Cisco ISE - For Wired Networks
Moiz moiz
4:38:04
Description
ISE for wired networks
What You'll Learn?
- Learn to install lab components such as EVE-NG, cisco Catalyst switch and windows 10
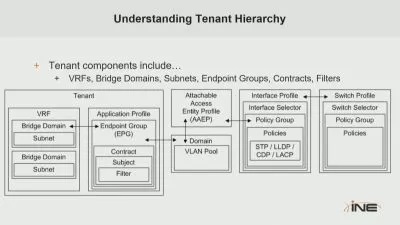
- Implementing cisco ISE Two node distributed deployment
- Implementing different authentications such as MAB & Dot1x
- Profiling machines, Guest Access, and BYOD
Who is this for?
More details
DescriptionCisco Identity Services Engine (ISE)
Know and control devices and users on your network
Leverage intel from across your stack to enforce policy, manage endpoints, and deliver trusted access. Multicloud NAC with zero trust makes it possible.
In zero-trust architecture, ISE is the policy decision point. It gathers intel from the stack to authenticate users and endpoints, automatically containing threats.
​Harness the power of resilience​
​Resilience begins with secure connections. ISE helps ensure that only trusted users and their devices can access resources across your self-managed network.
Visibility better than 20/20
Knowing who's connecting to your network, what devices they're on, and what connection they're using is key. ISE uses key intel to automatically identify, classify, and profile devices.
Think outside the box
​Switching from infrastructure in a box to infrastructure as code (IaC) helps preserve business integrity, while aligning access and policy to your strategy and objectives.
Make a stand
Verify your device posture with ISE 3.x and see how easily it complies with your security policy. ISE works to protect your network, data, and resources from hostile attacks.
Flexibility and choice power security
resilience for zero-trust architectures
What if IT and security operations could respond to change
and reduce risk with seamless access to network resources
from anywhere, to everywhere, and on anything? And, what
if controlling and managing access to the workplace was
radically simplified and modernized to build security
resilience into the network?© 2022 Cisco and/or its affiliates. All rights reserved.
Who this course is for:
- IT admins, Cisco Admins, Cisco ISE admins, Administrators, Cisco ISE supporting officer
Cisco Identity Services Engine (ISE)
Know and control devices and users on your network
Leverage intel from across your stack to enforce policy, manage endpoints, and deliver trusted access. Multicloud NAC with zero trust makes it possible.
In zero-trust architecture, ISE is the policy decision point. It gathers intel from the stack to authenticate users and endpoints, automatically containing threats.
​Harness the power of resilience​
​Resilience begins with secure connections. ISE helps ensure that only trusted users and their devices can access resources across your self-managed network.
Visibility better than 20/20
Knowing who's connecting to your network, what devices they're on, and what connection they're using is key. ISE uses key intel to automatically identify, classify, and profile devices.
Think outside the box
​Switching from infrastructure in a box to infrastructure as code (IaC) helps preserve business integrity, while aligning access and policy to your strategy and objectives.
Make a stand
Verify your device posture with ISE 3.x and see how easily it complies with your security policy. ISE works to protect your network, data, and resources from hostile attacks.
Flexibility and choice power security
resilience for zero-trust architectures
What if IT and security operations could respond to change
and reduce risk with seamless access to network resources
from anywhere, to everywhere, and on anything? And, what
if controlling and managing access to the workplace was
radically simplified and modernized to build security
resilience into the network?© 2022 Cisco and/or its affiliates. All rights reserved.
Who this course is for:
- IT admins, Cisco Admins, Cisco ISE admins, Administrators, Cisco ISE supporting officer
User Reviews
Rating
Moiz moiz
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 11
- duration 4:38:04
- Release Date 2023/03/29