Complete Infoblox Tech Training (NIOS/BloxOne) P2/BloxOne
GIANT Labs
5:21:55
Description
A Complete Technical Guide To Most Popular Feature Of Infoblox BloxOne DDI & BloxOne Threat Defense
What You'll Learn?
- Defining the needed concepts of Infoblox BloxOne DDI and BloxOne Threat Defense
- Using BloxOne To Create DNS Objects For On Premises Datacenters Using On Prem Hosts
- Using BloxOne To Create DHCP Objects For In Premises Datacenters Using On Prem Hosts
- Understands All Settings Related To On Prem Host And How To Configure It
- Researching For Threats Using Research Tools Like Dossier
- Using Logging And Reporting Options
Who is this for?
More details
DescriptionDuring This Second Portion Of "Complete Infoblox Technical Training (NIOS/BloxOne)" , we are going to explain and discover the main pillars of infoblox bloxone and how to use it inside our corporate network .
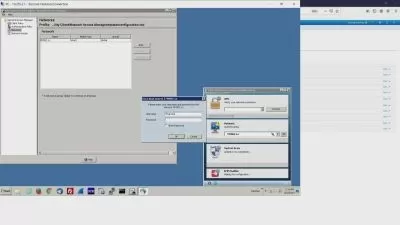
Firstly , we are going to see how to use DDI within BloxOne and how to manage DNSÂ and DHCP using an on prem host in our DCÂ that can contact infoblox bloxone to start taking instruction from it to be executed inside our environment . We are going to review quickly on the theoretical stuff for DNS and DHCP before we get started with our labs and practice . Then there are some labs that we'll do related to DNSÂ and DHCP through bloxone .
Secondly , we are going to start with bloxone threat defense, which is a separate component used to secure the first gate of traffic "Resolving/DNS". We are going to see methods used to connect to your on prem host to start pushing the needed security policies to be used . Also we'll see the types of rules that we can use inside our security policies ( custom lists , app filters , feed and others ) and what are the available actions that we can take according to each rule .
Finally , we are going to learn how to investigate for multiple objects ( passing traffic through DNSÂ , DHCP , DNSÂ activity and security alerts and also how to investigate a specific ip or domain using dossier and researching tools ) .
Who this course is for:
- - Systems Engineers .
- - Networking Engineers .
- - Networks/Systems Security Engineers .
- - IT Professional
During This Second Portion Of "Complete Infoblox Technical Training (NIOS/BloxOne)" , we are going to explain and discover the main pillars of infoblox bloxone and how to use it inside our corporate network .
Firstly , we are going to see how to use DDI within BloxOne and how to manage DNSÂ and DHCP using an on prem host in our DCÂ that can contact infoblox bloxone to start taking instruction from it to be executed inside our environment . We are going to review quickly on the theoretical stuff for DNS and DHCP before we get started with our labs and practice . Then there are some labs that we'll do related to DNSÂ and DHCP through bloxone .
Secondly , we are going to start with bloxone threat defense, which is a separate component used to secure the first gate of traffic "Resolving/DNS". We are going to see methods used to connect to your on prem host to start pushing the needed security policies to be used . Also we'll see the types of rules that we can use inside our security policies ( custom lists , app filters , feed and others ) and what are the available actions that we can take according to each rule .
Finally , we are going to learn how to investigate for multiple objects ( passing traffic through DNSÂ , DHCP , DNSÂ activity and security alerts and also how to investigate a specific ip or domain using dossier and researching tools ) .
Who this course is for:
- - Systems Engineers .
- - Networking Engineers .
- - Networks/Systems Security Engineers .
- - IT Professional
User Reviews
Rating
GIANT Labs
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 34
- duration 5:21:55
- Release Date 2023/04/26