Ethical Hacking And Penetration Testing Crash Course
KANCHARANA CHANDRAKANTH
2:42:57
Description
Become a Cybersecurity Expert: Master Penetration Testing & Ethical Hacking - A Crash Course - 2023 NEW!
What You'll Learn?
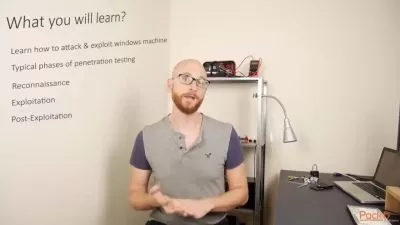
- Learn Ethical Hacking from scratch & All 5 phases of Penetration Testing
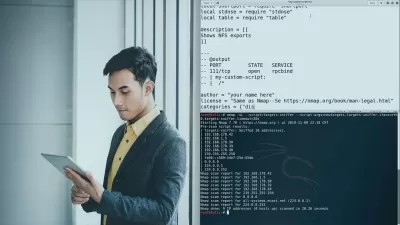
- Master Information Gathering and Footprinting
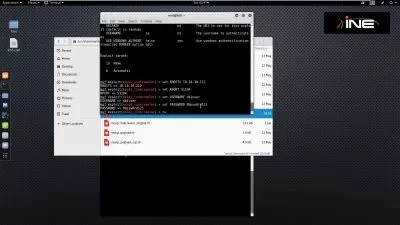
- Learn Advance Nmap Scanning and Enumeration
- Learn how to perform Vulnerability Analysis
- Learn how to gain access to Windows Systems
- Learn how to Escalate Privileges from Local User to Admin
- Create Persistence on target machines
- Learn Practical Demonstrations of Password Cracking(SSH), Social Engineering, SQL Injection, MAC Flooding, Session Misconfigurations
Who is this for?
What You Need to Know?
More details
DescriptionIn today's digital world, cybersecurity is more important than ever. Ethical hackers play a vital role in identifying and fixing security vulnerabilities before malicious actors can exploit them.
Our comprehensive Master Penetration Testing and Ethical Hacking Crash Course is designed to take you from a complete novice to a skilled ethical hacker in no time. You'll learn about the latest hacking techniques and tools, and gain hands-on experience by working on real-world scenarios.
This course is perfect for anyone who wants to pursue a career in cybersecurity or simply learn more about how to protect themselves from cyberattacks.
More Than Just Theory: Hands-On Learning:
This course isn't just about theory; it's about putting your knowledge into action. Each lecture offers practical exercises, real-world examples, and the opportunity to hone your skills. You won't just understand the concepts; you'll also become proficient in their application.
For Whom is This Course?
Whether you're a budding cybersecurity enthusiast, a network administrator looking to bolster your skills, or an individual with a profound interest in technology and security, this course is tailored to your journey. It takes you from the very basics to the level of a proficient ethical hacker.
Embrace the Challenge: Enroll Today:
The world of ethical hacking beckons, and it's a realm where knowledge becomes power—the power to protect. Join us in the "Master Penetration Testing and Ethical Hacking Crash Course" course and embrace the challenge of securing the digital realm. Your adventure in ethical hacking starts here.
Don't wait; enroll today and take the first step towards becoming a guardian of the digital world. The future of cybersecurity awaits you.
Who this course is for:
- Beginners in Cybersecurity: Those new to the field looking for a structured, beginner-friendly introduction to ethical hacking concepts and techniques.
- IT Professionals: IT specialists and system administrators aiming to enhance their security skills, ensuring robust defense mechanisms for their networks and systems.
- Students and Enthusiasts: Students pursuing degrees in computer science or related fields, as well as anyone keen on cybersecurity as a hobby or potential career path.
- Professionals Seeking Certifications: Those preparing for industry-recognized certifications like Certified in Cybersecurity(CC), Certified Ethical Hacker (CEH) benefiting from practical hands-on training
In today's digital world, cybersecurity is more important than ever. Ethical hackers play a vital role in identifying and fixing security vulnerabilities before malicious actors can exploit them.
Our comprehensive Master Penetration Testing and Ethical Hacking Crash Course is designed to take you from a complete novice to a skilled ethical hacker in no time. You'll learn about the latest hacking techniques and tools, and gain hands-on experience by working on real-world scenarios.
This course is perfect for anyone who wants to pursue a career in cybersecurity or simply learn more about how to protect themselves from cyberattacks.
More Than Just Theory: Hands-On Learning:
This course isn't just about theory; it's about putting your knowledge into action. Each lecture offers practical exercises, real-world examples, and the opportunity to hone your skills. You won't just understand the concepts; you'll also become proficient in their application.
For Whom is This Course?
Whether you're a budding cybersecurity enthusiast, a network administrator looking to bolster your skills, or an individual with a profound interest in technology and security, this course is tailored to your journey. It takes you from the very basics to the level of a proficient ethical hacker.
Embrace the Challenge: Enroll Today:
The world of ethical hacking beckons, and it's a realm where knowledge becomes power—the power to protect. Join us in the "Master Penetration Testing and Ethical Hacking Crash Course" course and embrace the challenge of securing the digital realm. Your adventure in ethical hacking starts here.
Don't wait; enroll today and take the first step towards becoming a guardian of the digital world. The future of cybersecurity awaits you.
Who this course is for:
- Beginners in Cybersecurity: Those new to the field looking for a structured, beginner-friendly introduction to ethical hacking concepts and techniques.
- IT Professionals: IT specialists and system administrators aiming to enhance their security skills, ensuring robust defense mechanisms for their networks and systems.
- Students and Enthusiasts: Students pursuing degrees in computer science or related fields, as well as anyone keen on cybersecurity as a hobby or potential career path.
- Professionals Seeking Certifications: Those preparing for industry-recognized certifications like Certified in Cybersecurity(CC), Certified Ethical Hacker (CEH) benefiting from practical hands-on training
User Reviews
Rating
KANCHARANA CHANDRAKANTH
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 31
- duration 2:42:57
- Release Date 2023/12/24