Denail Of Service Attacks (DoS) For Begginers
Focused View
6:26:23
97 View
1. Introduction.mp4
04:41
2. What is Denail of Service ATTACK.mp4
04:15
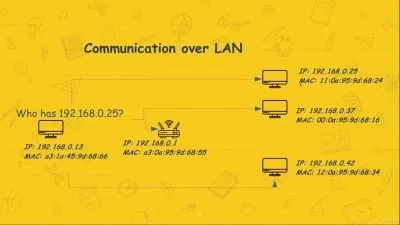
1. What is Computer Network.mp4
05:23
2. Major Components of Computer Network.mp4
07:44
3. Reference Model-1.mp4
10:45
4. Reference Model-2.mp4
03:06
5. Application Layer and Port Numbers.mp4
04:15
6. HTTP.mp4
13:26
7. FTP.mp4
04:34
8. SMTP.mp4
04:59
9. DNS.mp4
09:27
10. TCP AndUDP.mp4
11:26
11. IP.mp4
13:21
12. ROUTER.mp4
06:39
13. NAT.mp4
04:31
14. ICMP.mp4
05:57
15. DHCP.mp4
02:47
16. MAC.mp4
05:10
17. SWITCH.mp4
06:15
18. ARP.mp4
04:05
1. What is Denail of Service Attacks.mp4
04:15
2. Methods of Denail of Service Attacks.mp4
04:16
3. Signs of Denail of Service Attacks.mp4
04:01
4. DDos Attack.mp4
04:07
5. Types of Denail of Service Attacks.mp4
03:15
6. ICMP Flooding attacks.mp4
04:45
7. SYN Flooding Attacks.mp4
04:30
8. UDP Flooding Attacks.mp4
02:03
9. HTTP Flooding Attacks.mp4
03:17
10. Ping of Death Attacks.mp4
02:29
11. Smurf Attacks.mp4
02:49
12. Slowloris Attacks.mp4
03:46
13. Preventing Denail of Service Attacks.mp4
03:23
1. Lab Overview.mp4
03:56
2. Download and Install VMware.mp4
05:54
3. Downlaod and Install VirtualBox.mp4
03:19
4. Downlaod and Install Kali Linux.mp4
09:04
5. Download and Install Metasploitable 2.mp4
06:07
6. Downlaod and Install Windows 11 VM-1.mp4
03:26
7. Download and Install Windows 11 VM-2.mp4
04:23
8. Test the lab connectivity.mp4
08:09
1. Navigating File System.mp4
18:24
2. Users and Priviledges-1.mp4
09:33
3. Users and Priviledges-2.mp4
08:30
4. Networking Commands.mp4
14:02
5. Installing and Updating Tools.mp4
08:02
6. Controlling Kali Linux Services.mp4
05:13
7. Viewing, Creating and Editing Files.mp4
10:39
8. grep Command-1.mp4
12:41
9. grep Command-2.mp4
06:57
10. More Linux Commands.mp4
13:05
1. Downlaod and Install Slowloris tool-1.mp4
04:15
2. Download and Install Slowloris tool-2.mp4
04:01
3. Launch DoS attack using Slowloris.mp4
08:36
4. Download and Install Goldeneye Tool.mp4
03:26
5. Launch DDoS attack using Goldeneye.mp4
07:12
6. Launch SYN Flooding.mp4
08:26
7. Launch ICMP Flooding.mp4
06:28
8. Launch DoS attack (Land).mp4
04:31
9. Launch DDoS attack (Random Source).mp4
03:49
10. Launch Ping of Death Attack.mp4
04:33
More details
User Reviews
Rating
average 0
Focused display
Category

Udemy
View courses UdemyStudents take courses primarily to improve job-related skills.Some courses generate credit toward technical certification. Udemy has made a special effort to attract corporate trainers seeking to create coursework for employees of their company.
- language english
- Training sessions 61
- duration 6:26:23
- Release Date 2023/06/16