Cryptography
2:29:48
Description
Cipher Modes, PKI, Tunnel, Transport
What You'll Learn?
- Understand Cryptography principles
- PKI knowledge
- Understanding Tunnel vs Transport
- Understanding Cipher modes
Who is this for?
What You Need to Know?
More details
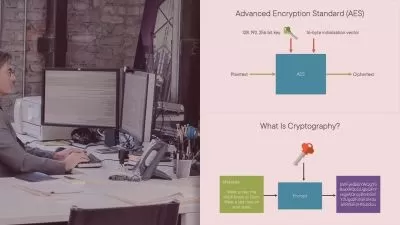
DescriptionThis course on cryptography delves into the fundamental concepts of IT security, emphasizing the historical evolution of ciphers and modern cryptographic practices. It explores the origins and mechanics of classical encryption methods, such as the Caesar cipher, BIFID cipher, Playfair cipher, and Vigenère cipher, providing learners with foundational knowledge of symmetric encryption techniques. Understanding the importance of the CIA triad—Confidentiality, Integrity, and Availability—will be a core theme, underscoring security goals in cryptographic practices.
Learners will study Public Key Infrastructure (PKI) and digital certificates, essential components of modern security, enabling secure communication and authentication. The course also covers tunneling and encapsulation protocols like Transport, Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE), each providing critical insights into secure data transmission over networks.
Moreover, the course introduces the concepts of cryptanalysis and crypto-cracking, giving students a glimpse into methods for decrypting information and examining the robustness of encryption. These practical insights allow learners to critically evaluate and understand encryption’s role in digital security, preparing them for advanced cryptographic concepts and applications in cybersecurity.
The course equips students with practical skills in securing data and understanding vulnerabilities, laying a strong foundation for further exploration in cybersecurity fields, including encryption standards and advanced cryptographic applications.
Who this course is for:
- Technology Learners
This course on cryptography delves into the fundamental concepts of IT security, emphasizing the historical evolution of ciphers and modern cryptographic practices. It explores the origins and mechanics of classical encryption methods, such as the Caesar cipher, BIFID cipher, Playfair cipher, and Vigenère cipher, providing learners with foundational knowledge of symmetric encryption techniques. Understanding the importance of the CIA triad—Confidentiality, Integrity, and Availability—will be a core theme, underscoring security goals in cryptographic practices.
Learners will study Public Key Infrastructure (PKI) and digital certificates, essential components of modern security, enabling secure communication and authentication. The course also covers tunneling and encapsulation protocols like Transport, Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE), each providing critical insights into secure data transmission over networks.
Moreover, the course introduces the concepts of cryptanalysis and crypto-cracking, giving students a glimpse into methods for decrypting information and examining the robustness of encryption. These practical insights allow learners to critically evaluate and understand encryption’s role in digital security, preparing them for advanced cryptographic concepts and applications in cybersecurity.
The course equips students with practical skills in securing data and understanding vulnerabilities, laying a strong foundation for further exploration in cybersecurity fields, including encryption standards and advanced cryptographic applications.
Who this course is for:
- Technology Learners
User Reviews
Rating

Udemy
View courses Udemy- language english
- Training sessions 52
- duration 2:29:48
- Release Date 2025/02/24