Complete F5 Bootcamp (LTM,ASM,DNS) - P1 (ASM
GIANT Labs
8:29:41
Description
Complete F5 Technical & Practical Training For The Main Three Modules Of F5 ( LTM , ASM & DNS "GTM" ) .
What You'll Learn?
- Take a complete overview of f5 bigip asm module and how it works
- Define the main components of security policy and how to configure it
- Identify the differences between learning and blocking settings
- Take a complete real world project scenario
- Make a real world penetration testing scenarios using kali linux
Who is this for?
What You Need to Know?
More details
DescriptionIn this first portion of this course (Â Complete F5 Technical & Practical Training For The Main Three Modules Of F5 ( LTM , ASM & DNS "GTM" ) we will tackle the main needed topics to secure a web application through ASM "Application Security Manager" of f5 .
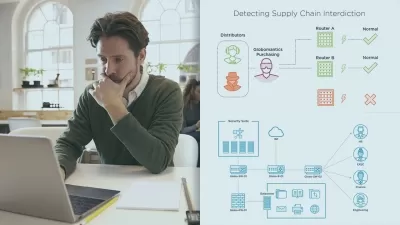
In the first section we will speak about an overview of ASM module and the theory of web application firewall , what are the main attack types that we can secure against and finally we'll tackle the main owasp top 10 vunlerabilities of any web application .
With the section section , we'll be familiar with how ASMÂ learning methodolgy works and how we can tune the policy according to the learning results .
In the third section , we'll understand deeply the concept of automatic learning and how we can create a policy in an automatic mode to automatically enable our asm to accept learning suggestion without any intervention from the administrator .
Then , we'll take a deep look into the main objects to secure related to the web application against some popular attacks like ( brute force attacks , DOS attacks , bot attacks and others ) .
After that , we'll see how to work with parameters with all their types inside the web application (Â static parameters and dynamic parameters )Â .
Finally , we'll configure some features related to the administration of this module "ASM" and how to configure logging and also how to generate reports .
Who this course is for:
- Application Security Engineers
- Penetrations Testers
- Networks Security Engineers
- IT Systems Engineers
In this first portion of this course (Â Complete F5 Technical & Practical Training For The Main Three Modules Of F5 ( LTM , ASM & DNS "GTM" ) we will tackle the main needed topics to secure a web application through ASM "Application Security Manager" of f5 .
In the first section we will speak about an overview of ASM module and the theory of web application firewall , what are the main attack types that we can secure against and finally we'll tackle the main owasp top 10 vunlerabilities of any web application .
With the section section , we'll be familiar with how ASMÂ learning methodolgy works and how we can tune the policy according to the learning results .
In the third section , we'll understand deeply the concept of automatic learning and how we can create a policy in an automatic mode to automatically enable our asm to accept learning suggestion without any intervention from the administrator .
Then , we'll take a deep look into the main objects to secure related to the web application against some popular attacks like ( brute force attacks , DOS attacks , bot attacks and others ) .
After that , we'll see how to work with parameters with all their types inside the web application (Â static parameters and dynamic parameters )Â .
Finally , we'll configure some features related to the administration of this module "ASM" and how to configure logging and also how to generate reports .
Who this course is for:
- Application Security Engineers
- Penetrations Testers
- Networks Security Engineers
- IT Systems Engineers
User Reviews
Rating
GIANT Labs
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 30
- duration 8:29:41
- Release Date 2023/06/24