Data Privacy, Governance, and Compliance: How to Share Your Data with Privacy Controls
Nishant Bhajaria
57:20
Description
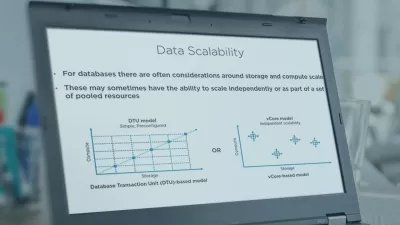
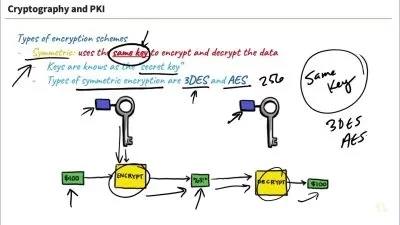
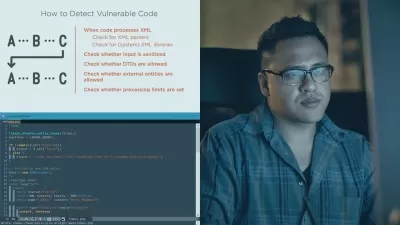
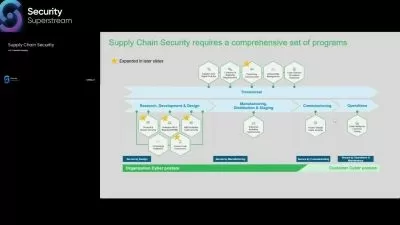
Companies that drive revenue and growth based on user engagement also face challenges sharing data. From re-identification to exfiltration to unmanaged access, data sharing presents several privacy risks. In this course, privacy and security executive Nishant Bhajaria helps data-driven innovators understand key technologies and players that are involved in the data sharing space. As part of a "shift left" governance strategy, find out how to perform a cost-benefit analysis around data sharing and its use cases. Learn to apply data-driven tests to measure privacy risks around data sharing. Explore ways to solve the privacy risks around data sharing at all levels: data, access, identity, transport, and storage. Contextualize data sharing in terms of user footprint digitally versus in real life. After this course, you will be able to enforce data protection policies throughout the data sharing process.
More details
User Reviews
Rating
Nishant Bhajaria
Instructor's Courses
Linkedin Learning
View courses Linkedin Learning- language english
- Training sessions 23
- duration 57:20
- Release Date 2023/04/27