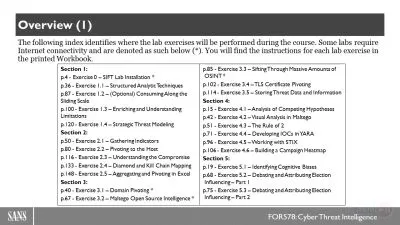
Cybersecurity Fundamentals for Beginners-Learning with Demos
Kshitij Joy (DB Alchemist Academy)
9:16:48
Description
For Beginners-Practical Approach to learning - Cyber Attacks, Cryptography, Encryption Algorithms, PKI,Networking Topics
What You'll Learn?
- Top 10 Cyber Attacks of 21st Century
- What is Cybersecurity ?
- What is CIA Triad ?
- Types of Cyber Attacks
- Demo: How attackers use Phishing Attack ?
- Demo: How to create a Sql Injection(SQLi) Attack
- Types of Hackers : Black Hat / White Hat / Grey Hat / Hacktivist
- What is Cryptography ?
- Understand Symmetric Encryption with an Example
- Demo:Asymmetric encryption using openssl
- Understanding of AES/DES Algorithms
- Understanding of RSA / DSA / ECDSA / Diffie-Hellman Algorithms with Demos
- What is PKI ?
- Demos for Digital Signature / Digital Certificate / Certificate Authority
- How to raise a CSR and sign the certificate
- A Primer on Networking and all important terms
- What is a Switch & a Router
- What is VLAN / IP Address / Subnetting / Subset Mask
- Demos on ARP / Network Packets / Traceroute
- Understanding of VPN / Firewall / DMZ / Proxy Server
- What is SSH/ TCP-IP
- What is SSL
- Understanding SSL Vs TLS
- Demo: Checking the Latest Stats on SSL/TLS
- What is mTLS
Who is this for?
What You Need to Know?
More details
DescriptionThis is a course that has been designed for the Beginners to the world of Cybersecurity and also experienced IT Professionals looking to learn the fundamentals of Cybersecurity , the entire learning will be based on demos and various practical.
* What is Cybersecurity ?
* Types of Cyber Attacks - Malware / Phishing / MITM / DDOS /SQLInjection
* Types of Hackers - Black Hat / White Hat / Grey Hat / Hacktivist
* Basics of Cryptography - History / Caesar's Cypher / Symmetric & Asymmetric Encryption
* Deep Dive into Various Algorithms - RSA / DSA / AES/ DES / ECDSA / Diffie-Hellman
* Public Key Infrastructure (PKI) - Digital Signature / Certificate Authority (CA) / Digital Certificate / Self Signed Certificate
* Networking Basics - IP Addressing / Subnetting / VPN / DMZ / Firewall / Proxy Server / Packet Switching
* Key Protocols - SSH / SSL / TCP/IP / TLS / mTLS
The details are as below:
1. Introduction
2. Top 10 Cyber Attacks of 21st Century
3. A Look at the Live Threats
4. Demand for CyberSecurity Skills
5. What is Cybersecurity ?
6. What is CIA Triad ?
7. Malware Attack
8. Phishing Attack
9. Demo: How attackers use Phishing Attack ?
10. Password Attack
11. Demo: A Dictionary Attack - Password Attack
12. Man-in-the-Middle Attack
13. Demo: MITM Attack using ARP Poisoning
14. SQL Injection Attack
15. Demo: How to create a Sql Injection(SQLi) Attack
16. Denial-of-Service Attack
17. Cryptojacking
18. White Hat Hacker
19. Black Hat Hacker
20. Grey Hat Hacker
21. Hacktivist
22. Script Kiddie
23. What is Cryptography ?
24. History of Cryptography
25. Understanding the Ceasar's Cypher
26. What is Symmetric Encryption
27. Understand Symmetric Encryption with an Example
28. Demo: Symmetric Encryption using openssl
29. What is Asymmetric Encryption
30. Understand Asymmetric Encryption - Confidentiality
31. Understand Asymmetric Encryption - Integrity & Authentication
32. Demo:Asymmetric encryption using openssl
33. Get an Understanding of Hybrid Encryption
34. What is Cipher Algorithm & Key
35. What is DES - Data Encryption Standard ?
36. What is AES : Advanced Encryption Standard
37. Which are the NIST Approved Asymmetric Algorithms ?
38. What is the RSA Algorithm ?
39. Understanding RSA Algorithm with Example
40. What is DSA Algorithm ?
41. What is Deffie-Hellman Algorithm ?
42. Understanding DH Algorithm with an Example
43. Understanding Calculations for DH Algorithm
44. What is Elliptic Curve Algorithm ?
45. Quick Comparison : RSA vs DSA vs ECDSA vs DH
46. What is PKI ?
47. What is a Hashing Algorithm
48. Demo: Hashing using openssl
49. What is a Message Digest
50. What is a Digital Signature ?
51. Understanding Digital Signature
52. What is a Certificate Authority -CA
53. Demo: Exploring the DigiCert Website
54. What is a Digital Certificate
55. Understanding Digital Certificate
56. Check a Real Certificate - Facebook
57. Protecting from MITM using Digital Certificate
58. What is a Self Signed Certificate ?
59. PEM Vs PKCS12
60. What is a Chain of Trust
61. Demo: Create a Self Signed Certificate / rootCA
62. Demo : Create a CSR
63. Demo: Sign a Certificate CSR
64. Main Artefacts for Networking
65. Understanding the OSI Model
66. What is a Switch ?
67. What is a Router ?
68. What is a VLAN
69. Decimal to Binary Conversion
70. Binary to Decimal Conversion
71. Understanding an IP address
72. What is Subnetting
73. What is Subnet Mask
74. What is ARP
75. Simulation to understand ARP
76. What is a Network Packet
77. How a Packet Travels from Source to Destination
78. Demo: traceroute to cnn
79. What is a VPN ?
80. Demo: Using a Software based VPN (NordVPN)
81. What is a Firewall ?
82. Role of a Proxy Server
83. What is a Perimeter Network or a DMZ
84. What is SSH
85. What is TCP/IP
86. What is SSL
87. Understanding SSL Vs TLS
88. Demo: Checking the Latest Stats on SSL/TLS
89. What is MTLS
Who this course is for:
- Cybersecurity Beginners / Experienced Professionals in IT wanting to understand the fundamentals of Cybersecurity in a Practical oriented learning
- The course also teaches all the important Networking Fundamentals as well.
This is a course that has been designed for the Beginners to the world of Cybersecurity and also experienced IT Professionals looking to learn the fundamentals of Cybersecurity , the entire learning will be based on demos and various practical.
* What is Cybersecurity ?
* Types of Cyber Attacks - Malware / Phishing / MITM / DDOS /SQLInjection
* Types of Hackers - Black Hat / White Hat / Grey Hat / Hacktivist
* Basics of Cryptography - History / Caesar's Cypher / Symmetric & Asymmetric Encryption
* Deep Dive into Various Algorithms - RSA / DSA / AES/ DES / ECDSA / Diffie-Hellman
* Public Key Infrastructure (PKI) - Digital Signature / Certificate Authority (CA) / Digital Certificate / Self Signed Certificate
* Networking Basics - IP Addressing / Subnetting / VPN / DMZ / Firewall / Proxy Server / Packet Switching
* Key Protocols - SSH / SSL / TCP/IP / TLS / mTLS
The details are as below:
1. Introduction
2. Top 10 Cyber Attacks of 21st Century
3. A Look at the Live Threats
4. Demand for CyberSecurity Skills
5. What is Cybersecurity ?
6. What is CIA Triad ?
7. Malware Attack
8. Phishing Attack
9. Demo: How attackers use Phishing Attack ?
10. Password Attack
11. Demo: A Dictionary Attack - Password Attack
12. Man-in-the-Middle Attack
13. Demo: MITM Attack using ARP Poisoning
14. SQL Injection Attack
15. Demo: How to create a Sql Injection(SQLi) Attack
16. Denial-of-Service Attack
17. Cryptojacking
18. White Hat Hacker
19. Black Hat Hacker
20. Grey Hat Hacker
21. Hacktivist
22. Script Kiddie
23. What is Cryptography ?
24. History of Cryptography
25. Understanding the Ceasar's Cypher
26. What is Symmetric Encryption
27. Understand Symmetric Encryption with an Example
28. Demo: Symmetric Encryption using openssl
29. What is Asymmetric Encryption
30. Understand Asymmetric Encryption - Confidentiality
31. Understand Asymmetric Encryption - Integrity & Authentication
32. Demo:Asymmetric encryption using openssl
33. Get an Understanding of Hybrid Encryption
34. What is Cipher Algorithm & Key
35. What is DES - Data Encryption Standard ?
36. What is AES : Advanced Encryption Standard
37. Which are the NIST Approved Asymmetric Algorithms ?
38. What is the RSA Algorithm ?
39. Understanding RSA Algorithm with Example
40. What is DSA Algorithm ?
41. What is Deffie-Hellman Algorithm ?
42. Understanding DH Algorithm with an Example
43. Understanding Calculations for DH Algorithm
44. What is Elliptic Curve Algorithm ?
45. Quick Comparison : RSA vs DSA vs ECDSA vs DH
46. What is PKI ?
47. What is a Hashing Algorithm
48. Demo: Hashing using openssl
49. What is a Message Digest
50. What is a Digital Signature ?
51. Understanding Digital Signature
52. What is a Certificate Authority -CA
53. Demo: Exploring the DigiCert Website
54. What is a Digital Certificate
55. Understanding Digital Certificate
56. Check a Real Certificate - Facebook
57. Protecting from MITM using Digital Certificate
58. What is a Self Signed Certificate ?
59. PEM Vs PKCS12
60. What is a Chain of Trust
61. Demo: Create a Self Signed Certificate / rootCA
62. Demo : Create a CSR
63. Demo: Sign a Certificate CSR
64. Main Artefacts for Networking
65. Understanding the OSI Model
66. What is a Switch ?
67. What is a Router ?
68. What is a VLAN
69. Decimal to Binary Conversion
70. Binary to Decimal Conversion
71. Understanding an IP address
72. What is Subnetting
73. What is Subnet Mask
74. What is ARP
75. Simulation to understand ARP
76. What is a Network Packet
77. How a Packet Travels from Source to Destination
78. Demo: traceroute to cnn
79. What is a VPN ?
80. Demo: Using a Software based VPN (NordVPN)
81. What is a Firewall ?
82. Role of a Proxy Server
83. What is a Perimeter Network or a DMZ
84. What is SSH
85. What is TCP/IP
86. What is SSL
87. Understanding SSL Vs TLS
88. Demo: Checking the Latest Stats on SSL/TLS
89. What is MTLS
Who this course is for:
- Cybersecurity Beginners / Experienced Professionals in IT wanting to understand the fundamentals of Cybersecurity in a Practical oriented learning
- The course also teaches all the important Networking Fundamentals as well.
User Reviews
Rating
Kshitij Joy (DB Alchemist Academy)
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 101
- duration 9:16:48
- Release Date 2023/09/10