Cisco Certified Support Technician (CCST) Cybersecurity Online Training
James Conrad
20:49:47
More details
This entry-level Cisco Certified Support Technician (CCST) Cybersecurity training prepares entry-level cybersecurity professionals to operate, maintain, troubleshoot, and configure the Cisco devices and software that keep devices and networks secure.
The CCST series of certifications from Cisco was specially designed to serve two purposes. First, it introduces people who are brand new to IT to the subject matter and job expectations they can expect from the career field. Second, it familiarizes newcomers to the world of IT certifications and what's necessary to advance your IT career.
Earning the CCST Cybersecurity puts your feet under you and prepares you for a career troubleshooting and monitoring devices and networks. This course makes sure you understand the concepts and vocabulary you'll hear and need to use on your first day on the job.
For anyone who leads a technology team, this Cisco training can be used to onboard new entry-level cybersecurity professionals, curated into individual or team training plans, or as a Cisco reference resource.
CCST Cybersecurity: What You Need to Know
For any entry-level cybersecurity professional looking to improve their proficiency with cybersecurity, this Cisco course covers topics such as:
- Essential security principles like threats, exploits, and vulnerabilities
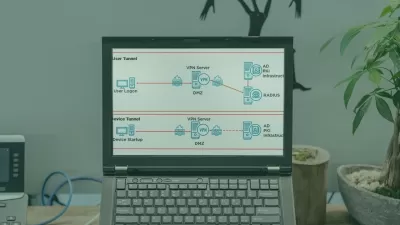
- Fundamentals of network operations
- Endpoint system security concepts related to OS and software
- Vulnerability assessment and risk management basics
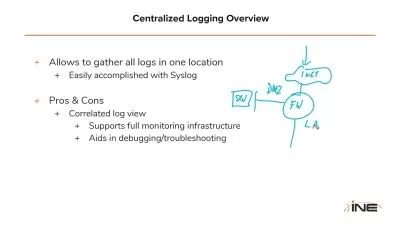
- Responsibilities and expectations around incident handling
Who Should Take CCST Cybersecurity Training?
This CCST training was designed for entry-level cybersecurity professionals. This entry-level cybersecurity concepts and topics skills course is valuable for new IT professionals with at least a year of experience with cybersecurity and experienced entry-level cybersecurity professionals looking to validate their Cisco skills.
New or aspiring entry-level cybersecurity professionals. If you've never held a job in the IT world, or you're very early in your IT career, the CCST certifications will ensure you understand everything about the job, from the technology to the terminology and even to the job responsibilities and expectations. Set yourself up for success with this course that will prepare you for one of your first industry credentials.
Experienced entry-level cybersecurity professionals. If you've got a few years of experience in cybersecurity already, this course and the CCST Cybersecurity will probably be easy, but it's still worth it to take. If you've never taken the time to learn the official, by-the-book terminology and technological concepts that Cisco expects of its entry-level technicians, it's worth setting the foundation early with this course and earning a cert that will solidify your career.
User Reviews
Rating
James Conrad
Instructor's CoursesI really enjoy teaching someone a topic that was difficult for me to learn so they don’t have to go through the same pain that I did while learning that topic.
James brings more than 30 years of IT experience to his training. He got his start in IT volunteering for a nonprofit and becoming their defacto IT pro — while using an MS-DOS portable computer. Before joining CBT Nuggets, James did freelance IT work, and wrote and reviewed technical books. His hobbies include photography, hiking, and traveling, especially to Eastern Europe and Russia.
Certifications: Microsoft Certified Professional, Microsoft Certified Solutions Associate, Microsoft Certified Solutions Expert, Microsoft Certified Technician, Certified Ethical Hacker, and CompTIA A+
Areas of expertise: Microsoft (Group Policy) and CompTIA

CBT Nuggets
View courses CBT Nuggets- language english
- Training sessions 156
- duration 20:49:47
- Release Date 2024/06/25