CompTIA Security+ (SY0-701) Online Training
Erik Choron
28:04:10
More details
This entry-level Security+ training prepares cybersecurity specialists to secure networks, implement cryptographic techniques, detect and respond to threats, manage risks effectively, and ensure compliance with industry standards.
Security+ is a vendor-neutral certification, which means that earning it proves that you're capable of managing a network's cybersecurity no matter who the vendor or manufacturer is. That's a powerful thing to be able to put on a resume or say in a job interview – it proves you're capable, flexible and knowledgeable.
This training is vendor-agnostic too: you'll practice deploying, managing and configuring security devices and protocols in different hardware and software combinations. The broad cybersecurity familiarity and flexibility you get from this course are very attractive to companies hiring cybersecurity professionals at many different points in their career.
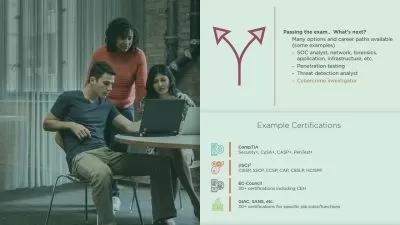
For anyone who manages IT training, this CompTIA training can be used to onboard new cybersecurity specialists, curated into individual or team training plans, or as a CompTIA reference resource.
Security+ (SY0-701): What You Need to Know
This Security+ training has videos that cover topics such as:
- Performing core security functions
- Managing security related to automation, zero trust, risk analysis, and operational technology
- Assessing security posture of enterprise environments and recommend solutions
- Securing hybrid, cloud and on-prem environments
- Proving familiarity with applicable regulations and governance policies
Who Should Take SY0-701 Training?
This Security+ training is considered foundational-level training, which means it was designed for cybersecurity specialists. This security best practices skills course is valuable for new IT professionals with at least a year of experience with security tools and experienced cybersecurity specialists looking to validate their CompTIA skills.
New or aspiring cybersecurity specialists. If you're just getting started in cybersecurity, the Security+ is an excellent credential for proving your competence in key areas of network security, cryptography and risk management. And since this training and the cert are vendor-agnostic, you're not tying yourself down to one system or piece of technology early in your career.
Experienced cybersecurity specialists. This course is perfect for evaluating your knowledge and experience of cybersecurity and shoring up any areas you've overlooked in the last few years of work. It's easy to never stumble across certain jobs, tasks or even hardware/software vendors over the years. But after taking this course, you'll have proof of your well-rounded competence in all aspects of cybersecurity.
User Reviews
Rating
Erik Choron
Instructor's CoursesOnline training allows for the flexibility to learn or better a skill within a timeline and remote environment — that doesn't take away from work or family.
Erik brings over 20 years of IT experience to his training. He holds nearly 20 IT certifications, the majority of which focus on cybersecurity. Prior to joining CBT Nuggets, he served as a First Sergeant in the U.S. Army. His interest in tech and eventually IT was spurred after receiving a 486 computer from his grandfather and learning Basic and Pascal. When Erik isn't creating training videos, he enjoys spending time with his family, going to professional wrestling events, and doing mechanical work.
Certifications: Certifications: Certified Ethical Hacker, GIAC Continuous Monitoring Certification (GMON), GIAC Systems and Network Auditor (GSNA), GIAC Critical Controls Certification (GCCC),GIAC Certified Intrusion Analyst (GCIA) - Gold, GIAC Certified Incident Handler (GCIH), GIAC Certified Enterprise Defender (GCED), GIAC Security Essentials (GSEC), Microsoft MCSA: Server 2012, CompTIA Security+, CompTIA Cloud+, CompTIA A+, PMI® Project Management Professional (PMP)
Areas of expertise: Digital forensics and cyber defense

CBT Nuggets
View courses CBT Nuggets- language english
- Training sessions 277
- duration 28:04:10
- English subtitles has
- Release Date 2024/11/03