Defeating Anti-reverse Engineering and Anti-debugging Techniques
Josh Stroschein
1:53:40
Description
Anti-reverse engineering and anti-debugging techniques are often used by malware authors to disrupt or prevent analysis, helping them to avoid detection. This course will teach you effective strategies for detecting and defeating these techniques.
What You'll Learn?
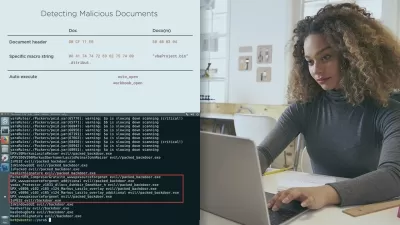
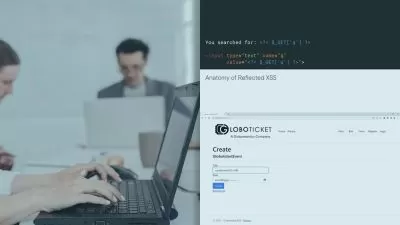
Anti-reverse engineering and anti-debugging techniques are often leveraged by malware authors to disrupt or prevent detailed analysis, helping them to avoid detection by even the most advanced security products. These efforts increase the odds that they will be successful in attacking an organization and can allow them to stay hidden within an organization for prolonged periods of time. In this course, Defeating Anti-reverse Engineering and Anti-debugging Techniques, you will gain the skills necessary to not only identify prevalent anti-analysis techniques, but also how to defeat them. First, you will gain insight into why malware authors employ such anti-analysis techniques and gain a deeper understanding of where to expect them. Next, you will dig deep into anti-analysis techniques used to disrupt both your static and dynamic analysis activities. You will get hands-on with identifying anti-disassembly techniques, control-flow obfuscation and hiding string and API calls. Then, you will learn how malware authors trick your debugger, employ code hiding techniques such as process hollowing and how they leverage shellcode to complicate analysis. Finally, you will explore techniques used to detect the presence of a sandbox, which leads to incomplete or inaccurate results and can throw off your analysis. Each module of this course will include in-depth demonstrations and hands-on labs utilizing real-world malware. By the end of this course, you will have the knowledge and skills to defeat anti-reversing and anti-debugging techniques used by the most sophisticated malware authors.
More details
User Reviews
Rating
Josh Stroschein
Instructor's Courses
Pluralsight
View courses Pluralsight- language english
- Training sessions 27
- duration 1:53:40
- level advanced
- Release Date 2023/12/06