Cyber Threat Intelligence
Christopher Nett
7:22:21
Description
Learn Cyber Threat Intelligence | Hands-on experience | Elevate your career to the next level
What You'll Learn?
- Understand typical behavior patterns of adversaries, enabling you to predict and mitigate potential security breaches.
- Learn to effectively identify and analyze a wide range of cyber threats and to enable threat-informed defenses.
- Comprehensive Understanding of MITRE ATT&CK
- Explore industry best practices around CTI
Who is this for?
What You Need to Know?
More details
DescriptionCyber Threat Intelligence (CTI) by Christopher Nett is a meticulously organized Udemy course designed for IT professionals aiming to master CTI to empower threat-informed defenses. This course systematically guides you from the basis to advanced concepts of CTI.
By mastering CTI, you're developing expertise in essential topics in today's cybersecurity landscape. Through this course, you'll develop expertise in CTI, a comprehensive topic widely recognized for understanding tactics, techniques and procedures of adversaries and defending against cyber threats.
This deep dive into CTI equips you with the skills necessary for a cutting-edge career in cybersecurity.
Key Benefits for you:
SOC Basics: Understand the foundational structures of Security Operations Centers and their role in cybersecurity.
Azure Basics: Gain essential knowledge of Microsoft Azure's infrastructure.
Zero Trust Basics: Learn the principles of the Zero Trust security model.
Intelligence: Explore the methods of collecting and analyzing data to predict and prevent threats.
CTI: Delve into the core techniques of Cyber Threat Intelligence to identify potential threats before they impact.
CTI Related Frameworks: Discover various frameworks that enhance the effectiveness of CTIÂ processes.
MITRE ATT&CK: Study this globally-accessible knowledge base of adversary tactics and techniques.
Threat Actors and Advanced Persistent Threats: Identify common adversaries in cyber warfare.
CTI Tools: Get hands-on experience with the tools that professionals use for CTI gathering and analysis.
CTI Platforms: Familiarize yourself with platforms specifically designed for managing and operationalizing CTI.
AI & CTI: Explore the intersection of Artificial Intelligence and CTI to enhance threat detection.
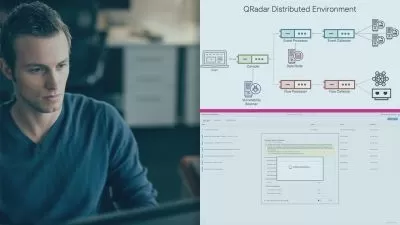
Case Study I - MISP on Azure: Analyze how the MISP threat intelligence platform can be implemented on Azure to manage CTI.
Case Study II: Researching APT41 with ATT&CK: Understand the approach to investigating the TTPs of APT41 using the MITRE ATT&CK framework.
Case Study III: Leveraging CTI in Microsoft Sentinel: See practical applications of CTI in enhancing Microsoft Sentinel's threat detection capabilities.
Case Study IV: Building a CTI Program: Learn from a comprehensive blueprint on setting up a successful CTI program within an organization.
Who this course is for:
- SOC Analyst
- Security Engineer
- Security Consultant
- Security Architect
- Security Manager
- CISO
- Red Team
- Blue Team
- Cybersecurity Professional
- Ethical Hacker
- Penetration Tester
- Incident Handler
Cyber Threat Intelligence (CTI) by Christopher Nett is a meticulously organized Udemy course designed for IT professionals aiming to master CTI to empower threat-informed defenses. This course systematically guides you from the basis to advanced concepts of CTI.
By mastering CTI, you're developing expertise in essential topics in today's cybersecurity landscape. Through this course, you'll develop expertise in CTI, a comprehensive topic widely recognized for understanding tactics, techniques and procedures of adversaries and defending against cyber threats.
This deep dive into CTI equips you with the skills necessary for a cutting-edge career in cybersecurity.
Key Benefits for you:
SOC Basics: Understand the foundational structures of Security Operations Centers and their role in cybersecurity.
Azure Basics: Gain essential knowledge of Microsoft Azure's infrastructure.
Zero Trust Basics: Learn the principles of the Zero Trust security model.
Intelligence: Explore the methods of collecting and analyzing data to predict and prevent threats.
CTI: Delve into the core techniques of Cyber Threat Intelligence to identify potential threats before they impact.
CTI Related Frameworks: Discover various frameworks that enhance the effectiveness of CTIÂ processes.
MITRE ATT&CK: Study this globally-accessible knowledge base of adversary tactics and techniques.
Threat Actors and Advanced Persistent Threats: Identify common adversaries in cyber warfare.
CTI Tools: Get hands-on experience with the tools that professionals use for CTI gathering and analysis.
CTI Platforms: Familiarize yourself with platforms specifically designed for managing and operationalizing CTI.
AI & CTI: Explore the intersection of Artificial Intelligence and CTI to enhance threat detection.
Case Study I - MISP on Azure: Analyze how the MISP threat intelligence platform can be implemented on Azure to manage CTI.
Case Study II: Researching APT41 with ATT&CK: Understand the approach to investigating the TTPs of APT41 using the MITRE ATT&CK framework.
Case Study III: Leveraging CTI in Microsoft Sentinel: See practical applications of CTI in enhancing Microsoft Sentinel's threat detection capabilities.
Case Study IV: Building a CTI Program: Learn from a comprehensive blueprint on setting up a successful CTI program within an organization.
Who this course is for:
- SOC Analyst
- Security Engineer
- Security Consultant
- Security Architect
- Security Manager
- CISO
- Red Team
- Blue Team
- Cybersecurity Professional
- Ethical Hacker
- Penetration Tester
- Incident Handler
User Reviews
Rating
Christopher Nett
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 130
- duration 7:22:21
- Release Date 2024/06/24