Cyber Threat Intelligence - Basics & Fundamentals
Adrien Le Sech
2:37:16
Description
Cyber Threat Intelligence / CTI specific models / Tactical, Operational and Strategic Intelligence / Quizzes / Use Cases
What You'll Learn?
- Understand Cyber Threat Intelligence (definition, objectives and specific vocabulary)
- Understand and use CTI specific models (Cyber Kill Chain, Diamond Model, Mitre ATT&CK, Pyramid of Pain)
- Know how to do a threat actor primo-analysis (define intelligence requirements, collect information, analyze information and write a report)
- Know how to do asset monitoring in the Darkweb (set up a virtual environment & VPN connection, monitor forums & marketplaces, monitor ransomware groups)
- Know how to do C2 infrastructure hunting (pivot on SSL certificates and JARM fingerprints)
Who is this for?
More details
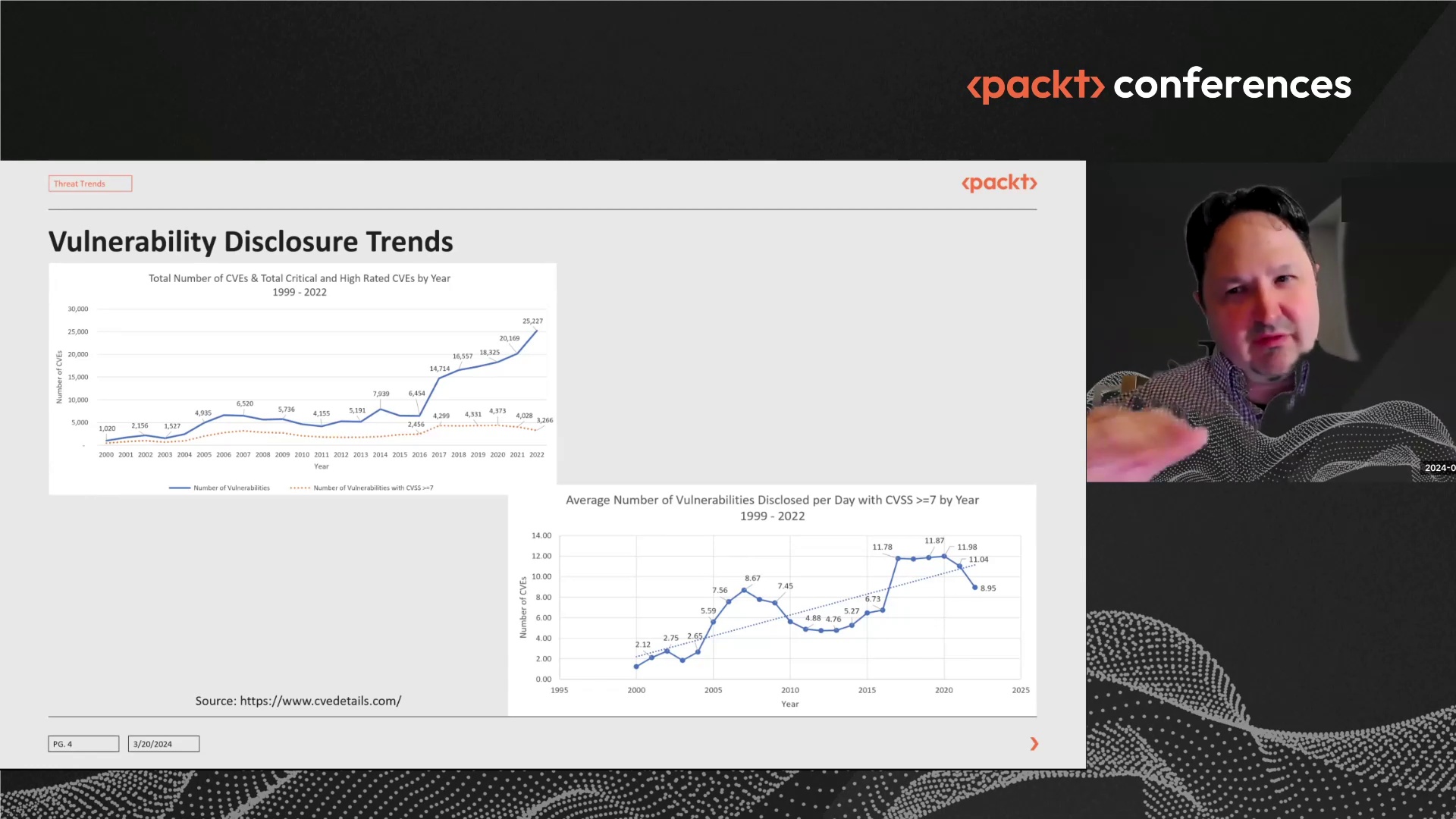
DescriptionCyber Threat Intelligence is a relatively new field within cyber security. As cyber attacks increase both in terms of volume and sophistication, organizations felt the need to anticipate future cyber attacks by analyzing threat actors, malwares, used modus operandi, motivations and possible affiliations.
Are you a young graduate in the field of cyber security, computer science, international relations & geopolitics?
Are you a junior cyber security professionals (SOC analysts, CERT analysts)?
Are you interested in cyber security and would like to know more about Cyber Threat Intelligence?
If yes, this class will provide you:
The theoretical foundations of Cyber Threat Intelligence with:
Definitions of the fundamentals (cyberspace, threat, intelligence, Indicators of Compromise,etc.)
Definition and explanation of CTI specific models (Cyber Kill Chain, Diamond Model, Pyramid of Pain, MITREÂ ATT&CK)
Explanation of CTI objectives (Tactical level, Operational level, Strategic Level Intelligence)
Concrete examples of reports published nowadays
Quizzes to test your knowledge
The practical experience to complete CTIÂ related tasks:
Primo-analysis of a threat actor (context, modus operandi analysis, assessment and recommendations)
Asset monitoring in the Darkweb (setup a virtual environment, VPN connection, identify Darkweb forums and ransomware group activities)
Adversary controlled infrastructure hunting (SSLÂ certificate pivoting and JARM fingerprint pivoting)
Resources for your future tasks as a CTI analyst:
OSINTÂ report integration framework
Intelligence Workbook
Analysis and reports examples
This class is synthetic, straight to the point and well resourced. Enjoy the class and welcome to the CTI community!
Who this course is for:
- Young graduates in the following field: cyber security, computer science, international relations & geopolitics
- Junior cyber security professionals (SOC analysts, CERT analysts)
Cyber Threat Intelligence is a relatively new field within cyber security. As cyber attacks increase both in terms of volume and sophistication, organizations felt the need to anticipate future cyber attacks by analyzing threat actors, malwares, used modus operandi, motivations and possible affiliations.
Are you a young graduate in the field of cyber security, computer science, international relations & geopolitics?
Are you a junior cyber security professionals (SOC analysts, CERT analysts)?
Are you interested in cyber security and would like to know more about Cyber Threat Intelligence?
If yes, this class will provide you:
The theoretical foundations of Cyber Threat Intelligence with:
Definitions of the fundamentals (cyberspace, threat, intelligence, Indicators of Compromise,etc.)
Definition and explanation of CTI specific models (Cyber Kill Chain, Diamond Model, Pyramid of Pain, MITREÂ ATT&CK)
Explanation of CTI objectives (Tactical level, Operational level, Strategic Level Intelligence)
Concrete examples of reports published nowadays
Quizzes to test your knowledge
The practical experience to complete CTIÂ related tasks:
Primo-analysis of a threat actor (context, modus operandi analysis, assessment and recommendations)
Asset monitoring in the Darkweb (setup a virtual environment, VPN connection, identify Darkweb forums and ransomware group activities)
Adversary controlled infrastructure hunting (SSLÂ certificate pivoting and JARM fingerprint pivoting)
Resources for your future tasks as a CTI analyst:
OSINTÂ report integration framework
Intelligence Workbook
Analysis and reports examples
This class is synthetic, straight to the point and well resourced. Enjoy the class and welcome to the CTI community!
Who this course is for:
- Young graduates in the following field: cyber security, computer science, international relations & geopolitics
- Junior cyber security professionals (SOC analysts, CERT analysts)
User Reviews
Rating
Adrien Le Sech
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 62
- duration 2:37:16
- Release Date 2023/06/08