001 OSI Layers Ports And Protocols A Tale of Two Kings.mp4
05:10
002 OSI Layers Ports And Protocols The 7 Layers of the OSI Model.mp4
05:23
003 OSI Layers Ports And Protocols TCPIP Suite Layers.mp4
05:49
004 OSI Layers Ports And Protocols Core TCPIP Protocols.mp4
05:18
005 OSI Layers Ports And Protocols Wireshark Views of Core TCPIP Protocols.mp4
04:47
006 OSI Layers Ports And Protocols How Ports Are Used in TCPIP.mp4
06:45
007 OSI Layers Ports And Protocols Verifying L4 Ports with Wireshark.mp4
03:23
008 OSI Layers Ports And Protocols Common Protocols and Their Well-known Ports.mp4
05:58
009 OSI Layers Ports And Protocols TCPs Three-way Handshake.mp4
05:42
010 OSI Layers Ports And Protocols Wireshark Verification of a TCP 3-Way Handshake.mp4
05:00
011 Ethernet Switching Properties of Network Traffic.mp4
05:54
012 Ethernet Switching Layer 2 Ethernet Addresses.mp4
04:50
013 Ethernet Switching How a Layer 2 Switch Works.mp4
05:37
014 Ethernet Switching Demonstration Switch Dynamic Learning.mp4
03:14
015 Ethernet Switching Understanding VLANs.mp4
03:23
016 Ethernet Switching Configuring a VLAN.mp4
05:55
017 Ethernet Switching Overview of 802.1Q and Trunks.mp4
05:53
018 Ethernet Switching Configuring an 802.1Q Ethernet Trunk.mp4
05:31
019 Ethernet Switching How Address Resolution Protocol (ARP) Operates.mp4
05:36
020 Ethernet Switching Predicting the MAC Address Table.mp4
05:46
021 Ethernet Switching Validating MAC Address Table Predictions.mp4
03:35
022 Ethernet Switching Game Predict MAC Table After PC1 Pings PC4.mp4
04:24
023 Ethernet Switching Game Predict MAC Table After PC3 Pings PC5.mp4
04:55
024 Ethernet Switching Switching Loops and Spanning Tree Protocol (STP).mp4
04:29
025 Ethernet Switching STP Reacting to a Network Change.mp4
05:27
026 Ethernet Switching Design Considerations and PoE.mp4
04:31
027 Ethernet Switching Switch Port Mirroring.mp4
03:00
028 IP Routing and Forwarding Introduction to IP Routing.mp4
05:56
029 IP Routing and Forwarding How to Train a Router.mp4
04:49
030 IP Routing and Forwarding Options for Static Routes.mp4
05:17
031 IP Routing and Forwarding Configuring Static Routes.mp4
04:52
032 IP Routing and Forwarding Dynamic Routing Protocol Overview.mp4
04:28
033 IP Routing and Forwarding Dynamic Routing Protocol Demonstration.mp4
02:22
034 IP Routing and Forwarding Address Translation with PAT.mp4
04:41
035 IP Routing and Forwarding One-to-one Translations with NAT.mp4
03:59
036 IP Routing and Forwarding Using Wireshark to Verify IP Translations.mp4
04:25
037 IP Routing and Forwarding Access Control Lists.mp4
05:42
038 IP Routing and Forwarding ACL Demonstration.mp4
04:50
039 IP Routing and Forwarding Enterprise Network Forwarding.mp4
05:31
040 IP Addressing and Subnetting IPv4 Overview.mp4
05:46
041 IP Addressing and Subnetting Binary Basics.mp4
05:43
042 IP Addressing and Subnetting Converting Decimal to Binary.mp4
05:28
043 IP Addressing and Subnetting Converting Binary to Decimal.mp4
05:44
044 IP Addressing and Subnetting The IP Mask.mp4
05:32
045 IP Addressing and Subnetting Practice Using a Different IP Mask.mp4
04:23
046 IP Addressing and Subnetting Borrowing Host Bits.mp4
15:29
047 IP Addressing and Subnetting Practicing the Finger Game.mp4
04:33
048 IP Addressing and Subnetting Identifying New Subnets.mp4
05:36
049 IP Addressing and Subnetting Exercise 1 Identify the New Subnets.mp4
05:50
050 IP Addressing and Subnetting Exercise 2 Identify the New Subnets.mp4
02:55
051 IP Addressing and Subnetting ID Valid Host Addresses on a Subnet.mp4
05:36
052 IP Addressing and Subnetting Exercise 1 ID Valid Host Addresses.mp4
05:48
053 IP Addressing and Subnetting Exercise 2 ID Valid Host Addresses.mp4
05:07
054 IP Addressing and Subnetting Calculate the Number of Hosts per Subnet.mp4
05:57
055 IP Addressing and Subnetting Determine the Subnet Based on a Hosts IP Address.mp4
05:51
056 IP Addressing and Subnetting Planning and Assigning IP Addresses.mp4
05:59
057 IP Addressing and Subnetting Test Your IPv4 Knowledge Lab.mp4
10:33
058 IP Addressing and Subnetting IPv6 Concepts.mp4
05:38
059 Network Topologies Wired Topologies.mp4
06:13
060 Network Topologies Wireless Topologies.mp4
04:55
061 Network Topologies Types of Networks.mp4
05:59
062 Network Topologies Introducing the Internet of Things (IoT).mp4
05:48
063 Network Topologies Internet of Things (IoT) Technologies.mp4
04:42
064 Wireless Technologies and Configurations The Purpose of Wireless.mp4
04:23
065 Wireless Technologies and Configurations Understanding Radio Frequency.mp4
06:36
066 Wireless Technologies and Configurations Understanding Radio Channels.mp4
08:01
067 Wireless Technologies and Configurations Wireless Communication Technologies.mp4
06:53
068 Wireless Technologies and Configurations Designing for Wireless Speed and Coverage.mp4
08:13
069 Wireless Technologies and Configurations Understanding Wireless Antennas.mp4
05:24
070 Wireless Technologies and Configurations Wireless Performance Improvements.mp4
07:27
071 Cloud Concepts Types of Services.mp4
05:41
072 Cloud Concepts Cloud Delivery Models.mp4
03:55
073 Cloud Concepts Connectivity Methods.mp4
05:25
074 Cloud Concepts Security Implications Considerations.mp4
05:51
075 Cloud Concepts Local and Cloud Resource Relationships.mp4
04:56
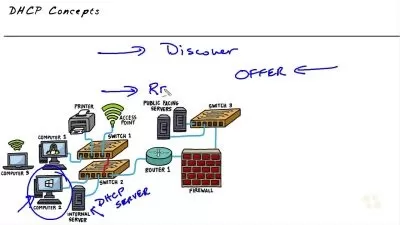
076 Network Services DHCP Overview.mp4
05:55
077 Network Services Verify DHCP with Wireshark.mp4
03:01
078 Network Services DNS Overview.mp4
03:23
079 Network Services DNS Methods Records and Design Options.mp4
05:57
080 Network Services DNS Testing and Validation.mp4
03:42
081 Network Services Network Time Protocol (NTP).mp4
05:15
082 Network Services IP Address Management (IPAM).mp4
03:22
083 Deploying Appropriate Cabling Solutions Copper Network Media Types.mp4
07:59
084 Deploying Appropriate Cabling Solutions Fiber Network Media Types.mp4
06:57
085 Deploying Appropriate Cabling Solutions Network Termination Points.mp4
09:34
086 Deploying Appropriate Cabling Solutions Network Transceivers.mp4
08:14
087 Device Placement and Configuration Network Device Placement.mp4
05:46
088 Device Placement and Configuration Device Configuration Overview.mp4
05:53
089 Device Placement and Configuration Configure Switch Ports Lab.mp4
06:25
090 Device Placement and Configuration Configure IP Addresses Lab.mp4
05:12
091 Device Placement and Configuration Configure IP Routing Lab.mp4
06:15
092 Device Placement and Configuration Configuring DHCP Services Lab.mp4
05:39
093 Device Placement and Configuration Configuring a VLAN Interface Lab.mp4
06:56
094 Device Placement and Configuration Configuring NAT Lab.mp4
06:20
095 Advanced Networking Devices Multi-Layer Switch Overview.mp4
05:58
096 Advanced Networking Devices Configure Multi-Layer Switch Lab.mp4
05:45
097 Advanced Networking Devices Load Balancer Overview.mp4
03:59
098 Advanced Networking Devices IDS and IPS.mp4
05:11
099 Advanced Networking Devices Proxy Servers and Content Filtering.mp4
03:27
100 Advanced Networking Devices Security Network Devices.mp4
04:56
101 Advanced Networking Devices AAARADIUS Server.mp4
03:54
102 Advanced Networking Devices VoIP PBX and Gateway.mp4
03:20
103 Advanced Networking Devices Wireless Controller.mp4
03:02
104 Virtualization And Network Storage Hypervisor Introduction.mp4
05:49
105 Virtualization And Network Storage Virtual Networking Components.mp4
04:05
106 Virtualization And Network Storage Creating a Virtual Switch and VM Lab.mp4
03:25
107 Virtualization And Network Storage Network Storage.mp4
05:10
108 WAN Technologies Understanding the LAN MAN and WAN Difference.mp4
05:17
109 WAN Technologies WAN Transmission over Copper Fiber Wireless and Satellite.mp4
03:55
110 WAN Technologies WAN Types ISDNPRI T1-T3 E1-E3 and OC.mp4
10:05
111 WAN Technologies WAN Types Cable DSL Dial-up.mp4
06:14
112 WAN Technologies WAN Characteristics Frame Relay ATM MPLS and DMVPN.mp4
08:55
113 WAN Technologies What is PPP and PPPoE.mp4
05:20
114 WAN Technologies What is SIP Trunking.mp4
06:50
115 WAN Technologies The Physical Reality of a WAN Connection.mp4
04:56
116 Network Diagram And Documentation Network Documentation is Fun!.mp4
05:55
117 Network Diagram And Documentation Creating Logical Network Diagrams.mp4
05:25
118 Network Diagram And Documentation Creating Physical Diagrams.mp4
05:10
119 Network Diagram And Documentation Naming Conventions and Labeling.mp4
07:11
120 Network Diagram And Documentation Documenting Wiring and Port Locations.mp4
05:46
121 Network Diagram And Documentation SOPs and Work Instructions.mp4
06:53
122 Network Diagram And Documentation Network Change Management.mp4
05:08
123 Network Diagram And Documentation Configuration and Monitoring Baselines.mp4
07:09
124 Network Diagram And Documentation Inventory Management.mp4
04:07
125 Business Continuity Availability Concepts.mp4
05:17
126 Business Continuity Load Sharing and Balancing.mp4
06:00
127 Business Continuity Power Management.mp4
02:51
128 Business Continuity Site Recovery Options.mp4
05:15
129 Business Continuity Backups.mp4
07:43
130 Business Continuity Backup and Restore Hands On Lab.mp4
14:15
131 Business Continuity MTTR and MTBF.mp4
03:58
132 Business Continuity SLA Requirements.mp4
02:49
133 Scanning Monitoring And Patching Scanning Overview.mp4
02:56
134 Scanning Monitoring And Patching Network Scanning Methodology.mp4
03:20
135 Scanning Monitoring And Patching Port Scanning and Discovery.mp4
04:31
136 Scanning Monitoring And Patching OS Discovery and Fingerprinting.mp4
05:50
137 Scanning Monitoring And Patching Motivators for Vulnerability Management.mp4
04:35
138 Scanning Monitoring And Patching Vulnerability Scanning.mp4
05:00
139 Scanning Monitoring And Patching Logging and Review.mp4
05:52
140 Scanning Monitoring And Patching Packet and Traffic Analysis.mp4
04:43
141 Scanning Monitoring And Patching Packet Capture and Analysis Lab.mp4
10:34
142 Scanning Monitoring And Patching Remediation and Patch Management.mp4
05:55
143 Scanning Monitoring And Patching Network Scanning with NMAP and Zenmap Lab.mp4
17:36
144 Scanning Monitoring And Patching Baselines.mp4
04:04
145 Remote Access Methods Telnet and SSH for CLI Remote Access.mp4
04:29
146 Remote Access Methods HTTPS Management URLs.mp4
03:03
147 Remote Access Methods VPNs.mp4
05:28
148 Remote Access Methods Remote Desktop Access.mp4
04:06
149 Remote Access Methods Out-of-Band Management.mp4
05:06
150 Identify Policies And Best Practices Privileged User Agreement.mp4
04:00
151 Identify Policies And Best Practices Password Policy.mp4
03:44
152 Identify Policies And Best Practices On-boarding and Off-boarding.mp4
06:41
153 Identify Policies And Best Practices Licensing Restrictions.mp4
04:35
154 Identify Policies And Best Practices International Export Controls.mp4
03:25
155 Identify Policies And Best Practices Data Loss Prevention.mp4
04:07
156 Identify Policies And Best Practices Remote Access Policies.mp4
03:52
157 Identify Policies And Best Practices Incident Response Policies.mp4
05:03
158 Identify Policies And Best Practices Bring Your Own Device (BYOD).mp4
05:12
159 Identify Policies And Best Practices Acceptable Use Policy (AUP).mp4
03:34
160 Identify Policies And Best Practices Non-disclosure Agreements (NDA).mp4
04:02
161 Identify Policies And Best Practices System Life Cycle.mp4
04:24
162 Identify Policies And Best Practices Safety Procedures and Policies.mp4
02:32
163 Physical Security And Network Attacks Lets Break into a Data Center.mp4
02:22
164 Physical Security And Network Attacks Video Surveillance and Motion Detection.mp4
05:28
165 Physical Security And Network Attacks Badges and Smart Cards.mp4
05:12
166 Physical Security And Network Attacks Biometrics.mp4
05:09
167 Physical Security And Network Attacks Locks Asset Tags and Tamper Detection.mp4
05:28
168 Physical Security And Network Attacks DoS and PDoS (Permanent Denial of Service).mp4
04:18
169 Physical Security And Network Attacks DDoS (Distributed Denial of Service).mp4
04:33
170 Physical Security And Network Attacks DDoS with ICMP and Smurfing.mp4
03:19
171 Physical Security And Network Attacks DDoS with DNS and NTP.mp4
03:59
172 Physical Security And Network Attacks Lets Go Phishing.mp4
04:01
173 Physical Security And Network Attacks Social Engineering and Insider Threats.mp4
04:35
174 Physical Security And Network Attacks Ransomware and Scareware.mp4
04:07
175 Physical Security And Network Attacks Cryptolocker and Logic Bombs.mp4
05:43
176 Physical Security And Network Attacks DNS Spoofing (Poisoning).mp4
05:55
177 Physical Security And Network Attacks Man-In-The-Middle with ARP Spoofing.mp4
05:51
178 Physical Security And Network Attacks Wardriving and Deauthentication.mp4
05:32
179 Physical Security And Network Attacks Evil Twins and Rogue Access Points.mp4
04:59
180 Authentication And Access Control AAA.mp4
05:43
181 Authentication And Access Control Multi-factor Authentication Overview.mp4
04:44
182 Authentication And Access Control Using Two-Factor Authentication (2FA).mp4
04:46
183 Authentication And Access Control Demo Implementing 2FA.mp4
05:48
184 Authentication And Access Control Switch Port Security.mp4
02:52
185 Authentication And Access Control Access Control Methods.mp4
03:37
186 Basic Wireless Network Security The Wireless Security Evolution.mp4
06:51
187 Basic Wireless Network Security Wireless Authentication and Authorization Types.mp4
06:56
188 Mitigation Techniques Network Device Hardening.mp4
05:55
189 Mitigation Techniques Hardening a Windows Server System.mp4
04:12
190 Mitigation Techniques Signature Management.mp4
03:11
191 Mitigation Techniques File Integrity Monitoring.mp4
04:31
192 Mitigation Techniques Privileged User Accounts and Role Separation.mp4
05:14
193 Mitigation Techniques Network Segmentation.mp4
04:08
194 Mitigation Techniques Switch Port Protections.mp4
06:46
195 Mitigation Techniques The Native VLAN.mp4
04:58
196 Mitigation Techniques Filtering with Access Control Lists (ACLs).mp4
06:21
197 Mitigation Techniques Honeypots and Honeynets.mp4
03:23
198 Mitigation Techniques Penetration Testing.mp4
05:01
199 Troubleshooting Methodology A Network Troubleshooting Methodology.mp4
04:12
200 Troubleshooting Methodology Identify the Problem.mp4
04:04
201 Troubleshooting Methodology Establish a Theory of Probable Cause.mp4
05:29
202 Troubleshooting Methodology Test the Theory to Determine the Root Cause.mp4
03:37
203 Troubleshooting Methodology Establish a Plan of Action to Solve the Problem.mp4
04:09
204 Troubleshooting Methodology Problem Solving Verification and Documentation.mp4
04:42
205 Network Troubleshooting Hardware Tools.mp4
08:33
206 Network Troubleshooting Software Tools.mp4
08:38
207 Network Troubleshooting Using CLI Network Tools ipconfig ping arp.mp4
08:34
208 Network Troubleshooting Using CLI Network Tools nslookup dig.mp4
07:30
209 Network Troubleshooting Using CLI Network Tools tracert pathping nmap route.mp4
09:07
210 Network Troubleshooting Using CLI Network Tools ifconfig iptables tcpdump and netstat.mp4
06:58
211 Wired Connectivity And Performance Issues Attenuation Latency and Jitter.mp4
05:49
212 Wired Connectivity And Performance Issues Crosstalk EMI OpenShort.mp4
05:32
213 Wired Connectivity And Performance Issues Incorrect Pin-Outs or Cable Types.mp4
04:27
214 Wired Connectivity And Performance Issues Mismatched and Damaged Cables.mp4
03:20
215 Wired Connectivity And Performance Issues Bad Ports and LED Status Indicators.mp4
04:59
216 Wired Connectivity And Performance Issues Duplex and Speed Mismatches.mp4
04:41
217 Wired Connectivity And Performance Issues VLAN Mismatches.mp4
07:28
218 Wired Connectivity And Performance Issues Native VLAN Mismatches.mp4
05:49
219 Wired Connectivity And Performance Issues Bottlenecks.mp4
05:13
220 Troubleshooting Wireless The Nature of Airwaves.mp4
06:55
221 Troubleshooting Wireless Fighting Frequencies.mp4
08:50
222 Troubleshooting Wireless Understanding Antenna Types.mp4
05:31
223 Troubleshooting Wireless Misconfigurations.mp4
07:19
224 Common Network Service Issues Troubleshooting Name Resolution.mp4
06:35
225 Common Network Service Issues Troubleshooting MAC Addressing.mp4
05:28
226 Common Network Service Issues Troubleshooting IP Addressing.mp4
05:42
227 Common Network Service Issues Troubleshooting Security Settings.mp4
05:21
228 Common Network Service Issues Troubleshooting Miscellaneous Service Issues.mp4
05:27