Ethical Hacking: Cloud Computing
Daniel Lachance
2:30:56
Description
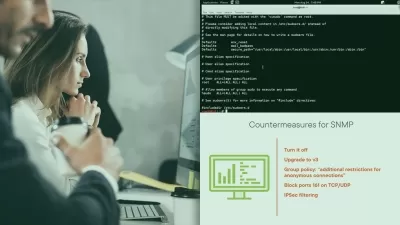
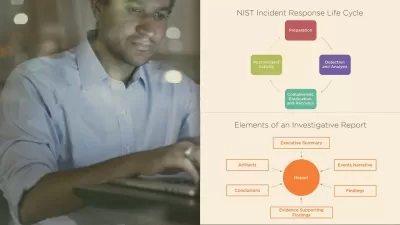
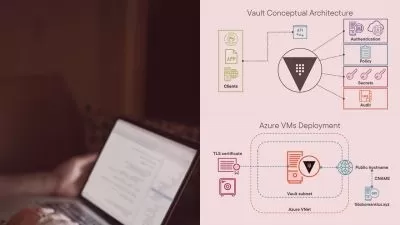
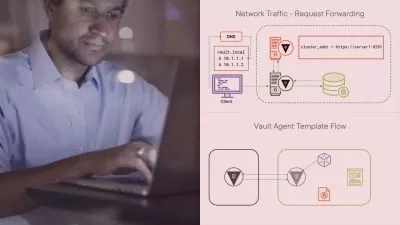
Cloud resource hardening and monitoring can go a long way in mitigating cloud-based attacks. In this course, which maps to the Cloud Computing module from the Certified Ethical Hacker (CEH) Body of Knowledge, instructor Daniel Lachance explores how many types of resources including virtual machines, databases, and storage can be deployed in a cloud computing environment. Daniel covers how cloud computing relates to the different phases of ethical hacking, as well as common breaches and security threats that can affect overall cloud security. He also goes over cloud identity management, keeping your IT systems running in the cloud even in the event of an attack or security breach, using artificial intelligence (AI) and machine learning (ML) to identify anomalies that might indicate that your system is compromised, test-taking strategies, and much more.
More details
User Reviews
Rating
Daniel Lachance
Instructor's Courses
Linkedin Learning
View courses Linkedin Learning- language english
- Training sessions 30
- duration 2:30:56
- English subtitles has
- Release Date 2023/07/02