CompTIA Security+ SY0-601 Lab Course with Simulations/PBQ
TIA Education, Andrew Ramdayal
24:22:20
Description
Pass your Security+ SY0-601 exam on the first try with a lab base approach to learning. Tons of labs.
What You'll Learn?
- CompTIA Security+ exam objectives
- Attacks against networks
- Methods to protect a network
- Full length Mock Exam
- Introduction to ethical hacking
Who is this for?
More details
DescriptionThis course will prepare you to pass the CompTIA Security+ SY0-601 exam on the first try. In this course I will be using my 20+ years of experience teaching IT courses to give you a practical hands-on approach to all of the CompTIA Security+ Certification exam. I will cover all of the exam objectives in details.
I am a best-selling author that have sold over 150,000 books in project management and IT service management. I have helped thousands of students to pass their certification exam over the last 20 years. My method of teaching is engaging and fun.
I will review how to build your own lab to follow along with me in this journey so you can gain the practical knowledge needed not only to pass your Security+ exam but also how to apply it in the real world of being an IT technician.
This course will cover the following domains:
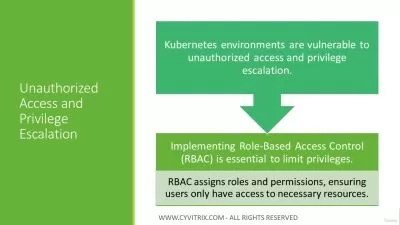
Attacks, Threats, and Vulnerabilities
Architecture and Design
Implementation
Operations and Incident Response
Governance, Risk, and Compliance
This course will include:
Over 200 lectures.
Over 24 Hours of training.
We will only be covering the topics on your exam, no nonsense and personal stories.
PDF of the exam objectives from CompTIA for the Security+ exam.
Certificate of completion.
Lifetime access.
30-day money-back guarantee.
Who this course is for:
- Anyone looking to get CompTIA Security+ Certified
This course will prepare you to pass the CompTIA Security+ SY0-601 exam on the first try. In this course I will be using my 20+ years of experience teaching IT courses to give you a practical hands-on approach to all of the CompTIA Security+ Certification exam. I will cover all of the exam objectives in details.
I am a best-selling author that have sold over 150,000 books in project management and IT service management. I have helped thousands of students to pass their certification exam over the last 20 years. My method of teaching is engaging and fun.
I will review how to build your own lab to follow along with me in this journey so you can gain the practical knowledge needed not only to pass your Security+ exam but also how to apply it in the real world of being an IT technician.
This course will cover the following domains:
Attacks, Threats, and Vulnerabilities
Architecture and Design
Implementation
Operations and Incident Response
Governance, Risk, and Compliance
This course will include:
Over 200 lectures.
Over 24 Hours of training.
We will only be covering the topics on your exam, no nonsense and personal stories.
PDF of the exam objectives from CompTIA for the Security+ exam.
Certificate of completion.
Lifetime access.
30-day money-back guarantee.
Who this course is for:
- Anyone looking to get CompTIA Security+ Certified
User Reviews
Rating
TIA Education, Andrew Ramdayal
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 207
- duration 24:22:20
- English subtitles has
- Release Date 2023/06/08