CISSP : Domain 1 : Security and Risk Management - Learn 2024
CloudMatrix Learning
8:37:28
Description
Comprehensive cybersecurity certification covering risk management, access control, cryptography, and incident response.
What You'll Learn?
- Principles of risk management, including risk identification, assessment, and mitigation strategies.
- Security governance frameworks and their implementation.
- Security policies, standards, procedures, and guidelines development and enforcement.
- Asset classification and control, including information classification and handling.
- Compliance with relevant laws, regulations, and business requirements.
- Professional ethics and the importance of security awareness and training.
- Incident response and disaster recovery planning.
- Business continuity management and its integration with security practices.
Who is this for?
What You Need to Know?
More details
DescriptionHere's a detailed course outline for the Certified Information Systems Security Professional (CISSP) certification:
CISSP Course Outline:
Introduction to CISSP
Overview of the CISSP certification
Understanding the CISSP domains and their importance
Exam structure, format, and requirements
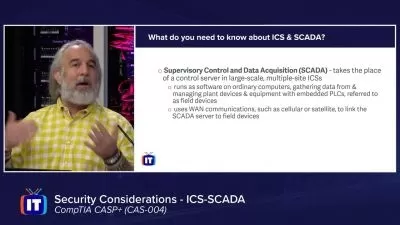
Security and Risk Management
Principles of security and risk management
Risk assessment and management
Security governance and compliance
Business continuity and disaster recovery planning
Asset Security
Identifying and classifying information assets
Protecting data confidentiality, integrity, and availability
Cryptography and its applications
Physical security controls
Security Architecture and Engineering
Secure system design principles
Security models and frameworks
Security control types and their implementation
Security in the Software Development Life Cycle (SDLC)
Communication and Network Security
Network security architecture and components
Secure network design and protocols
Wireless security
Remote access and VPN technologies
Identity and Access Management
Principles of identity and access management
Authentication, authorization, and accounting
Identity federation and single sign-on
Privileged account management
Security Assessment and Testing
Security assessment methodologies
Vulnerability assessment and penetration testing
Security monitoring and auditing
Incident response and forensics
Security Operations
Operational security controls
Patch and vulnerability management
Logging, monitoring, and alerting
Disaster recovery and business continuity
Software Development Security
Secure software design principles
Secure coding techniques and practices
Security testing and validation
Supply chain security
Exam Preparation and Review
Practice questions and mock exams
Time management and exam-taking strategies
Final review and consolidation of key concepts
This comprehensive course outline covers the eight domains of the CISSP exam, providing a detailed understanding of the knowledge and skills required to become a Certified Information Systems Security Professional. The course will equip participants with the necessary expertise to protect organizations from cyber threats, manage security risks, and implement effective security controls.
Who this course is for:
- This CISSP Domain 1: Security and Risk Management course is designed for individuals who are preparing for the CISSP (Certified Information Systems Security Professional) certification exam.
- It covers the first domain of the CISSP exam, which focuses on security and risk management.
- The course is suitable for IT professionals, security analysts, security managers, and anyone interested in enhancing their knowledge and skills in information security and risk management.
- Whether you're new to the field or an experienced security practitioner, this course will provide you with the necessary knowledge and strategies to succeed in the CISSP certification process.
Here's a detailed course outline for the Certified Information Systems Security Professional (CISSP) certification:
CISSP Course Outline:
Introduction to CISSP
Overview of the CISSP certification
Understanding the CISSP domains and their importance
Exam structure, format, and requirements
Security and Risk Management
Principles of security and risk management
Risk assessment and management
Security governance and compliance
Business continuity and disaster recovery planning
Asset Security
Identifying and classifying information assets
Protecting data confidentiality, integrity, and availability
Cryptography and its applications
Physical security controls
Security Architecture and Engineering
Secure system design principles
Security models and frameworks
Security control types and their implementation
Security in the Software Development Life Cycle (SDLC)
Communication and Network Security
Network security architecture and components
Secure network design and protocols
Wireless security
Remote access and VPN technologies
Identity and Access Management
Principles of identity and access management
Authentication, authorization, and accounting
Identity federation and single sign-on
Privileged account management
Security Assessment and Testing
Security assessment methodologies
Vulnerability assessment and penetration testing
Security monitoring and auditing
Incident response and forensics
Security Operations
Operational security controls
Patch and vulnerability management
Logging, monitoring, and alerting
Disaster recovery and business continuity
Software Development Security
Secure software design principles
Secure coding techniques and practices
Security testing and validation
Supply chain security
Exam Preparation and Review
Practice questions and mock exams
Time management and exam-taking strategies
Final review and consolidation of key concepts
This comprehensive course outline covers the eight domains of the CISSP exam, providing a detailed understanding of the knowledge and skills required to become a Certified Information Systems Security Professional. The course will equip participants with the necessary expertise to protect organizations from cyber threats, manage security risks, and implement effective security controls.
Who this course is for:
- This CISSP Domain 1: Security and Risk Management course is designed for individuals who are preparing for the CISSP (Certified Information Systems Security Professional) certification exam.
- It covers the first domain of the CISSP exam, which focuses on security and risk management.
- The course is suitable for IT professionals, security analysts, security managers, and anyone interested in enhancing their knowledge and skills in information security and risk management.
- Whether you're new to the field or an experienced security practitioner, this course will provide you with the necessary knowledge and strategies to succeed in the CISSP certification process.
User Reviews
Rating
CloudMatrix Learning
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 148
- duration 8:37:28
- Release Date 2024/08/11