Complete Cyber Security Course: The Network Security A-Z™
Teach Apex
15:17:22
Description
Cyber Security In-depth - Network Security Fundamentals (Threat, Vulnerabilities), NMAP, Firewalls & Prevent Attacks
What You'll Learn?
- Network Fundamentals
- Network Design Elements and Components
- Network Security Threats, Vulnerabilities, and Attacks
- Network Security Controls, Devices and Protocols
- Introduction to Intrusion Detection System
- Introduction to Firewalls
- Introduction to Wireless Network Security
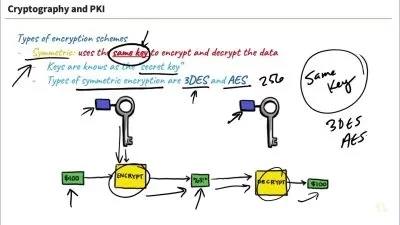
- Sniffing and Spoofing
- Network Traffic Monitoring & Analysis
- Network Scanning
Who is this for?
What You Need to Know?
More details
DescriptionBecome a Network Security Specialist with this exclusive course covering every aspect of Network Security. After this course, you will be able to discover security vulnerabilities across an entire network, by using network hacking techniques and vulnerability scanning.
You will be able to architect your network for maximum security and prevent local and remote attacks. You will understand the various types of firewalls that are available and what threats each helps mitigate.
Explore wireless security, the configurations that are required for maximum security, and why. Learn how Wi-Fi is hacked and how to mitigate those attacks, covering topics from Wireless encryption weaknesses and the latest WPA3 standard.
You will master network monitoring to discover and identify potential hackers, malware, and other adversaries that might be lurking on your network. Using tools like Wireshark and Nmap.
Learn the best ways to reduce the attack surface of your network and harden it for maximum security and privacy. Finally, you will fully understand how to best use IDS and IPS in your network to secure your network.
This Network Security training can be used as a security solution for home-based or any business-sized networks, which makes it an ideal solution for securing networking activities.
After going through this course, you will find yourself at an intermediate level of knowledge regarding network security.
Who this course is for:
- Any internet user who wants to become an expert in security, privacy, and anonymity.
- For all levels of internet users who are interested in security, safety, and privacy.
- This course is for anyone who wants to keep their important files, emails, accounts and personal information out of the hackers.
- This course is for anyone who wants to become an expert in network security, privacy, and anonymity. This course covers network security attacking and defending techniques.
- This course is specially designed for the personnel who would love to gain a practical skillset in mitigating the network security attacks such as - Virus, Trojans, Spywares, Keyloggers, DoS/DDoS, Password based attacks etc. by implementing Firewalls/IDS/IPS solutions and implementing a complete Network Vulnerability Assessment plan.
- This course is ideal for Network Security leaders responsible for applying best practices to secure Network, including those in the following positions: Network Security Administrator, Network Security Auditors, Security Consultant, Security Architect
- For anyone who would love to gain a practical skillset in mitigating the risk from, malware, Trojans, hackers, trackers, cyber criminals and all online threats.
- This course is designed for personal and home Internet security, privacy, and anonymity.
Become a Network Security Specialist with this exclusive course covering every aspect of Network Security. After this course, you will be able to discover security vulnerabilities across an entire network, by using network hacking techniques and vulnerability scanning.
You will be able to architect your network for maximum security and prevent local and remote attacks. You will understand the various types of firewalls that are available and what threats each helps mitigate.
Explore wireless security, the configurations that are required for maximum security, and why. Learn how Wi-Fi is hacked and how to mitigate those attacks, covering topics from Wireless encryption weaknesses and the latest WPA3 standard.
You will master network monitoring to discover and identify potential hackers, malware, and other adversaries that might be lurking on your network. Using tools like Wireshark and Nmap.
Learn the best ways to reduce the attack surface of your network and harden it for maximum security and privacy. Finally, you will fully understand how to best use IDS and IPS in your network to secure your network.
This Network Security training can be used as a security solution for home-based or any business-sized networks, which makes it an ideal solution for securing networking activities.
After going through this course, you will find yourself at an intermediate level of knowledge regarding network security.
Who this course is for:
- Any internet user who wants to become an expert in security, privacy, and anonymity.
- For all levels of internet users who are interested in security, safety, and privacy.
- This course is for anyone who wants to keep their important files, emails, accounts and personal information out of the hackers.
- This course is for anyone who wants to become an expert in network security, privacy, and anonymity. This course covers network security attacking and defending techniques.
- This course is specially designed for the personnel who would love to gain a practical skillset in mitigating the network security attacks such as - Virus, Trojans, Spywares, Keyloggers, DoS/DDoS, Password based attacks etc. by implementing Firewalls/IDS/IPS solutions and implementing a complete Network Vulnerability Assessment plan.
- This course is ideal for Network Security leaders responsible for applying best practices to secure Network, including those in the following positions: Network Security Administrator, Network Security Auditors, Security Consultant, Security Architect
- For anyone who would love to gain a practical skillset in mitigating the risk from, malware, Trojans, hackers, trackers, cyber criminals and all online threats.
- This course is designed for personal and home Internet security, privacy, and anonymity.
User Reviews
Rating
Teach Apex
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 94
- duration 15:17:22
- English subtitles has
- Release Date 2023/09/10