CompTIA Security+ (SY0-601) Course with Practice Exam
Cybr Training,Christophe Limpalair
23:42:14
Description
Full Practice Exam | Simulated PBQs | Video Lessons | Everything you need to pass the CompTIA Security+ SY0-601 exam
What You'll Learn?
- Get access to this complete and high-quality course for the CompTIA Security+ SY0-601 certification exam
- Pass the CompTIA Security+ with confidence and learn practical skills you can directly apply on-the-job
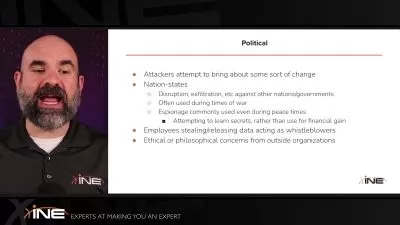
- Common threats, attacks, and vulnerabilities (social engineering, malware, network-based, cloud-based, supply-chain, etc...) and how to defend against them
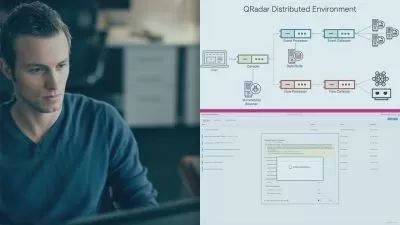
- Proper security architecture and design for: enterprise environments, cloud computing, app development, authentication & authorization, and more
- How to properly implement secure protocols, host & app security solutions, secure network designs, mobile solutions, cloud solutions, PKI, and more
- Incident response approaches: selecting the right tools, policies, processes, and procedures, key aspects of digital forensics, and mitigation techniques
- Governance, Risk, and Compliance concepts: controls, frameworks, regulations & standards, policies, risk management, and privacy for the enterprise
- Full practice exam (multiple choice Q&A) and Performance-Based Questions (PBQs) with explanations included!
Who is this for?
More details
DescriptionWelcome! I'm here to help you prepare for and PASS the CompTIA Security+ SY0-601 exam!
Whether you are new to IT or you already have experience, my course is designed to help you learn all of the topics you need.
-----------------------
Are you trying to get started in cybersecurity? Or are you looking to get a higher-paying job?
The CompTIA Security+ certification is one of the most well-known cybersecurity certifications. It can not only provide you with more job opportunities, but it also provides you with a learning path of important cybersecurity topics you need to understand in order to have a successful career in this space. In fact, certain jobs require that you have at least one IT certification, and the Security+ can often qualify as one of those certifications.
By the way, my name is Christophe Limpalair and I’m the founder of Cybr, a cybersecurity training platform, and the author of this all-in-one Security+ course. I have over 7 years of training experience, and I’ve been in IT for about 20 years. I’ve taught tens of thousands of students in cybersecurity, cloud computing, and web development, and I look forward to helping you get certified.
I've personally taken and passed this exam, so I know exactly what you need to learn and how, and I've sprinkled in tips and tricks throughout the course that will help you get ready for the real exam.
I specifically designed this course syllabus to match the official CompTIA Exam Objectives so that you can keep track of what you’ve learned and what you still need to learn.
This exam has 5 different domains:
Domain 1 is about Attacks, Threats, and Vulnerabilities – which is 24% of the exam
Domain 2 is about Architecture and Design – which is 21% of the exam
Domain 3 is about Implementation – which is 25% of the exam
Domain 4 is about Operations and Incident Response – which is 16% of the exam
Domain 5 is about Governance, Risk, and Compliance – which is 14% of the exam
Within these domains, you will learn about malware, web/cloud/network attacks, cryptography, network configurations, authentication, and much, much more.
If any of those topics sound overwhelming to you — don’t worry! I walk you through it all lesson by lesson.
In fact, this course has over 300 video lessons which is over 23 hours of high-quality video content as well as additional learning materials including a study template you can customize, a full list of Security+ acronyms and their definitions, and knowledge check quizzes.
I’ve even included a multiple-choice practice exam at the end of the course to validate your knowledge and understanding, and I provide free access to multiple Performance-Based Questions (PBQs) that you can take and that mimic PBQs you can expect to see on the exam.
On top of the training you receive, you get access to Cybr’s free Discord community where you can meet others who are actively studying for the Security+ or who have passed it and can provide you with tips and tricks.
If you still have doubts, by the way, I provide a 30-day money-back policy pursuant to Udemy's refund policies.
With an increasing demand for cybersecurity jobs, getting started with this course is a no-brainer. Let’s get started, and let’s take your career to the next level!
I’ll see you in the course!
-----------------------
About the Instructor
Hi, my name is Christophe Limpalair, and I will be your instructor for this course. IÂ got my start in IT at the age of 11 building websites for organizations. This is where IÂ first learned the importance of writing secure code because some of my websites got hacked and I had to figure out how. Back then, there weren't very many affordable learning resources for this topic, so figuring this out was very painful at times. That's when I first started to realize that more training was needed in IT.
Fast-forward a few years, and this thing called "AWS"Â was becoming more and more popular. IÂ started learning how it worked by migrating a few of my projects to it, and IÂ fell in love. Cloud computing was the real deal and IÂ knew it was going to become more and more important over time, so I learned as much of it as IÂ could. Around the same time, IÂ founded a training platform for developers which got acquired by Linux Academy in 2016. There, IÂ authored multiple AWSÂ courses including:Â AWSÂ Lambda Deep Dive, AWSÂ Certified Developer Associate (certification course), AWSÂ Certified DevOps Engineer Professional (certification course), AWSÂ Backup Strategies, and more. IÂ also helped build and secure our Hands-On Labs platform which was constantly under attack because malicious actors wanted to abuse our lab platform to mine cryptocurrency or to launch external attacks from our infrastructure. At the same time, many of our business customers were also sharing that they had issues and concerns with making sure their cloud environments and resources were secure, especially as they were migrating from on-prem.
Once Linux Academy was acquired and merged with ACloudGuru in 2019, IÂ decided to launch my own training platform called Cybr to provide affordable cybersecurity training, including this course and AWSÂ cloud security courses, as well as ethical hacking courses.
Long story short, I've been in ITÂ for about 20 years and I've gotten exposure to web development, cloud computing, and cybersecurity. These are all topics I'm passionate about and that are needed to understand for the Security+Â exam, and IÂ love giving back because so many people have helped me along my journey. That's why I've been creating both free and affordable training material for over 7 years, and that's why IÂ created a free community that all are welcome to join. IÂ hope to see you in my community and in my course!
-----------------------
This course also comes with:
Lifetime access to the content
Udemy Certificate of Completion
Free access to a cybersecurity community
Notion study template you can fully customize
Full list of Security+Â acronyms and their definitions
Full practice exam (multiple choice Q&A) with explanations
Performance-Based Questions (PBQs) with explanations
Let's get you CompTIAÂ Security+Â certified!
Who this course is for:
- Learners who want to pass the CompTIA Security+ certification
- Learners who want to build a solid foundation for cybersecurity by learning best practices
- Learners who are seeking a career in cybersecurity
- Learners who wish to learn more about common threats facing IT systems, networks, applications, and the cloud
Welcome! I'm here to help you prepare for and PASS the CompTIA Security+ SY0-601 exam!
Whether you are new to IT or you already have experience, my course is designed to help you learn all of the topics you need.
-----------------------
Are you trying to get started in cybersecurity? Or are you looking to get a higher-paying job?
The CompTIA Security+ certification is one of the most well-known cybersecurity certifications. It can not only provide you with more job opportunities, but it also provides you with a learning path of important cybersecurity topics you need to understand in order to have a successful career in this space. In fact, certain jobs require that you have at least one IT certification, and the Security+ can often qualify as one of those certifications.
By the way, my name is Christophe Limpalair and I’m the founder of Cybr, a cybersecurity training platform, and the author of this all-in-one Security+ course. I have over 7 years of training experience, and I’ve been in IT for about 20 years. I’ve taught tens of thousands of students in cybersecurity, cloud computing, and web development, and I look forward to helping you get certified.
I've personally taken and passed this exam, so I know exactly what you need to learn and how, and I've sprinkled in tips and tricks throughout the course that will help you get ready for the real exam.
I specifically designed this course syllabus to match the official CompTIA Exam Objectives so that you can keep track of what you’ve learned and what you still need to learn.
This exam has 5 different domains:
Domain 1 is about Attacks, Threats, and Vulnerabilities – which is 24% of the exam
Domain 2 is about Architecture and Design – which is 21% of the exam
Domain 3 is about Implementation – which is 25% of the exam
Domain 4 is about Operations and Incident Response – which is 16% of the exam
Domain 5 is about Governance, Risk, and Compliance – which is 14% of the exam
Within these domains, you will learn about malware, web/cloud/network attacks, cryptography, network configurations, authentication, and much, much more.
If any of those topics sound overwhelming to you — don’t worry! I walk you through it all lesson by lesson.
In fact, this course has over 300 video lessons which is over 23 hours of high-quality video content as well as additional learning materials including a study template you can customize, a full list of Security+ acronyms and their definitions, and knowledge check quizzes.
I’ve even included a multiple-choice practice exam at the end of the course to validate your knowledge and understanding, and I provide free access to multiple Performance-Based Questions (PBQs) that you can take and that mimic PBQs you can expect to see on the exam.
On top of the training you receive, you get access to Cybr’s free Discord community where you can meet others who are actively studying for the Security+ or who have passed it and can provide you with tips and tricks.
If you still have doubts, by the way, I provide a 30-day money-back policy pursuant to Udemy's refund policies.
With an increasing demand for cybersecurity jobs, getting started with this course is a no-brainer. Let’s get started, and let’s take your career to the next level!
I’ll see you in the course!
-----------------------
About the Instructor
Hi, my name is Christophe Limpalair, and I will be your instructor for this course. IÂ got my start in IT at the age of 11 building websites for organizations. This is where IÂ first learned the importance of writing secure code because some of my websites got hacked and I had to figure out how. Back then, there weren't very many affordable learning resources for this topic, so figuring this out was very painful at times. That's when I first started to realize that more training was needed in IT.
Fast-forward a few years, and this thing called "AWS"Â was becoming more and more popular. IÂ started learning how it worked by migrating a few of my projects to it, and IÂ fell in love. Cloud computing was the real deal and IÂ knew it was going to become more and more important over time, so I learned as much of it as IÂ could. Around the same time, IÂ founded a training platform for developers which got acquired by Linux Academy in 2016. There, IÂ authored multiple AWSÂ courses including:Â AWSÂ Lambda Deep Dive, AWSÂ Certified Developer Associate (certification course), AWSÂ Certified DevOps Engineer Professional (certification course), AWSÂ Backup Strategies, and more. IÂ also helped build and secure our Hands-On Labs platform which was constantly under attack because malicious actors wanted to abuse our lab platform to mine cryptocurrency or to launch external attacks from our infrastructure. At the same time, many of our business customers were also sharing that they had issues and concerns with making sure their cloud environments and resources were secure, especially as they were migrating from on-prem.
Once Linux Academy was acquired and merged with ACloudGuru in 2019, IÂ decided to launch my own training platform called Cybr to provide affordable cybersecurity training, including this course and AWSÂ cloud security courses, as well as ethical hacking courses.
Long story short, I've been in ITÂ for about 20 years and I've gotten exposure to web development, cloud computing, and cybersecurity. These are all topics I'm passionate about and that are needed to understand for the Security+Â exam, and IÂ love giving back because so many people have helped me along my journey. That's why I've been creating both free and affordable training material for over 7 years, and that's why IÂ created a free community that all are welcome to join. IÂ hope to see you in my community and in my course!
-----------------------
This course also comes with:
Lifetime access to the content
Udemy Certificate of Completion
Free access to a cybersecurity community
Notion study template you can fully customize
Full list of Security+Â acronyms and their definitions
Full practice exam (multiple choice Q&A) with explanations
Performance-Based Questions (PBQs) with explanations
Let's get you CompTIAÂ Security+Â certified!
Who this course is for:
- Learners who want to pass the CompTIA Security+ certification
- Learners who want to build a solid foundation for cybersecurity by learning best practices
- Learners who are seeking a career in cybersecurity
- Learners who wish to learn more about common threats facing IT systems, networks, applications, and the cloud
User Reviews
Rating
Cybr Training
Instructor's CoursesChristophe Limpalair
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 339
- duration 23:42:14
- Release Date 2023/06/08