Cisco Certified Support Technician (CCST): Cybersecurity
Marious Kuriata
5:10:42
Description
An entry point into the Cisco Certified program
What You'll Learn?
- Master the principles of cybersecurity, including vulnerabilities and ethical considerations
- Acquire skills in tools and commands to test your network (Wireshark, CLI, cmd)
- Learn about operating system security, malware removal, and software updates.
- Gain hands-on experience with Cisco, Microsoft, and Linux systems.
- Develop skills in incident handling, digital forensics, and compliance frameworks
Who is this for?
What You Need to Know?
More details
DescriptionAre you looking to kickstart your career in cybersecurity? Our Cisco Certified Support Technician: Cybersecurity (CCST) course is specifically designed for entry-level technicians, students, interns, and IT professionals seeking to delve into the world of network and security. Hands-on experience with Cisco routers, switches, and access points will equip you with the real-world skills needed to protect digital assets. This course is an entry point into the Cisco Certified program. We will explore essential security principles, threats, vulnerabilities, access management principles, encryption methods, basic network security concepts, endpoint security, vulnerability assessment, risk management, incident handling, and more
This course covers:
Essential Security Principles: Grasp the foundations of cybersecurity, including the understanding of vulnerabilities, threats, and ethical considerations.
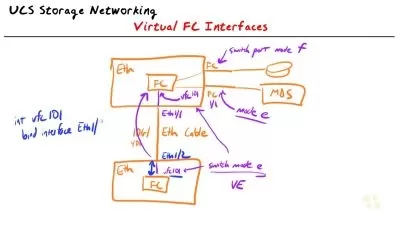
Basic Network Security Concepts: Learn about TCP/IP vulnerabilities, network addresses, and the ins and outs of network security architecture.
Endpoint Security Concepts: Explore operating system security, endpoint tools, system logs interpretation, and malware removal techniques.
Vulnerability Assessment and Risk Management: Discover how to identify and manage vulnerabilities, assess risks, and plan for disaster recovery.
Incident Handling: Develop skills in monitoring security events, understanding digital forensics, compliance frameworks, and cybersecurity incident response.
By the end of this course, participants will be ready to take the Cisco Certified Support Technician: Cybersecurity exam and will be qualified work-ready cybersecurity technicians.
Join now!
Who this course is for:
- Entry-level cybersecurity technicians
- IT students and interns
- IT professionals seeking to expand into cybersecurity
- Individuals aiming for Cisco's CyberOps certification
Are you looking to kickstart your career in cybersecurity? Our Cisco Certified Support Technician: Cybersecurity (CCST) course is specifically designed for entry-level technicians, students, interns, and IT professionals seeking to delve into the world of network and security. Hands-on experience with Cisco routers, switches, and access points will equip you with the real-world skills needed to protect digital assets. This course is an entry point into the Cisco Certified program. We will explore essential security principles, threats, vulnerabilities, access management principles, encryption methods, basic network security concepts, endpoint security, vulnerability assessment, risk management, incident handling, and more
This course covers:
Essential Security Principles: Grasp the foundations of cybersecurity, including the understanding of vulnerabilities, threats, and ethical considerations.
Basic Network Security Concepts: Learn about TCP/IP vulnerabilities, network addresses, and the ins and outs of network security architecture.
Endpoint Security Concepts: Explore operating system security, endpoint tools, system logs interpretation, and malware removal techniques.
Vulnerability Assessment and Risk Management: Discover how to identify and manage vulnerabilities, assess risks, and plan for disaster recovery.
Incident Handling: Develop skills in monitoring security events, understanding digital forensics, compliance frameworks, and cybersecurity incident response.
By the end of this course, participants will be ready to take the Cisco Certified Support Technician: Cybersecurity exam and will be qualified work-ready cybersecurity technicians.
Join now!
Who this course is for:
- Entry-level cybersecurity technicians
- IT students and interns
- IT professionals seeking to expand into cybersecurity
- Individuals aiming for Cisco's CyberOps certification
User Reviews
Rating
Marious Kuriata
Instructor's Courses
Udemy
View courses Udemy- language english
- Training sessions 59
- duration 5:10:42
- English subtitles has
- Release Date 2023/11/14