CompTIA CySA+ (CS0-002)
Stone River eLearning
11:30:04
Description
CompTIA Cyber Security Analyst
What You'll Learn?
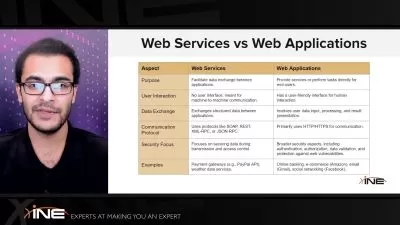
- Learn to manage threats and vulnerabilities by understanding attack frameworks like MITRE ATT&CK
- Learn about attack kill chain and identify vulnerabilities using assessment tools
- Perform remediation and mitigation of threats and vulnerabilities
- Learn about threats and vulnerabilities for cloud environments and software
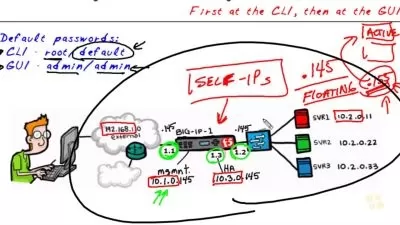
- Manage security infrastructure and learn about network security solutions
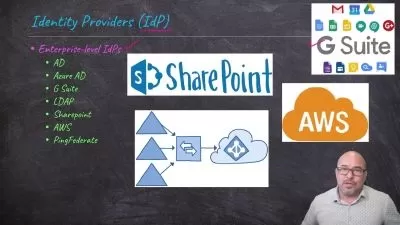
- Implement identity and access management
- Get to know advanced techniques like cryptography
- Ensure hardware security and learn about software assurance methods and best practices
- Learn the concepts of monitoring, logging, aggregating and analyzing security related data
- Implement security changes and manage security configuration
- Understand the importance of incident response and learn about incident response cycle
- Utilize digital forensic techniques
- Analyze indicators of compromise (IoCs)
- Perform compliance checks and assessments
- Analyze business impact and perform risk assessment
Who is this for?
What You Need to Know?
More details
DescriptionThe CompTIA Cyber Security Analyst course is an intermediate level certification that assesses both practical performance as well as theoretical knowledge of the candidates in the field of cyber security. Due to the increased exposure of data, applications and critical resources of any organization, cyber security is rapidly taking the center stage in every organization’s vision, mission and roadmap. The CompTIA CySA+ certification prepares the candidates to use artificial intelligence and threat detection techniques, analyze and interpret sensitive and critical data, pinpoint and fix vulnerabilities, suggest preventative measures to effectively respond to and recover from data breach and intrusion incidents. This set of skills helps the candidates to stand out and enhance job prospects in the competitive field of cyber security as well as related fields like information security, network security and systems security.
The CompTIA CySA+ (Cyber Security Analyst) course is an ideal course for information security professionals who are looking for career progression in this ever growing and always changing field. During the last decade, cyber security’s importance has increased exponentially and with this, the job openings have also multiplied several folds. On the other hand, the inflow of trained and certified cyber security professionals has not been able to match the demand, hence resulting in higher salaries for the trained professionals. The CompTIA CySA+ certification, being an intermediate level certification, provides an excellent opportunity to candidates to step foot in the cyber security and information security job market and excel from there. As a starting point for cyber security related certification, the training you will receive in this course, will help you to be prepared for the exam contents and successfully clear the CompTIA CySA+ exam.
Who this course is for:
- Security analysts working in any organization
- Threat intelligence analysts
- Information security manager
- Security engineer
- Application security analyst
- Incident responder or handler
- Compliance analyst
- Threat hunter
- Information security officer
The CompTIA Cyber Security Analyst course is an intermediate level certification that assesses both practical performance as well as theoretical knowledge of the candidates in the field of cyber security. Due to the increased exposure of data, applications and critical resources of any organization, cyber security is rapidly taking the center stage in every organization’s vision, mission and roadmap. The CompTIA CySA+ certification prepares the candidates to use artificial intelligence and threat detection techniques, analyze and interpret sensitive and critical data, pinpoint and fix vulnerabilities, suggest preventative measures to effectively respond to and recover from data breach and intrusion incidents. This set of skills helps the candidates to stand out and enhance job prospects in the competitive field of cyber security as well as related fields like information security, network security and systems security.
The CompTIA CySA+ (Cyber Security Analyst) course is an ideal course for information security professionals who are looking for career progression in this ever growing and always changing field. During the last decade, cyber security’s importance has increased exponentially and with this, the job openings have also multiplied several folds. On the other hand, the inflow of trained and certified cyber security professionals has not been able to match the demand, hence resulting in higher salaries for the trained professionals. The CompTIA CySA+ certification, being an intermediate level certification, provides an excellent opportunity to candidates to step foot in the cyber security and information security job market and excel from there. As a starting point for cyber security related certification, the training you will receive in this course, will help you to be prepared for the exam contents and successfully clear the CompTIA CySA+ exam.
Who this course is for:
- Security analysts working in any organization
- Threat intelligence analysts
- Information security manager
- Security engineer
- Application security analyst
- Incident responder or handler
- Compliance analyst
- Threat hunter
- Information security officer
User Reviews
Rating
Stone River eLearning
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 218
- duration 11:30:04
- English subtitles has
- Release Date 2024/01/31