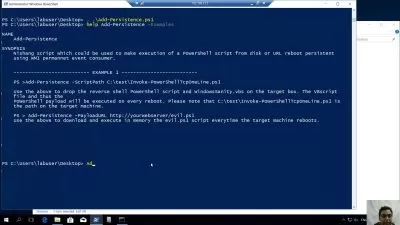
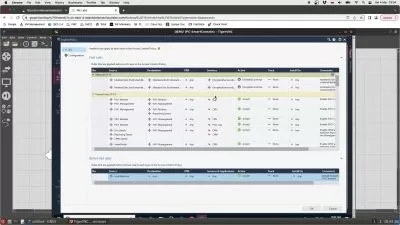
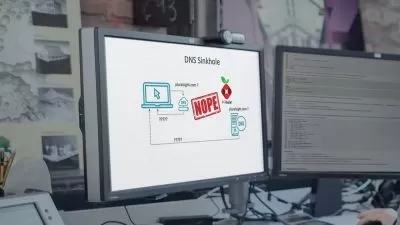
Ethical hacking—testing to see if an organization's network is vulnerable to outside attacks—is a desired skill for many IT security professionals. In this course, cybersecurity expert Malcolm Shore prepares you to take your first steps into testing client defenses. Malcolm provides you with an overview of firewall technology, detailing how firewalls work in both Windows and Linux, as well as how to set up a firewall simulation in a GNS3 network. Next, he goes over web application firewalls, API gateway threat mitigation solutions, and how to use honeypots to detect intruders. Malcolm also explains evasion techniques like exotic scanning and tunneling through DNS. Finally, he covers the main ways to manage a suspected intrusion, including how to use the Security Onion intrusion detection system (IDS).
Note: The topics covered in this course are drawn from the Evading IDS, Firewalls, and Honeypots competency in the Certified Ethical Hacker (CEH) body of knowledge.
More details
User Reviews
Rating
Malcolm Shore
Instructor's Courses
Linkedin Learning
View courses Linkedin Learning- language english
- Training sessions 39
- duration 2:19:56
- English subtitles has
- Release Date 2024/09/22